What Is a Zero-Day Attack?
A zero-day attack leverages a previously unknown vulnerability—one that hasn’t been detected by developers or security experts. Because the vulnerability is unknown, there is typically no existing patch or fix, leaving systems temporarily vulnerable until a solution can be developed and deployed. The term "zero-day" refers to the fact that defenders have "zero days" of warning before the attack hits, making these attacks particularly difficult to stop.
In the realm of email security, zero-day attacks often come through cleverly disguised phishing emails or malicious attachments, which can exploit unknown software vulnerabilities, bypass detection, and deliver malware into an organization’s network. This could lead to devastating outcomes, such as data theft, system hijacking, or ransomware attacks.
How Zero-Day Attacks Are Executed via Email
Zero-day attacks can be executed a number of ways, including:
- Malicious Attachments: Attackers may craft a malicious attachment that exploits a zero-day vulnerability in email clients or document readers. When recipients open the attachment, malware installs itself on the device and begins its damaging process, often without any visual cues or warnings.
- Malicious Links: Sometimes, attackers embed links in emails that lead to compromised websites. The site may exploit a browser vulnerability unknown to the security community, allowing malware to be downloaded onto the victim's device when they visit the site.
- Spear Phishing & Social Engineering: Attackers carefully research their targets and craft emails that appear legitimate and credible. These emails might not even contain any detectable malicious elements, but leverage social engineering tactics to prompt action that inadvertently exposes recipients to zero-day exploits.
How to Prevent Zero-Day Attacks in Email Security
- Advanced Email Threat Protection Solutions: Advanced email threat protection solutions use sophisticated data science, AI, and machine learning to detect unusual patterns in email traffic. These tools often employ behavioral analysis and sandboxing to observe how email attachments and links behave in a controlled environment, identifying potentially malicious activities without directly exposing your network.
- Attachment Protection: Using sandboxing provides a safe, isolated environment where email attachments can be executed and analyzed without risking the broader network at large. This approach allows security teams to observe how attachments behave in a controlled setting, detecting malware or zero-day exploits that might be disguised as innocuous files.
- URL Protection: URL analysis would scan all incoming emails for any suspicious malicious URLs, and thus would prevent zero-day exploits from being executed.
Let's look at recent Q3 data that displays recent trends in zero-day attacks and their delivery, as well as other email threat vectors:
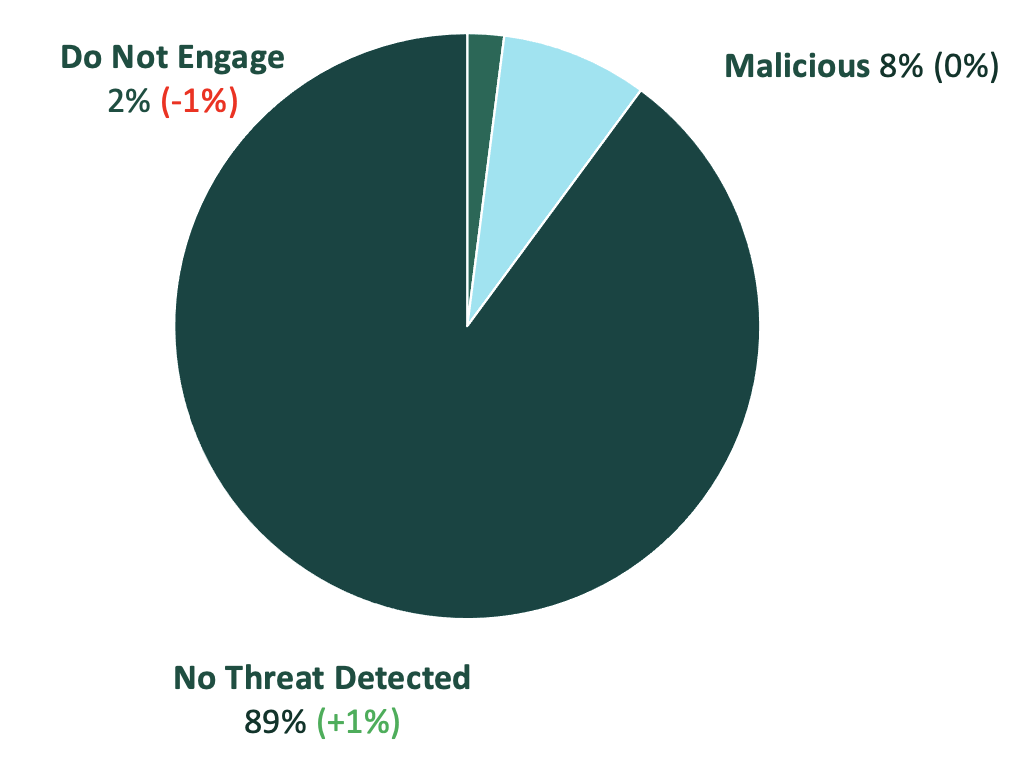
Employee-Reported Emails
- Reported emails containing no threats detected continue to make up the majority of employee-reported emails. Although the number of no threats detected increased by a minor 1%, it has continued to steadily increase across the year. This trend is constant throughout all of 2024 so far.
- Employee-reported emails that are classified as malicious and suspicious (i.e., Do Not Engage) made up 10% of all reported emails. Suspicious emails continued to decline over the past two consecutive quarters.
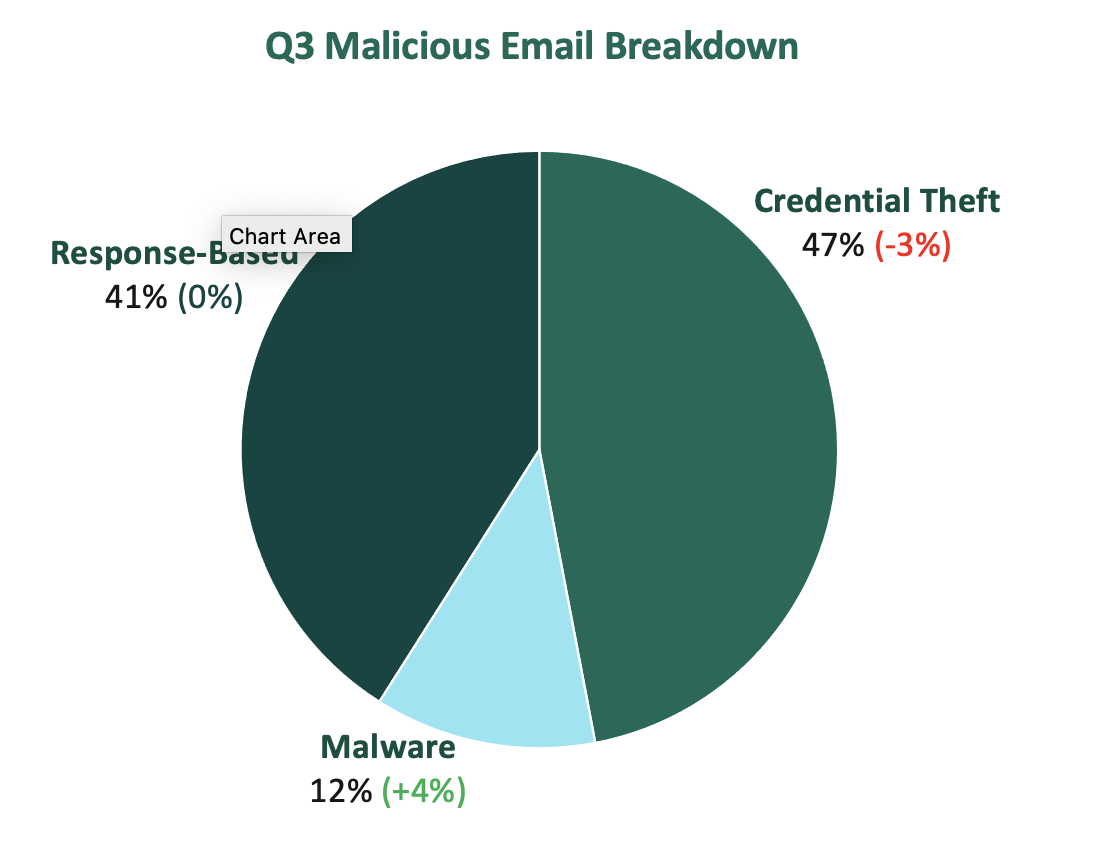
Top Email Threat Categories
- Credential theft made up almost half of all email threats observed in Q3. Although credential theft threats declined by 3% this quarter, they continue to make up most of the email threats recorded in 2024 so far. As of Q3 2024, organizations can expect to encounter credential theft in approximately 50% of all email security threats they handle.
- Malware threats constituted 12% of all reported malicious emails. This is the greatest percentage of malware-containing emails recorded by Fortra since Q1 2024.
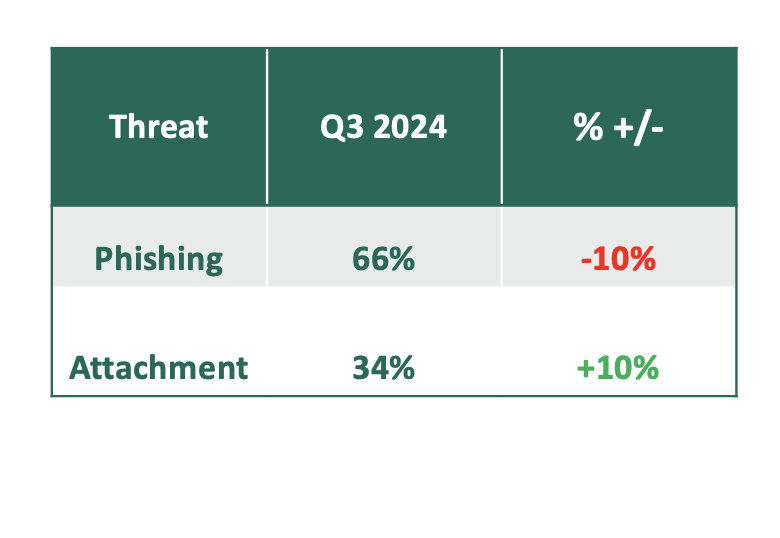
Credential Theft Attacks
- Phishing threats refer to malicious links within emails that point victims to suspicious websites, which made up most of the observed credential theft attacks in Q3, with 66% of reported emails containing a link that redirected to a malicious website.
- Attachment threats refer to emails containing attachments that redirect to malicious websites, otherwise known as Docuphish. These threats constituted just over one third of Q3’s attack volume and grew by 10% as compared to the previous quarter.Image
Response-Based Attacks
- The volume of response-based attacks made up 41% of all observed email threats, placing them as the second most encountered email threat of the quarter.
- 419 scams led the response-based category for the second quarter in a row, outnumbering all the other response-based threat categories.
- Although vishing (or voice-based phishing) and Business Email Compromise (BEC) attacks declined over Q3, they continue to make up a staggering 42% of the response-based attack volume.
Image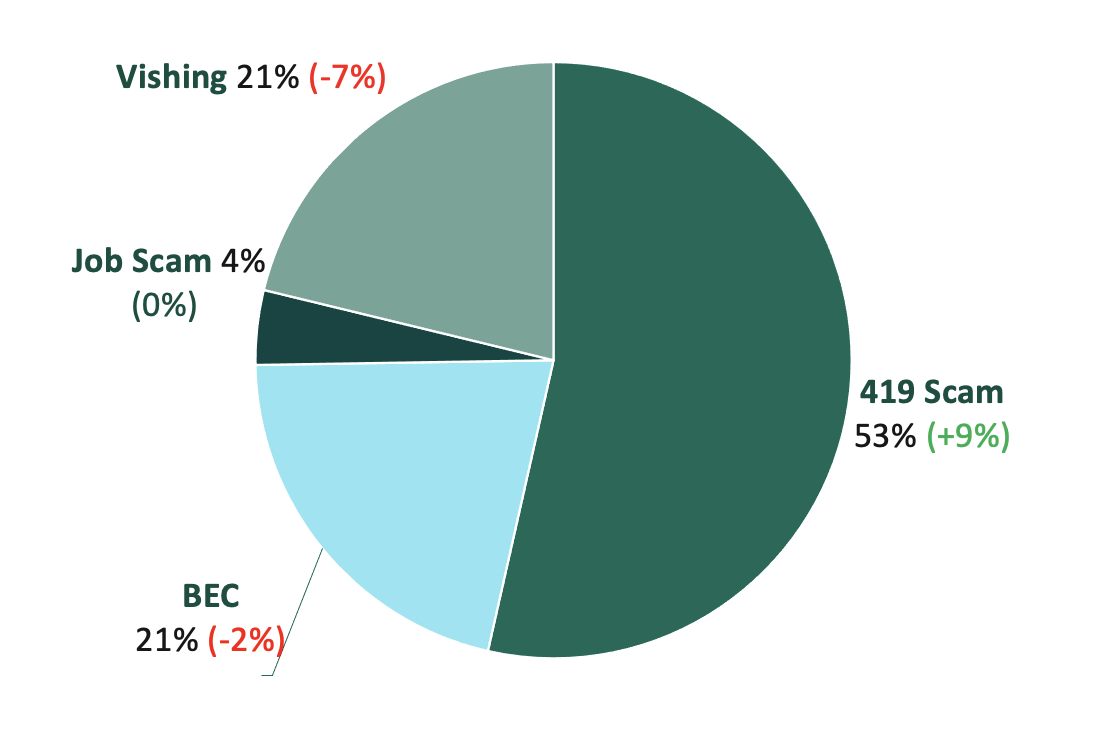
Malware Attacks
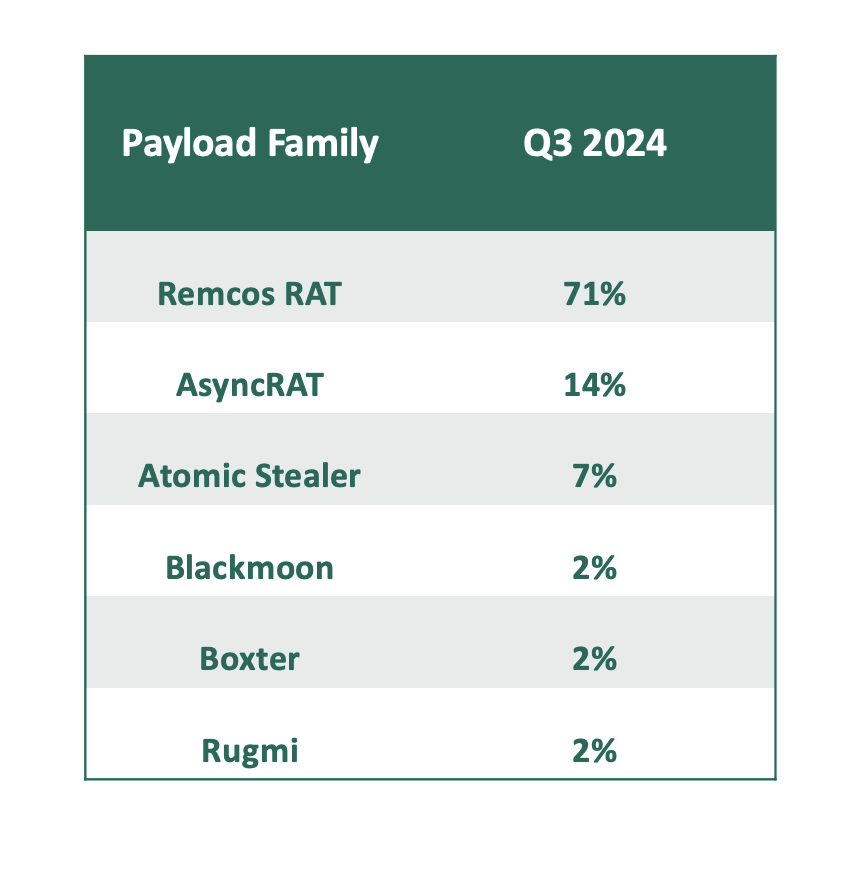
- The most popular malware of choice by threat actors in Q3 were remote access trojans (RATs). Earning their place as the topmost reported malware of Q3, Remcos RATs made up 71% of the payload volume. Remcos is a highly sophisticated remote access trojan used by attackers to gain access to and control of Windows computers from XP and beyond.
- Async RAT, a former open-source remote administration tool that has been weaponized by cybercriminals, came in second – making up 14% of the payload families in Q3.
- Blackmoon, Boxter, and Rugmi all tied at 2% apiece.
Conclusion
Luckily, Fortra's Cloud Email Protection can ward off and detect zero-day attacks like malware and other advanced email threats such as BEC, vishing, and more.
