Have you ever received a blank email from someone you don’t know? If you have, it may have been from a cybercriminal making sure your email account is legitimate prior to a Business Email Compromise (BEC) attack. Agari and PhishLabs define BEC as any response-based spear phishing attack involving the impersonation of a trusted party to trick victims into making an unauthorized financial transaction or send sensitive materials. And BEC attacks continue to show no signs of slowing down—research from Agari shows that BEC remains to be one of the primary attack vectors into an organization, and PhishLabs' Quarterly Threat Trends and Intelligence August report, BEC increased again in Q2, contributing to 16.3% of total attack volume.
We at Agari released a 2020 report on global BEC cybercriminal groups, including London Blue, which dove into the organizational structure of West African criminal groups and described how they operate like modern corporations. In fact, the London Blue operative made the foolish decision to send a BEC email to Agari's CFO (for a second time!), which provided us significant visibility into their operations and thus, an opportunity to observe the group’s entire attack chain—from preparation to execution.
BEC Attack Chain
The second step in this attack chain is “Lead Validation and Processing,” during which a BEC group member takes the raw leads gathered by another member and takes the following steps:
- Validates the contact information to confirm that it is accurate
- Supplements the leads with open-source intelligence to identify additional information, such as the name of the CEO to be impersonated
- Organizes the leads in a way that will allow the scammer sending the BEC emails to be more efficient.
The first part of this step—validation—is integral because it gives the BEC scammer confidence that his attacks are being directed to a live mailbox. So how do the scammers actually validate these potential target email addresses?
Taking the Easy Way Out
Many BEC groups use legitimate commercial lead generation services that are also used by companies all over the world to identify sales prospects, which we discussed first in London Blue and again in a threat dossier on cybercriminal group Scarlet Widow. Once a scammer conducts a customized search for corporate employees meeting their specific criteria, the service will provide a spreadsheet with target information, and even indicate whether their company has previously verified the email address.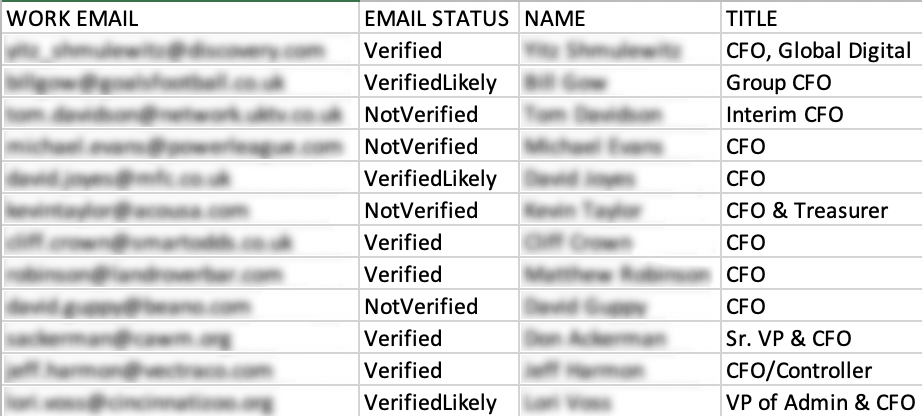
Example Results from Lead Generation Service
Some scammers, though, use a more hands-on approach to validating target email addresses. During our research into a Nigerian BEC organization we’ve named Curious Orca, we uncovered a more monotonous and manual process some scammers use to verify target contact information prior to initiating BEC campaigns.
Using the "i" to Validate Email Targets
The validation process used by Curious Orca is very rudimentary and straightforward. First, a group member starts with a list of raw targeting leads containing the names and possible email addresses of employees with the title “Controller” or “Accountant.” All of the targets processed by this group have these titles, which is a common tactic employed by BEC groups to identify targets. London Blue, for example, specifically looked for employees with “CFO” in their title.
Using this raw targeting list, Curious Orca attempted to validate any unvalidated email address on the spreadsheet by simply sending a probing blank email with the subject “i” to the target to see if the email is delivered successfully. Unlike the emails for BEC campaigns, which are usually sent during work hours in the morning, these validation emails are sent during non-working hours, often in the middle of the night, when targets are unlikely to immediately see the email.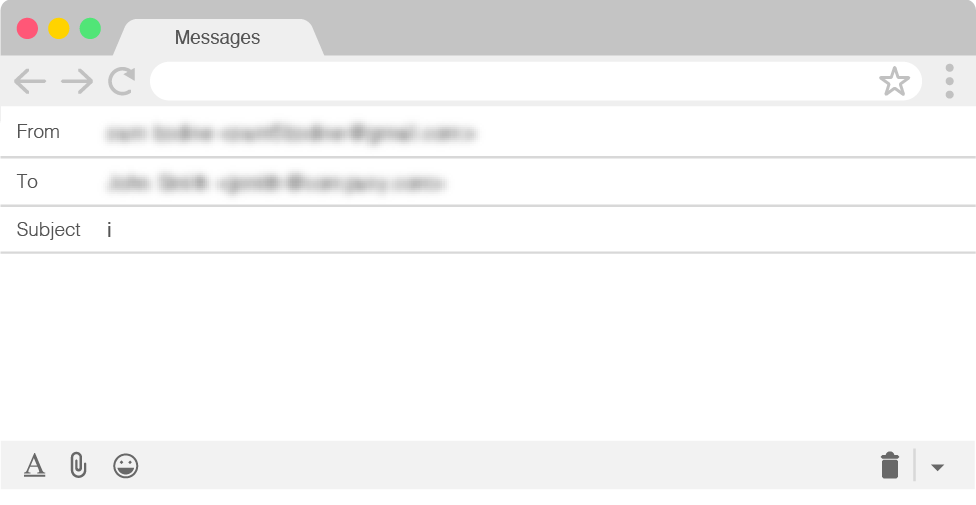
Curious Orca Probe Email
After sending this reconnaissance email, Curious Orca waited to see if an automated “bounce” is sent from the target’s mail server, which would indicate the email address is not valid. Usually, these emails come in the form of an “Undeliverable” or “Delivery Status Notification” message.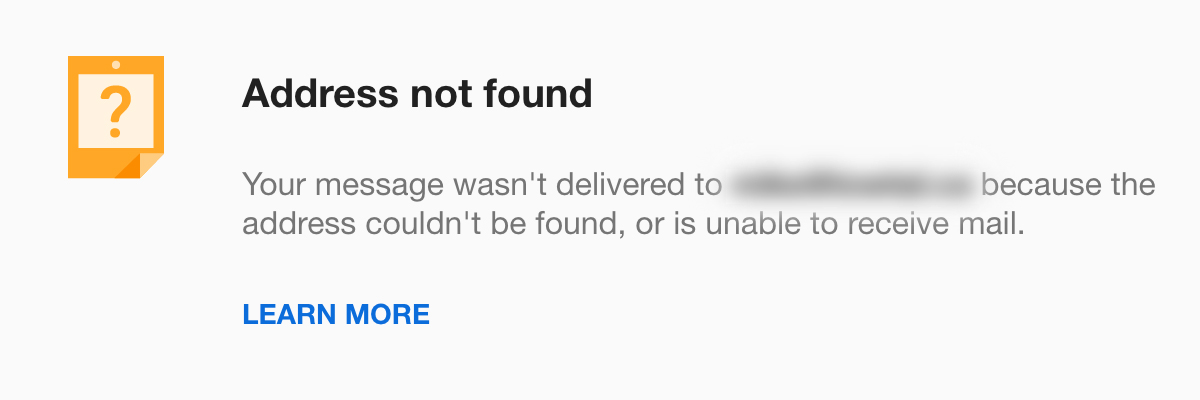
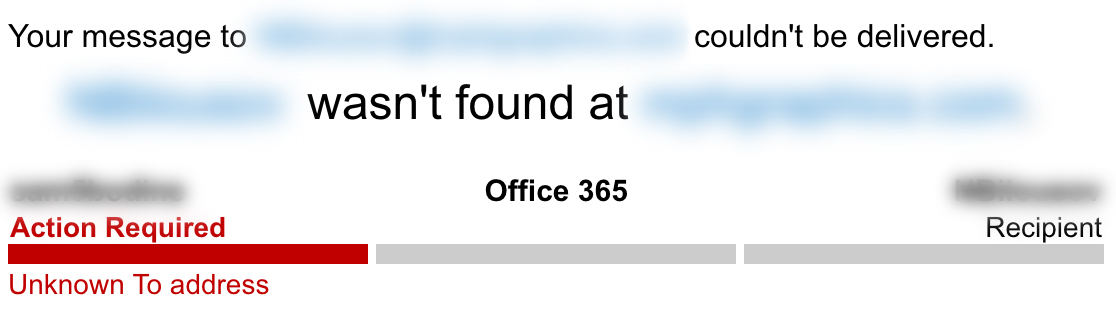

Examples of Email Bounce Notifications
If no bounce notification is received, the target’s email address is assumed to be valid and operational. In the case of Curious Orca, once this contact information has been validated, their name, email address, and title are added to one of the hundreds of consolidated text files containing verified targets. In many cases, this file includes supplemental information about the CEO at the target company, who will be impersonated in the BEC attack.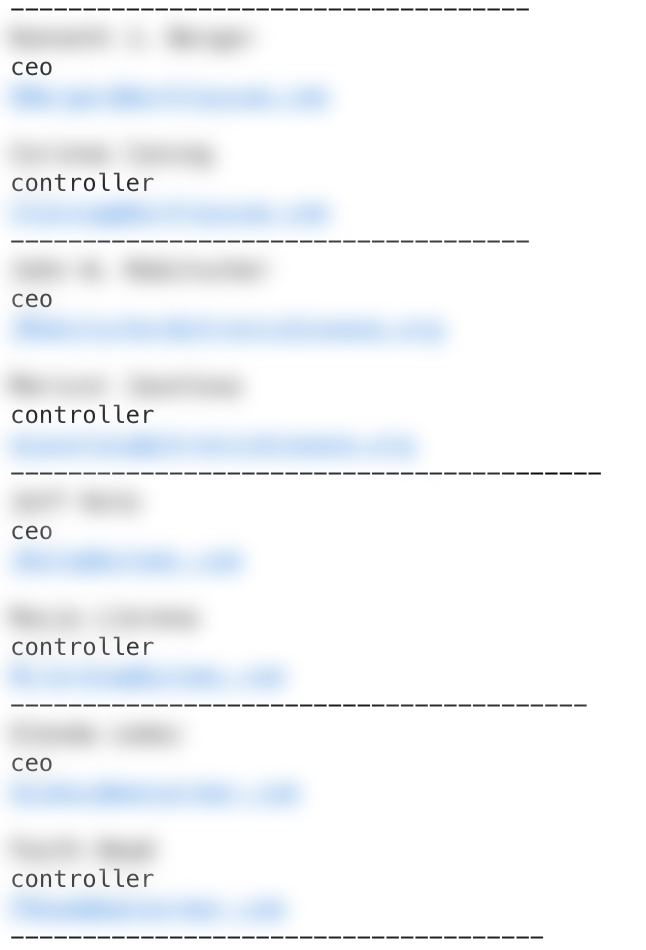
Example of a Consolidated List of Validated Targets
If a Curious Orca scammer receives one of these automated bounce responses, however, the address is deemed to be invalid. When an email address is invalidated, the scammer moves on to other tactics.
Continuing the Compromising Chase
The target information is useful, so the scammer does not want to immediately give up immediately. As a result, he begins iterating through a series of likely email username combinations to see if one works. For example, if the target’s name was John Smith and the original invalid email address was [email protected], the scammer may cycle through the following email variations:
[email protected]
[email protected]
[email protected]
[email protected]
For each email variation, Curious Orca sent another blank probing email looking for a bounce. If one of the alternate email permutations fails to generate a bounce message, the target and the newly validated information is added to a verified target list. If, however, the scammer burns through all of the obvious address combinations and receives a bounce email for all of them, then the target is simply excluded from the final target list—sparing that address from receiving a subsequent BEC attack.
While Curious Orca manually tested various email address variations, there are also online tools that attempt to predict the likely pattern used by email addresses on a specific domain. Like other commercial services used by BEC groups to identify initial raw target sets, these services are widely used by legitimate marketing teams; however, cybercriminals are exploiting them for more nefarious purposes.![]()
![]()
Examples of an Online Service Predicting Likely Email Patterns
By using these services, the cybercriminals are able to quickly and easily spot patterns and then test the most likely email combination, without having to go through the manual testing outlined above.
The Ugly Truth about Cybercrime
You might be thinking to yourself at this point... “This verification process seems like a lot of work. Surely, this group isn’t able to probe THAT many email addresses!”
Cybercriminal organizations have become practiced in these tactics to the point that they are able to perform them in an extremely efficient manner. Since 2018, a single Curious Orca associate has sent blank reconnaissance emails to more than 7,800 email addresses at over 3,200 companies in at least 12 countries, including Australia, Canada, Denmark, Hong Kong, Israel, Italy, the Netherlands, Papua New Guinea, Singapore, Sweden, the United Kingdom, and the United States. The validated contact information collected by this actor has contributed to a master targeting database containing more than 35,000 financial controllers and accountants at 28,000 companies around the world.
Even more surprising, these scammers are not using automation to send their probing emails. Each validation email is sent manually. In fact, one Curious Orca actor spent 46 hours over ONE WEEK performing reconnaissance using probe emails and consolidating validated address into master target lists. This is a significant amount of time and looks very similar to an actual work schedule, which underscores our previous findings that these groups operate very similarly to normal, everyday businesses.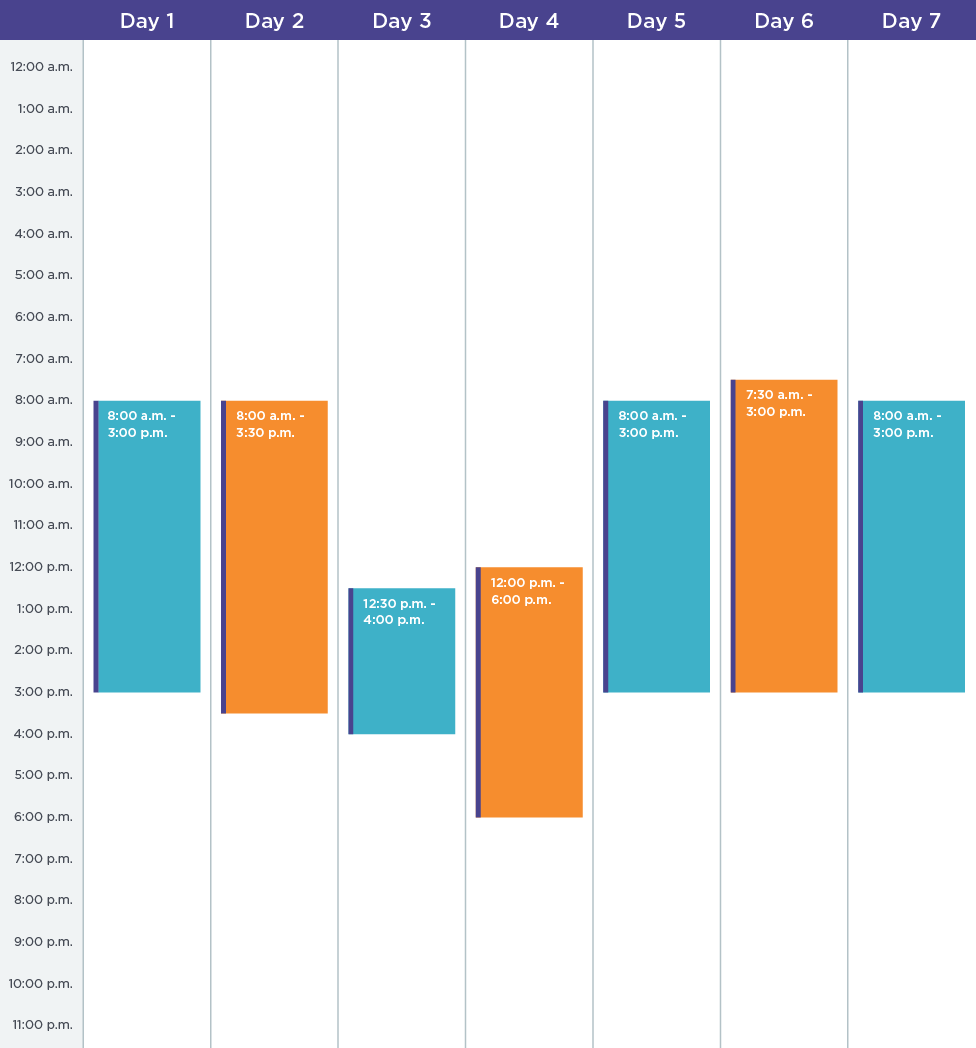
A Week in the Life of a Curious Orca Email Validation Actor(Times are West Africa Standard Time, GMT +1)
So what can you do to protect your company and your employees against these types of pre-attack email probes?
One easy step is to disable email bounce messages to external senders. This tactic will prevent threat actors conducting bounce reconnaissance from getting a notification telling them whether an email address is valid. While this would make an actor think that any email address they test is valid, meaning that all target email addresses on your domain would likely make it into the final target list, it would prevent them from being alerted if a test address is invalid. In this case, any email they send to an illegitimate address would simply go into a black hole and they would be none the wiser.
Another strategy is to configure your inbound email filter to look for inbound emails with no content. Since these emails are often used as a precursor for a follow-up attack, notifications of this nature would allow your team to alert targets to be cautious of any suspicious activity and block additional phishing emails before they reach the inbox by providing inbound visibility.
Gain more insight on the global reach of BEC attacks with "The Geography of BEC" report.