What is Email Spoofing?
Email spoofing is the forgery of an email sender address so that the message appears to have come from someone other than the actual source. Spammers will often spoof emails in order to encourage recipients to open, reply to, or even take action in response to their solicitations.
Email spoofing is one of the most common forms of cybercriminal activity, specifically a form of identity deception that's widely used in phishing and spam attacks. It underpins the mechanism required to conduct hacking activities, and it can take many forms. Unfortunately, most email users will eventually receive an email that has been spoofed—whether they know it or not.
And while brand spoofing is common, we are increasingly seeing criminal activities where individuals are spoofed to target employees and partners.
Examples of Email Spoofing
Some of the most prevalent forms of email spoofing are:
- Business email compromise, such as executive spoofing or display name deception
- Legitimate domain or lookalike domain spoofing
- Spear phishing, including social engineering, like this real example of a mortgage company targeting the recipient to download documents on a fake site:
Example of Email Spoofing Using Display Name Deception
Display name deception is the most common form of email spoofing and is often successful because many email clients (especially on mobile devices) show only the display name. With this kind of attack, criminals can insert the identity of a trusted individual (such as the name of an executive at the targeted company) or a trusted brand (such as the name of the bank used by the targeted individual) into the display name.
Since common consumer mailbox services, such as Gmail and Yahoo, allow a user to specify any value in the display name, this type of attack is simple and cheap to stage from such a service. Here is an example of a brand display name imposter below:
Example of Email Spoofing Using Legitimate Domains
In addition to manipulating the display name, an attacker may also use the actual email address of the impersonated identity in the From header, such as “United Customer Service” <[email protected]>. This type of attack, known as domain spoofing, does not require compromising the account or the servers of the impersonated identity, but exploits the security holes in the underlying email protocols. Attackers often use public cloud infrastructure or third-party email sending services that do not verify domain ownership to send such attacks.
Email authentication standards, such as DMARC, can be used by a domain owner to prevent spoofing of their domain, but have still not been adopted widely by many retail companies, Fortune 500 businesses, and government organizations. And according to Agari's 2022 Email Fraud & Identity Deception Trends report, email spoofing and phishing increased by a whopping 220% over 2021.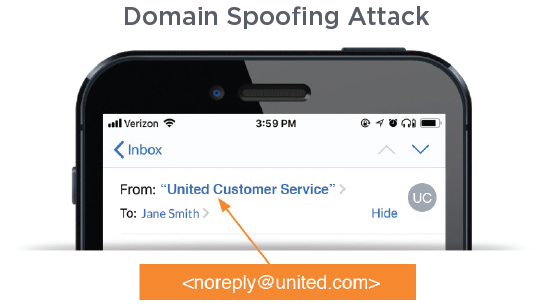
PhishLabs' Quarterly Threat Trends & Intelligence 2022 report reinforced the fact that impersonations continue to plague enterprises via advanced email attacks, lookalike domains, credential theft scams and other forms of phishing to commit brand abuse or fraud. Year after year, the proof of spoofing's efficacy is staggering. For example in addition to email spoofing, brand and executive impersonation made up the bulk share of social media attacks coming in at nearly 41% in Q2, with fraud coming in second at around 40% (over 5% from Q1).
Example of Email Spoofing Using Lookalike Domains
In cases where a domain is protected by email authentication and domain spoofing is not possible, attackers try to deceive the recipient by registering and using domains that are similar to the impersonated domain. These types of attacks, known as lookalike domain attacks, often use homoglyphs or characters that appear similar to the original characters in the impersonated domain. Attackers can use rendering similarities, such as “PayPal” <[email protected]>, exploiting the specific fonts and rendering styles used in popular email clients. Another variation of the lookalike domain attack is to add additional words to the domain name.
For example, if an attacker wanted to send you a bogus invoice from Acme Corporation, whose domain might be acme.com, the attacker could simply register acme-payments.com or invoices-acme.com. Finally, attackers can use characters from another script in the Unicode set. Cyrillic is a common choice, as in the 'From' header “Dropbox” <notifications@ dropbox.com>, where the “o”s in the domain are actually Cyrillic characters, but an email client will render the version that looks exactly like the impersonated domain.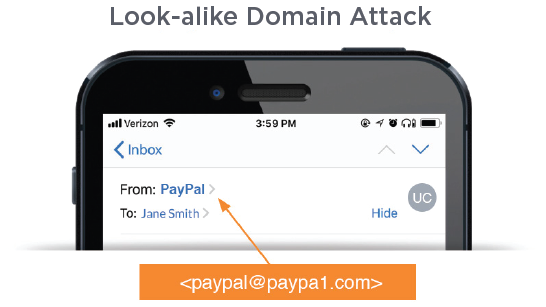
Example of Spoofing Using BEC
Throughout the past few years, there has been an increase in business email compromise attacks, which typically spoof CEOs' and CFOs' email addresses to initiate wire transfers, request small-dollar gift cards for charity events, or reward staff for their work. In these cases, the email is typically coming from an executive at the organization and is directed to either an executive assistant or to junior employees in his or her department.

How to Prevent Email Spoofing
While it is not possible to prevent cybercriminals from spoofing email addresses (as they continuously find new ways to trick their targets), it is possible to block these messages before they reach the inboxes of your employees, customers, and partners.
A combination of email authentication protocols (SPF, DKIM and DMARC) and identity detection methods (i.e., brand and executive impersonation) can help ensure that spoofed emails are detected before they ever reach the inbox. Additionally, supplementing with ongoing security awareness training to help spot attacks can help build a comprehensive strategy that ensures that intended targets stay safe from brand impersonation, identity deception, and email spoofing, ultimately helping you restore trust to the inbox.
Email Spoofing Vs. Phishing
Fortra delivers comprehensive advanced threat protection and powerful policy enforcement for cloud, on-prem, and hybrid environments. With our solution suite, enterprises can tackle their toughest email security challenges including BEC, advanced threats, and data leaks.
Get started first with DMARC email authentication.
Everything you need to know about getting started with DMARC!