Editor's Note: This post originally appeared on the Microsoft Security blog and has been republished here.
You already know that email is the number one attack vector for cybercriminals. But what you might not know is that without a standard email security protocol called Domain Message Authentication, Reporting, and Conformance (DMARC), your organization is open to the phishing attacks that target your customers, crater your email deliverability rates, and crush your email-based revenue streams.
For all the utility of email, which remains the ultimate app for business collaboration and communication, it does have a serious flaw: the ability for a bad actor to pretend to be someone else in an email message. This can be done through one of two attack techniques, spoofing and impersonation. Spoofing is when the sender is attempting to send mail from, or on behalf of, the exact target domain. Impersonation is when the sender if attempting to send mail that is a lookalike, or visually similar, to a targeted domain, targeted user, or targeted brand. When cybercriminals hijack your brand identity, especially your legitimate domains, the phishing attacks they launch against your customers, marketing prospects, and other businesses and consumers can be catastrophic for them—
Email-based brand spoofing and impersonations surged 250 percent in 2018, with consumers now losing $172 billion to these and other internet scams on an annual basis. More than 90 percent of businesses have been hit by such impersonations, with average losses from successful attacks now standing at $2 million—
DMARC can help you take control of who can send email messages on your behalf, eliminating the ability for cybercriminals to use your domain to send their illegitimate messages. In addition to blocking fake messages from reaching customers, it helps prevent your business-to-business customers from partner invoice scams like the kind that recently defrauded one large, publicly-traded business that lost $45 million. Not a good look for your brand, and a sure way to lose your customers, partners, and brand reputation.
But to protect your corporate domains and prevent executive spoofing of your employees, DMARC must be implemented properly across all your domains and subdomains. And you’ll want your supply chain to do the same to protect your company and partners from such scams. Today, 50 percent of attacks involve “island hopping,” spoofing or impersonating one trusted organization to attack another within the same business ecosystem.
Great, but What Exactly is DMARC?
For those not yet familiar with the term, DMARC acts as the policy layer for email authentication technologies already widely in use—
At its most essential, DMARC gives organizations control over who is allowed to send emails on their behalf. It allows email receiver systems to recognize when an email is not coming from a specific brand’s approved domains—
Today, 57 percent of consumer email in industries such as healthcare and retail are now fraudulent. Consumer-focused brand impersonations are up 11 times in the last five years, 80 percent involving email. In 2018, the IC3 received 20,373 BEC/E-mail Account Compromise (EAC) complaints with adjusted losses of over $1.2 billion. Those attacks target your accounting, payroll, and HR departments, so your outbound marketing programs can become toxic to recipients, obliterating your outbound email programs and the revenue they generate.
Microsoft Support for Email Authentication and DMARC
As the vast majority of businesses continue to migrate to capable and robust cloud platforms such as Office 365, a new generation of cybercriminal organizations is rapidly innovating its methods to find nefarious new ways to circumvent the considerable security controls built into these platforms. Unfortunately, some organizations may not realize that they should fully implement DMARC to augment the security benefit of Office 365 email authentication.
Microsoft has implemented support for DMARC across all of its email platforms. This means that when someone sends an email to a Microsoft mailbox on a domain that has published a DMARC record with the reject policy, it will only deliver authenticated email to the mailbox, eliminating spoofing of email domains.
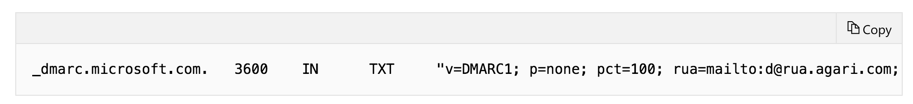
If you use Office 365 but aren’t utilizing custom domains, i.e. you use onmicrosoft.com, you don’t need to do anything else to configure or implement DMARC for your organization. But if you have custom domains, or you’re using on-premises Exchange servers, in addition to Office 365, you’ll need to implement DMARC for outbound mail. All of which is straightforward but implementing it across your entire email ecosystem requires some strategy. To ensure your corporate domains are protected, you’ll need to first publish a DMARC record in DNS with a policy of reject. Microsoft uses Agari’s DMARC reporting tool to enhance protection of Microsoft domains from being used in phishing attacks.
Read more about how Microsoft uses Agari to protect its domain and how that is used to validate email in Office 365 in this Microsoft documentation.
The Rise of Automated, Hosted Email Authentication
The truth is, properly implementing DMARC means you need to identify every single one of your domains and subdomains, across all business units and outside partners—
The task of identifying and onboarding thousands of domains controlled by multiple business units, outside agencies, and other external partners, both on Office 365 and off, can be daunting. As a result, many organizations may discover that working with a DMARC provider that can fully automate the implementation process across all these parties plus supply channel partners is their best chance for success. This is especially true for those that offer fully hosted email authentication (DMARC, SPF, and DKIM) to simplify the otherwise tedious and time-consuming process involved with preventing brand impersonations—
3 Steps to Getting Started with DMARC
The good news is that DMARC is supported by 2.5 billion email inboxes worldwide, and more are joining these ranks every day. But unfortunately, even among organizations with DMARC records assigned to their domains, few have them set to p=reject enforcement. As it stands now, nearly 90 percent of Fortune 500 businesses remain unprotected against email-based spoofing attacks, putting their customers, partners, and other businesses at risk for phishing.
When DMARC is implemented using email ecosystem management solutions, organizations have seen phishing emails sent by fraudsters seeking to spoof them drop to near zero. According to Forrester Research, organizations have also seen email conversion rates climb on average 10 percent, leading to an average $4 million boost in revenues thanks to increased email engagement.
While it’s no small task, there are three steps that will help you move forward with DMARC and get started:
- Create a new DMARC record with specific policies to protect your organization from spoofing attacks targeting your employees, customers, prospects, and more. Note that the policy must be a p=reject to prevent unauthorized mail from being received.
- Download Getting Started with DMARC, a special guide designed to provide an overview of DMARC and best practice resources.
- Schedule a demo and see how Agari can help implement DMARC at your organization. As a member of the Microsoft Intelligent Security Association (MISA), and provider of DMARC implementation for more domains than any other provider, Agari offers a free trial to Office 365 users looking to protect their customers, employees, and partners from phishing-based brand spoofing attacks. Given the threat from impersonation scams, and the benefits that come from employing the right approaches to reducing it, don’t be surprised if DMARC-based email authentication jumps to the top of the to-do list for a growing number of businesses. With luck, brand imposters will never know what hit them.
Bookmark the Microsoft Security blog to keep up with expert coverage on security matters, and subscribe to the Agari blog for more content.