Within Fortra's Threat Intelligence service, we regularly engage with BEC threat actors using active defense techniques. Recently, during one of our investigations into a group comprised of these threat actors, we observed several scammers taking advantage of a “feature” that Google has built into Gmail addresses. While Google sees this as an advantage of consumers, cybercriminals are exploiting it for malicious activities.
Taking Advantage of Dot Accounts
By utilizing this Gmail account feature—which we will call Gmail “dot accounts”—these threat actors are able to scale their operations by opening multiple fraudulent credit card accounts, which they then use to file for fraudulent unemployment benefits, file fake tax returns, and bypass trial periods for online information providers. In one case, a scammer was able to submit twenty-two separate applications, each under a different identity, and successfully open over $65,000 in fraudulent credit cards at a single financial institution.
Here’s how they did it.
Let’s assume I create a Gmail account with the email address bad.guy007[at]gmail.com. Visually, it looks like the username “bad.guy007” is separated by a period. According to Google, however, “you own all dotted versions of your address.” This means that Google interprets the email address I created as badguy007[at]gmail.com, stripping out the period, and the same can be said if the dot was placed in any other place in the email address. In other words, this interpretation is a feature, not a bug. This also means that b.a.d.g.u.y.007[at]gmail.com and bad.guy.007[at]gmail.com and ba.dg.uy.007[at]gmail.com all direct incoming email to the same account.
Scaling Scam
Warnings about the dangers associated with this feature have previously been published by other researchers. While all dot variants of Google Gmail dot accounts direct all email to the same inbox, a vast majority of the rest of the Internet treats each variant as a distinctly separate email address, associated with a unique separate account and identity. For example, if I sign up for a Netflix account using the email address badguy007[at]gmail.com and then again with b.adg.uy007[at]gmail.com, Netflix—like most other online services—would think that these are two different accounts linked to two different people. This is where, and how, cybercriminals are able to take advantage.
By exploiting this feature in Gmail accounts, scammers are able to scale their operations more efficiently, creating dozens of accounts on a single website that then direct all communication to a single Gmail account. This removes the need to create and monitor a new email account for every account they create on a website, ultimately making crimes faster and more efficient.
Recently, we observed a group of BEC actors make extensive use of Gmail dot accounts to commit a large and diverse amount of fraud. Since early 2018, this group has used this fairly simple tactic to facilitate the following fraudulent activities:
- Submit 48 credit card applications at four US-based financial institutions, resulting in the approval of at least $65,000 in fraudulent credit
- Register for 14 trial accounts with a commercial sales leads service to collect targeting data for BEC attacks
- File 13 fraudulent tax returns with an online tax filing service
- Submit 12 change of address requests with the US Postal Service
- Submit 11 fraudulent Social Security benefit applications
- Apply for unemployment benefits under nine identities in a large US state
- Submit applications for FEMA disaster assistance under three identities
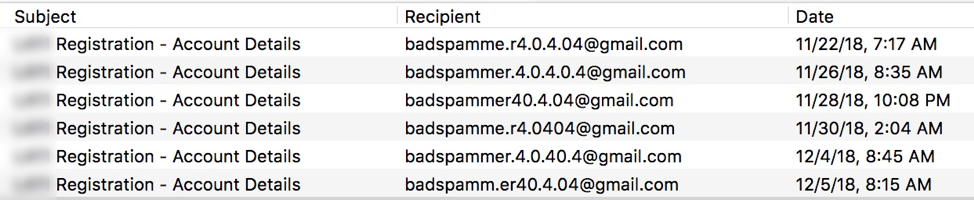
Google Dot Accounts Used to Create Trial Accounts on a Commercial Sales Lead Service
Note: Actual Email Address Changed
In each case, the scammers created multiple accounts on each website within a short period of time, modifying the placement of periods in the email address for each account. Each of these accounts is associated with a different stolen identity, but all email from these services are received by the same Gmail account. Thus, the group is able to centralize and organize their fraudulent activity around a small set of email accounts, thereby increasing productivity and making it easier to continue their fraudulent behavior.
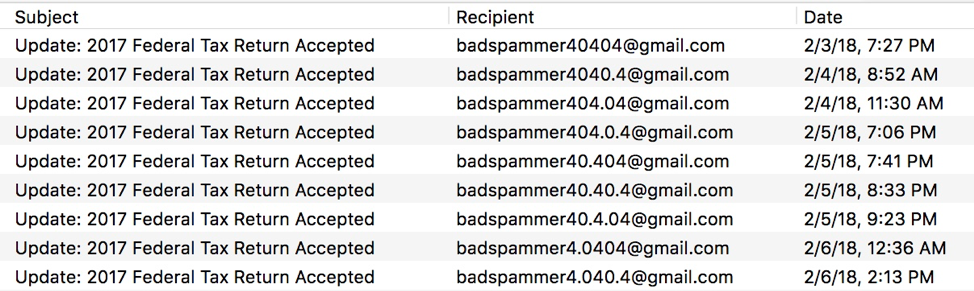
Google Dot Accounts Used to File Fraudulent Tax Returns
In total, the group used 56 different dot variants of a single Gmail email address to register accounts on websites used for fraudulent purposes.
To make matters worse, the “features” of Gmail are not contained to simply ignoring periods. Email accounts ending in @googlemail.com are also routed to the same inbox as those that end in @gmail.com. Thus, emails sent to badguy007[at]gmail.com and badguy007[at]googlemail.com all end up in the same inbox. While we have not yet observed scammers using the googlemail.com domain to mass-create online accounts that all point to the same mailbox, the potential for exploiting this feature for malicious purposes remains the same.
Searching for instances of excessive dots in newly created accounts is one way online services can identify potential instances of abusive activity, where threat actors use variants of Gmail dot accounts for fraudulent or nefarious activity.