In Q4, Response-Based phishing attacks were the top reported threat by end users, according to Fortra’s PhishLabs. While threats categorized as Credential Theft and Malware continue to bypass even the top secure email gateways, this is the second consecutive quarter where Response-Based attacks have led all categories. Response-Based attacks typically lack malicious indicators and instead rely solely on social engineering to compromise victims.
Every quarter, PhishLabs analyzes hundreds of thousands of phishing and social media attacks targeting enterprises, brands, and employees. In this post we discuss the types of malicious emails making it into employee inboxes most, using intelligence collected through Fortra's Suspicious Email Analysis solution.
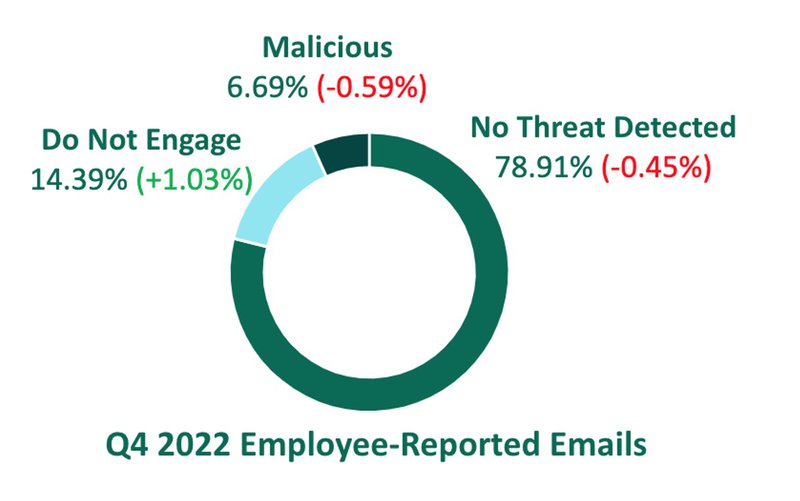
Emails classified as Malicious and Do Not Engage represented more than 21% of all messages reported by employees in Q4. The volume of potentially damaging messages classified by PhishLabs analysts as “Do Not Engage” grew in both count and share over the entirety of 2022. Potential threats qualify as “Do Not Engage” when they lack previously documented malicious indicators.
Malicious Email Breakdown
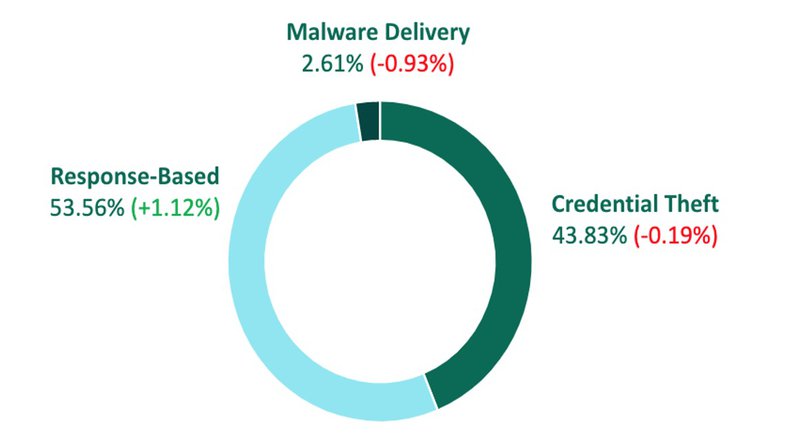
Response-Based Threats
In Q4, Response-Based attacks such as Vishing, 419 Scams, and BEC led the percentage of malicious emails with over half of the total volume. While Response-Based threats have traditionally trailed Credential Theft attacks in both share and volume, this is the second consecutive quarter where malicious emails lacking links or attachments are the top reported threat to employees. Response-Based attacks use social engineering to engage with victims in the attempt to convince them to disclose sensitive information or transfer cash to the criminal.
The increase in Response-Based attacks suggests criminals are finding greater success bypassing secure email gateways through social engineering tactics and identity deception than deploying attacks containing indicators commonly flagged by security controls.
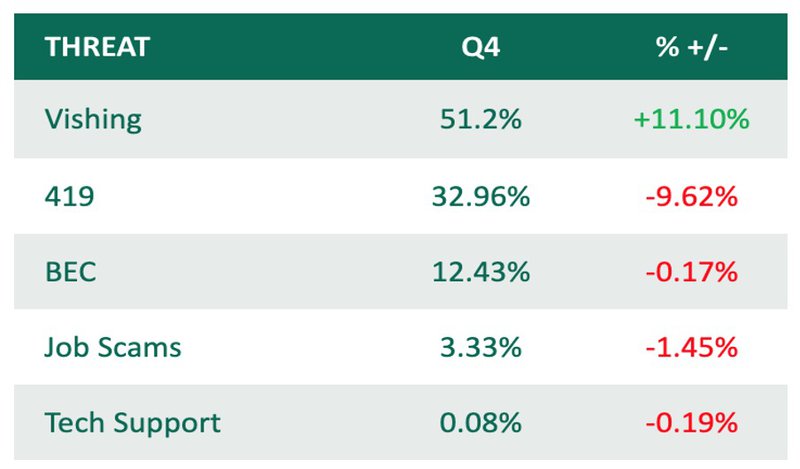
Within the group, hybrid vishing attacks overtook long-time leader 419 Scams (Advanced-Fee Fraud) for the first time since PhishLabs began reporting on the threat-type. Vishing jumped 11.1% in share to represent more than half of all Response-Based threats. Hybrid vishing attacks use a combination of email and phone number within the message body to bypass traditional security controls and trick victims into calling the provided number and disclosing sensitive information to malicious actors.
In Q4, 419 Scams experienced a decline in attacks for the second consecutive quarter, pushing the threat type behind hybrid vishing. Advanced-Fee scams are historically the top tactic for criminals within the Response-Based category due to their ease of creation and delivery. BEC attacks remained steady in Q4, making up 12.43% of share of Response-Based volume.
Job Scams and Tech Support both experienced a decline in share in Q4, contributing to 3.3% and 0.08% of volume, respectively.
Credential Theft Attacks
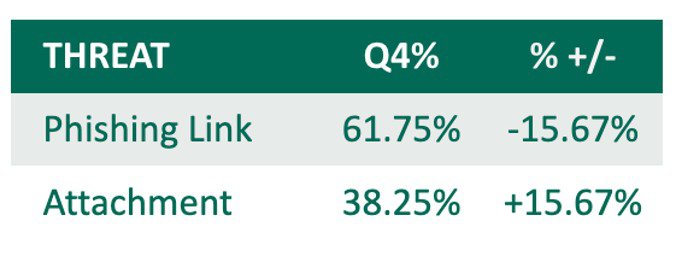
Credential Theft attacks declined slightly in Q4, contributing to 43.8% of reported malicious emails. Phishing links made up 61.75% of Credential Theft volume, despite declining more than 15% from Q3.
Within the Phishing link group, the share of M365 phish dropped as well, declining nearly 20% over Q3. This is the most significant decline in M365 phishing attacks since 2020, suggesting security teams and implemented security controls are getting better at identifying malicious messages impersonating Microsoft tools and products.
Attachments containing links that redirect to phishing sites, otherwise known as Docuphish, increased in Q4, owning 38.25% of share. Docuphish counts have increased for two consecutive quarters.
Malware
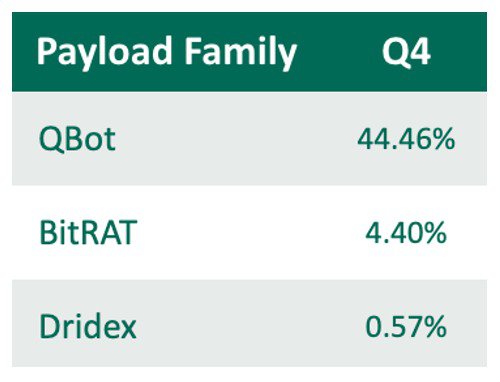
QBot was the favorite malware variety among bad actors in Q4, making up nearly 95% of all malware reported. While QBot is consistently among the top payload families, this represents a more than 60% increase in share of overall volume from Q3.
Remote access trojan BitRAT was the second most reported payload in Q4, contributing to 4.40% of share. Although BitRAT has only been around since 2021, it stood among the top ten payload varieties for three quarters of 2022.
Russian-linked Dridex rounded out the top three, with less than one percent of volume in Q4.
Criminals continue to infiltrate networks with malicious messages and software, tricking victims into disclosing sensitive information or allowing access into secure spaces. More often, these messages are straying from links and attachments, instead relying on convincing content to perform their attacks. In order to prevent these attacks, organizations should invest in security capabilities that thoroughly inspect the domain, content, and other indicators within a suspicious email that could reveal malicious activity.
Learn how you can protect against advanced email threats with Fortra's Suspicious Email Analysis.