Why would a cybercriminal spend time developing malware when he can simply trick unsuspecting users into handing over their passwords? Why would a threat actor spend her money and resources on ransomware, when she can get that same information through a compromised account? It’s a good question, and exactly what the Fortra Cyber Intelligence Team, Fortra's group of threat hunters, wanted to discover.
In a growing trend known as credential phishing, threat actors impersonate legitimate brands and services by crafting similar-looking websites where unsuspecting users enter their account information. Once entered, account details are forwarded to the cybercriminals, completely bypassing malware detection software. From there, those criminals can do what they want—often for years and without being detected. And now with enterprise migration toward cloud-based email and services, credential phishing is more popular than ever.
In order to better understand the problem, we seeded over 8,000 phishing sites with credentials under our control and then monitored these accounts to directly observe the actions taken by a cybercriminal post-compromise. The results were astounding.
Our research showed that nearly a quarter of compromised accounts were automatically accessed at the time of compromise to validate the authenticity of the credentials. And regardless of whether credentials were automatically validated, nearly all of the compromised accounts (92%) were accessed manually by a threat actor.
Almost one in five accounts were accessed within the first hour post compromise, and nearly all of them were accessed within a week after they were compromised. And while a majority of compromised accounts were only accessed one time by actors, we observed a number of examples where a cybercriminal maintained persistent and continuous access to a compromised account.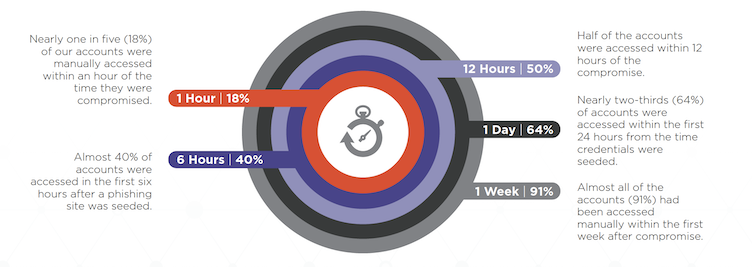
We traced threat actors accessing compromised accounts to 44 countries around the world. Mirroring the findings in our Geography of BEC video, Nigeria was far and away the top location for individuals accessing compromised accounts, which supports the link between response-based BEC attacks and credential phishing BEC attacks. The United States was the second-most common location for mailbox hackers, followed by South Africa, the United Arab Emirates, the United Kingdom, and Turkey.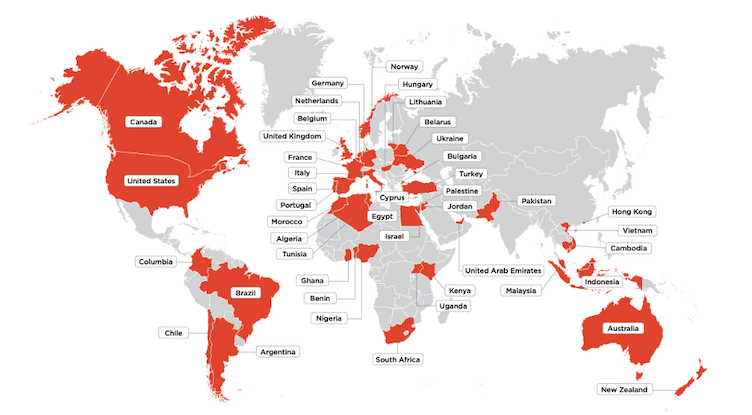
The most important part of our research directly observed how cybercriminals exploit a compromised account. In fact, we saw scammers create forwarding rules; pivot to other applications, including Microsoft OneDrive and Microsoft Teams; attempt to send outgoing phishing emails, sometimes by the thousands; and use the accounts to set up additional BEC infrastructure.
We hope this research provides an in-depth first look at how destructive credential phishing attacks can be, and demonstrates why these less technically sophisticated cyber attacks continue to increase in popularity.
Read the Anatomy of a Compromised Account for further details on how compromised accounts are used, and how they contribute to additional BEC scams.
Inside a Compromised Account: How Cybercriminals Use Credential Phishing to Further BEC Scams
Posted on June 7, 2021