Wondering how DMARC affects email? Here’s a comprehensive guide explaining what DMARC is, how it affects email, and why your company needs it for security.
What is DMARC?
What does DMARC mean? DMARC, short for Domain-based Message Authentication, Reporting and Conformance, is an email authentication protocol to help email administrators prevent fraudsters from spoofing email domains by specifying whether spoofed emails should be allowed, quarantined, or rejected by recipients.
DMARC is an open email standard created by the industry consortium DMARC.org that prevents malicious emails that impersonate other people and works to protect your email in conjunction with well-known email standards SPF and DKIM. These two separate records ensure the authenticity of the sender, as well as the validity of the email. Configuring emails to pass DMARC is the only way for email senders to tell email receivers that the emails sent from their domain are actually from them.
Simply put, DMARC acts as a gatekeeper to a receiving email server. When an email arrives from your sending domain and it isn't verified with SPF or DKIM, you can use DMARC to tell the receiver to reject, monitor, or quarantine the message. DMARC isn’t mandatory, but most modern email servers are now using it, which means if your email server isn’t configured correctly, your emails could be getting sent to spam.
Using DMARC as part of your email best practices can:
- Authenticate all legitimate email messages and sources for email-sending domains, including owned and third-party domains.
- Publish an explicit policy that instructs mailbox providers how to deliver or dispose of messages that are determined to be inauthentic.
- Gain intelligence on all use of their domains in email messages from across the Internet.
Now that you know the basics, let’s dive into some of the most common questions around DMARC.
Are there other benefits to using DMARC?
There are some additional benefits to using DMARC on your email server, other than just security. Government organizations and many of the most respected brands in the world have adopted DMARC, which allows them to:
- Gain visibility into their email channel to determine the legitimate and fraudulent use of their domains.
- Ensure legitimate email is getting delivered and fraudulent email is not.
- Receive alerts when changes to email infrastructure may impact the delivery of legitimate messages.
- Identify sources and forms of threat so that they’re equipped to proactively prevent attacks.
- Improve their overall email reputation score and trustworthiness.
All of this is important, especially for those companies that send millions or even billions of emails each year.
How do I know if I have DMARC for my email?
You can check to see if you have a DMARC email policy in place by looking for a TXT record in your DNS server that begins with “v=DMARC”. Alternatively, you can use the DMARC Setup Tool to check your domain for you.
And if you need to see whether your domain has a DKIM or SPF record, there’s a tool for that too! Check out the DKIM Setup Tool and the SPF Setup Tool for additional details.
Where are DMARC records stored?
DMARC records are stored on the DNS server that your email server uses. Within your DNS server, you can create and modify DMARC, SPF and DKIM records to secure your mail server. Below is a quick overview of the types of policies you might see in your DNS server, and what they do.
- DMARC: Stops spoofing by ensuring inbound mail has SPF and/or DKIM present within the email headers.
- SPF: Sender Policy Framework (SPF) is a form of email authentication used to prevent spoofing that ensures emails being sent with your domain only originate from specific IP addresses.
- DKIM: DomainKeys Identified Mail, which accomplishes the same goal as SPF, uses cryptography to ensure the emails you send are not modified in transit, and also combats email spoofing.
What does a DMARC record look like?
Inside your DNS server, a DMARC email policy will exist as a text record, commonly abbreviated as “TXT”. Below is an example showing what the record would look like. Keep in mind, records can look slightly different depending on how they are configured.
“v=DMARC1;p=quarantine;pct=100;rua=mailto:[email protected]”
The above policy moves all emails that are not secure into quarantine 100% of the time and provides a report to the postmaster.
When configuring your DMARC email policy, you can customize exactly how you want it to treat email traffic using DMARC tags. See the table below for of some of the most commonly used DMARC configuration tags.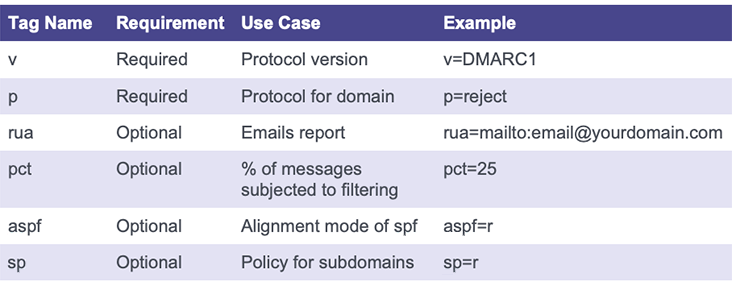
While those are just a few of the most common tags, there are many more tags you can use to get even more specific with your DMARC configuration.
If you’re looking to keep it simple, the only tags you must specify are your version and policy.
What are the options for DMARC policies?
There are three main DMARC policies that determine what happens to email traffic that fails the DMARC check.
- p=reject refuses to accept email that fails the DMARC check. The non-compliant email is dropped, and the sender receives a bounce-back message detailing the reason for the failure.
- p=quarantine accepts emails that violates the DMARC check, but marks them as spam. This is typically usually done by moving the email in a spam folder, or tagging the subject line with a warning.
- p=none does not impact the flow of email, and is used to monitor which emails are passing or failing the DKIM check. While this policy can help gauge how effective your current policies are, and shape how you implement future email security rules, it does nothing to protect your domain.
What doesn’t DMARC do?
DMARC may protect against spoofing, but it doesn’t protect against all forms of email threats. Having DMARC in place does not protect against malicious attachments or links in emails, or from emails that are not coming from your domain.
A simple DMARC email policy also doesn’t protect against cousin domain attacks. Simply put, cousin domain attacks register domains that look very similar to real companies in hopes of tricking recipients into clicking malicious emails. Here’s an example.
[email protected]: Here we see this email is coming from the real company, Microsoft.
[email protected]: At first glance, it may look the same, but attackers registered “micosoft” to trick users into trusting malicious emails.
Since these attacks rely on tricking the recipient, rather than spoofing a real company, a DMARC email policy alone will not stop these attacks.
However, Agari DMARC Protection works to stop spoofing attacks by rapidly identifying and securing lookalike and cousin domains, while working with name server authorities to take down malicious domain names that already exist.
How do I implement DMARC?
Implementing proper DMARC isn’t hard once you have a firm understanding of what it does and how it works. We’ve covered the DMARC setup process in depth, but here is an overview on how it’s done.
- Use the DMARC Setup Tool to easily create the required TXT record.
- After choosing your DMARC policy, copy the DMARC rule that the Setup Tool created.
- Log into the management console of your DNS hosting provider, and add a new TXT record.
If you need additional resources, feel free to reach out to our team. Enterprise clients may find it useful to use a product like Agari DMARC Protection to help automate the implementation work.
Want to learn more about DMARC? Check out our blog post on 5 Big Myths about DMARC, Debunked. The facts may surprise you!
