Business email compromise (BEC) is a term that encompasses a variety of techniques and tactics that cybercriminals leverage to obtain money or data via identity deception. Despite the evolution and repurposing of this suite of associated tactics, one constant has remained throughout—the correspondence between scammer and victim is done, almost without exception, over email.
This foundational conduit between attacker and victim has also now become the focus of evolution, with actors increasingly looking to transfer potential victims from email over to SMS, as mobile devices make it easier to facilitate attacks.
Like most BEC attacks, these new types of campaigns are initiated with an email sent to a prospective victim that is written to elicit a response. The only difference is that the scammer includes a request for the recipient’s cell phone number. By moving them over to their cell phone, the scammer is equipping their victim with all the functionality needed to complete the task that is to be given to them. A mobile device offers instant and direct messaging, the ability (in most cases) to still access email, the ability to take pictures with the phone’s camera, and far greater portability than a laptop, which all increases the chances that the scammer will be successful in achieving their desired outcome once a victim is on the hook.
The victim must immediately make a decision about whether to trust the situation, and they often do without realizing what is happening. On the other side, the scammer knows that the fraud is working the second they receive a reply containing the requested phone number.
Whether this approach is more realistic than a purely email-based exchange is, to a large extent, dependent on whether a mobile device is used in everyday communication within a targeted organization and would be quickly demonstrated by how the victim reacts to the initial request. Because most people think of an average scam as being initiated and continuing on one mode of communication, the slight increase in complexity may also decrease a recipient’s likelihood of believing the request is a scam.
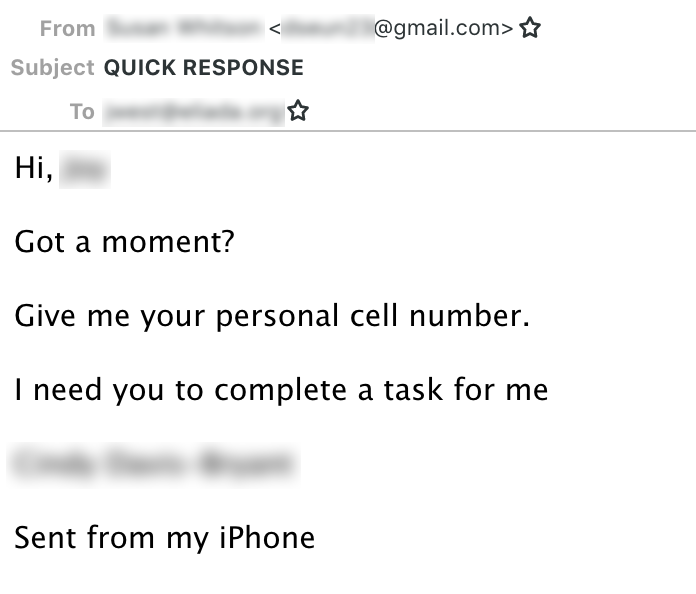 Example of the initial email sent in an email-to-mobile BEC attack.
Example of the initial email sent in an email-to-mobile BEC attack.
Based on an analysis of campaigns using these tactics, the identity generally impersonated by an actor is that of the CEO of an organization. Adopting the role of CEO comes with obvious hierarchical advantages, which is especially useful when requesting an employee’s cell number out of the blue.
Once a recipient replies with their cell number, the actor is immediately placed in a strong position. They’ve minimized the risk of the initial display name deception being noticed, and they have established a method of communication that, by its very nature, places greater expectations to make a more instantaneous reply than that of its email counterpart.
In terms of operational security, the scammers have not increased their risks of being identified by any tangible amount. Even if the gang was operating from a country other than the United States, it costs no more than a few dollars to set up a temporary US-based number, and there are many legitimate services which provide numbers relating to any state, and even any country, available both online and on Google and Apple’s respective app stores.
Having access to a US number also enables the actor to create a Google Voice number, which still prove to be extremely popular with non-US based cybergangs. Features such as being able to create personalized greetings that can be assigned to specific callers makes the use of multiple personas easy to manage. You can also send and receive SMS messages directly from a computer, allowing the actor to remain within the environment from which they run the majority of their operations. Furthermore, there is the ability to record voice calls, and voicemails are automatically transcribed and forwarded to you contained within an email, which allows the gang to keep a detailed record of what has been said, helping to avoid any costly mixups.
What unfolds next between the fraudulent CEO and their employee is fairly typical of how an email-based gift card scam plays out, but there are subtle differences that tangibly enhance the actor’s chances of being successful.
In a BEC SMS scam, the actor has the ability to play a greater role in guiding the victim throughout the entire gift card buying process. SMS is more conversational in nature than email, which mitigates potential stumbling blocks IN the completion of the task. If the type of card originally requested is not available or if there are problems with payment, it can easily be adjusted on the fly by the scammer. The screenshot below shows a reply from a victim who is messaging a persistent actor to update them that they are in line to pay for the requested gift cards.
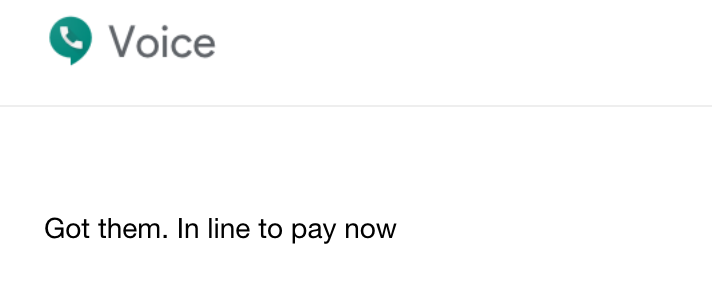 Victim response to mobile BEC scammer via Google Voice
Victim response to mobile BEC scammer via Google Voice
Finally, once the purchases have been made, the SMS dialogue now lends itself to being the perfect way to get the gift cards into the hands of the actor without any delays. Scammers generally ask a victim to take a picture of the back of the gift cards, after revealing the redemption codes, using the phone’s camera even before leaving the store.
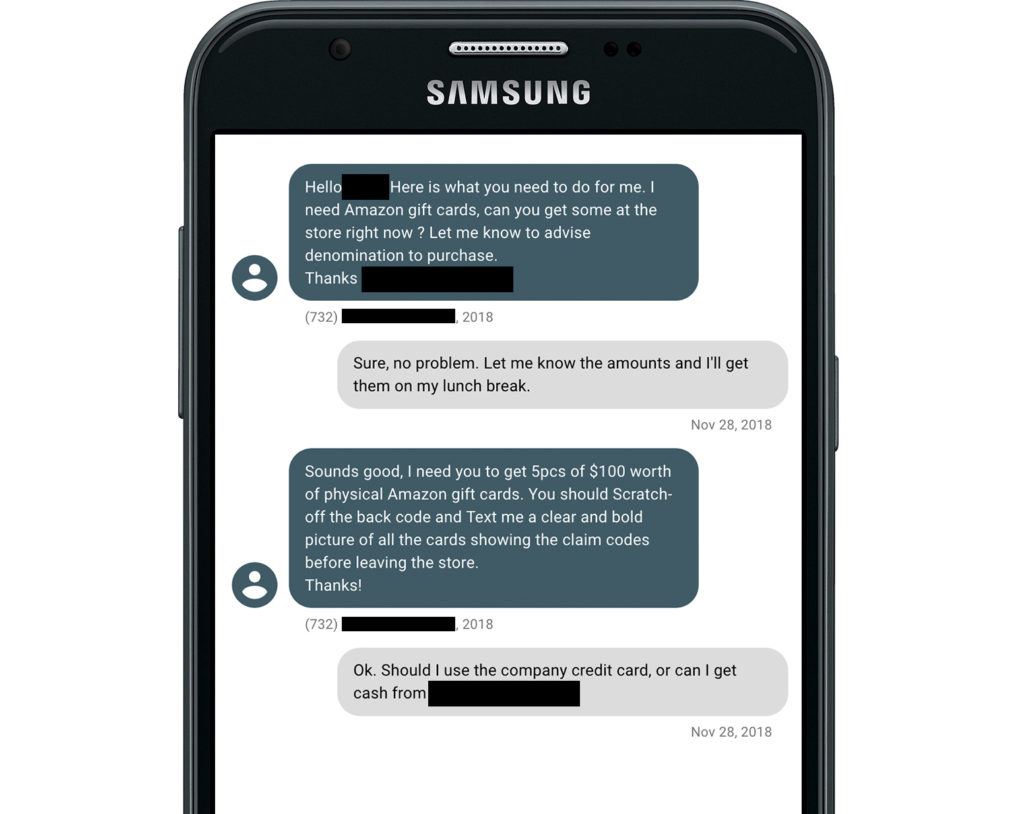 Scammer requesting Amazon gift cards from a presumed victim.
Scammer requesting Amazon gift cards from a presumed victim.
Once the scammer has pictures of the gift cards and redemption codes, they waste no time in laundering the gift cards through online services. We recently highlighted the process BEC actors use to launder gift cards in a report published on a group we called Scarlet Widow. Scarlet Widow, like many other BEC groups we track, launders gift cards through Paxful, a legitimate online peer-to-peer marketplace, that allows users to buy bitcoin from other users using hundreds of different payment methods, including dozens of different types of gift cards. To trade gift cards on Paxful, though, sellers take a significant hit when it comes to exchange rate. For example, most Apple iTunes gift cards are traded at 40 to 80 cents on the dollar.
After a gift card has been traded for bitcoin on Paxful, the funds are deposited into a wallet, but the cryptocurrency still needs to be converted into cash. To do this, an actor moves bitcoin from their Paxful wallet to a wallet on another peer-to-peer cryptocurrency exchange—in Scarlet Widow’s case that exchange is Remitano. On Remitano, users are able to advertise their bitcoin for sale and a buyer can purchase the bitcoin for a specified price via bank transfer. Once a scammer has exchanged their bitcoin on Remitano and the buyer’s funds are in their bank account, the process of converting illicit gift cards into cash is complete.
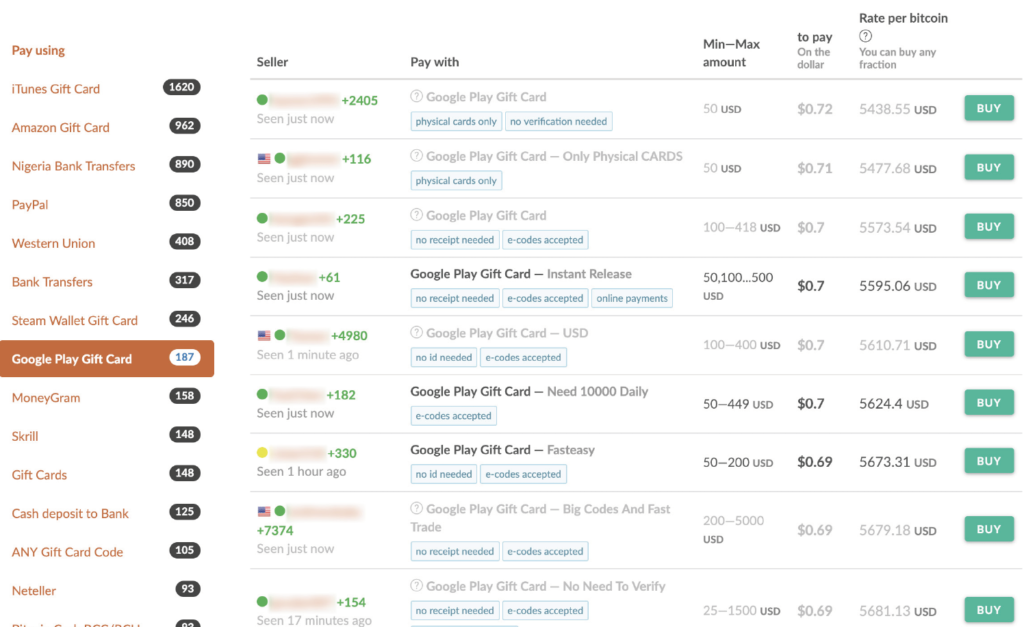 Screenshot of Google Play gift cards posted on Paxful.
Screenshot of Google Play gift cards posted on Paxful.
To protect yourself from becoming a victim of these types of BEC attacks, there are some really effective ways you can approach any unsolicited request over email to provide your cell number. If the email purports to be from a colleague, first check to see the sender’s email address. With the vast majority of these attacks relying on domain name deception, the first sign of a red flag will show here.
The email address checks out and a number is supplied, insist on a brief call before making purchases on behalf of someone else. As a final safety net, share concerns with a colleague or friend, especially if pressure is increased in unusual ways. As always, it’s better to be safe than sorry when dealing with these types of emails.
Related content:
Scarlet Widow: BEC Bitcoin Laundry—Scam, Rinse, Repeat
How cybercriminals transfer gift cards
COVID Text Scam Warning from National Health Service (NHS)
Scammers deploy phishing texts and lookalike websites