You’ve seen headlines like "Facebook and Google were Scammed Out of $100 Million" and "Equifax's Massive Data Breach Has Cost the Company $4 Billion So Far."
Despite significant investments in email security solutions, the threat from an endless barrage of spear-phishing attacks, business email compromise (BEC) schemes, account takeover-based attacks (ATOs) and other advanced email threats that result in security breaches and fraud just keeps growing by the day.
The fact is, no organization is invincible, no industry immune to the growing scourge of targeted, socially-engineered, email-based identity deception attacks designed to fool employees into revealing sensitive information, pay fake invoices or wire payments under the mistaken belief they're responding to a trusted colleague, business partner or client.
Today, 96% of all data breaches start with a malicious email. The cost of data breaches continue to rise each year, with the average breach in the United States now costing $7.3 million per incident. According to the FBI and IC3, losses from BEC alone have exceeded $12 billion from 2013 through 2017. The losses are real and pervasive. And they’re not limited to large companies or financial services companies, either. In research published by Agari, 96% of organizations have been the target of a BEC attack.
With such a persistent and costly threat, why aren’t more security controls put in place to stop these breaches and email fraud?
My thesis is that information security professionals aren’t comfortable, or may lack experience building compelling, ROI-based business cases to win the budget. When a business is weighing its level of investment in ERP software to cut cost in their supply chain or a SaaS solution to make their sales team more productive, the money always seems to be there. Security often loses because it can’t quantify the value to the business.
To get you started, part one of this series will provide some sources and statistics I’ve used to help Agari customers secure the budget needed for security controls designed to stop breaches and eliminate BEC attacks.
In part two, we'll cover important factors for preventing email attacks that target your customers and can cause serious damage your brand in the marketplace.
Breach and Email Fraud Economics
When it comes to inbound threats, you have to look at three factors to build your business case:
- The potential losses to your organization in the event of a successful attack
- The probability of a successful attack occurring per year
- The percentage reduction in that probability that can be directly attributed to implementation of a specific security control
The more specific you can be to your company and industry, and the more substantiation you can provide regarding these three items, the more compelling your business case will be. Here are a few stats and sources to get you started in quantifying the value that can be realized from reductions in the risk of a security breach or Business Email Compromise fraud.
Breach Costs
The first thing you need in your business case is the potential loss your organization would face if a breach occurs. This year, the average cost of a successful data breach is up 6%, to $7 million for organizations in the US, according to the 2018 Cost of Data Breach Study from Ponemon Institute. For financial services firms, the average is $12 million. For the healthcare and technology sectors, it's $14 million. Ponemon offers a public tool (requires form information) that will allow you to look up the estimated cost of a successful breach based on your country and industry. Here is a quick table to look up the same information.
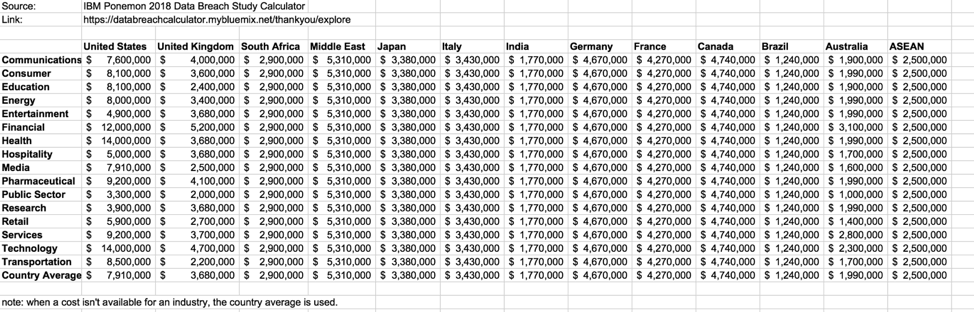
Breach Probability
The second piece of information you need to establish is the probability that your organization will experience a breach despite your existing security controls. Before you say “My security is so good, we’ll never have a breach,” or “We’ve never had a breach before, I think the percentage is low” consider the following.
The Identity Theft Resource Center documented 1,579 reported data breaches in the United States in 2017, which was a 44% increase over 2016. When you consider that many—if not most—breaches go unreported, that number could be much higher. The Ponemon Institute puts the average percentage likelihood of a breach occurring within 2 years at 27.9%. Therefore, in the absence of any other information, we recommend factoring half of that percentage, or 13.95%, as the default breach probability per year when we work with customers to develop the business case.
Business Email Compromise Fraud Costs (CEO/CFO Wire Transfer, Invoice Scams, etc)
According to the FBI, the average loss from BEC cons is more than $159,468 per attack. But that may be too conservative. Just in the last two years, we've seen Google and Facebook hit with $100 million in losses through a partner invoicing scam. Also, keep in mind that you could face multiple successful BEC attacks per year if you are a large organization or targeted by a cyber-criminal network.
Business Email Compromise Loss Probability
Because BEC attacks are a relatively new fraud vector, there really hasn’t been enough independent research on the probability of success rates relative to total number of attacks. However, as captured in “Behind the From Lines: Email Fraud on a Global Scale,” our own data indicates that 0.37% of all BEC “probes,” or initial malicious emails, were ultimately successful. That figure jumps to 3.97% if the target responds to that initial email probe.
So, if you know how many BEC messages are delivered to your employees per year, you can multiply that by 0.37% to determine the likely number of successful BEC attacks per year. For our customers, we typically recommend using a free trial version of Cloud Email Protection for 30 days to identify the number of BEC attacks over 30 days and then annualize that number.
In ROI analysis conducted for a financial services client, we found that Cloud Email Protection would block 4,116 BEC attacks per year. Factoring in the average BEC success rate, we were able to establish that the company would experience 15 successful BEC attacks per year, at an estimated cost of $2.3M.
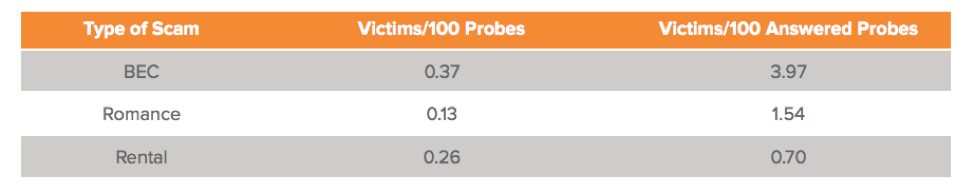
Estimating the Risk Reduction and Cost Avoidance Provided By Security Controls
There are two key areas where a security control can show ROI related to security breaches or BEC email fraud:
1. What reductions in successful attacks can you expect?
Look at the solution’s performance based on deployments at organizations similar to your size and industry. Using Agari as an example, our Phishing Defense solution goes beyond traditional email security systems by analyzing the context, behavior and relationship between sender and recipient. No security control is 100% fraud proof, and I would suggest scrutinizing any vendor claim about their solution’s effectiveness. The best way to do that is either through a trial in your production environment or finding a reference customer of a similar size or type.
2. What reductions in costs can you expect?
What are your current costs in terms of detection and escalation, breach response, legal expenditures, regulatory fines, and notifications? The fact is, assigning staff to sniff out identity deception-based email attacks diminishes productivity, takes away from other priorities, and adds investigative workload to IT administration. Will the solution under review enable you to consolidate security controls so you can save money while boosting productivity?
An Ounce of Prevention is Worth a Pound of Cure
The fact is, email remains the single most important tool for business communication and collaboration, yet it is also the initial point of entry for the vast majority of successful security breaches.
The tens of billions of dollars in global losses from advanced email threats make the business case for preventive security controls a no brainer.
As Benjamin Franklin once said, “An ounce of prevention is worth a pound of cure.” Preventing the next spear phishing or BEC email from ever reaching employee inboxes represents a fraction of the cost of a $7M breach or a $100M BEC partner invoice scam.
In today’s threat environment, there are only two kinds of companies: Those that have been hit by a successful email attack. And those that have been hit by a successful email attack and just don’t know it yet. The probability of experiencing a breach or successful BEC attack is a near certainty if you don’t have advanced email protections in place.
With that in mind, the time to act and build the business case for solutions that can protect your business is now. It’s my hope that the considerations presented in this post can help you source a solution that can best enable your organization to defeat email fraud, BEC, spear-phishing and other incoming email threats with maximum ROI.
And we aren’t done yet: In part two, we’ll take on the ROI of stopping phishing email attacks that target your customers using your brand.
Try the ROI calculator to learn more about the cost of advanced email fraud prevention solutions for your organization.