Phishing is one of the most prevalent forms of cyberattack used by bad threat actors to either steal personal data, or to gain entrance into a business’ network. These surreptitious and malicious email messages trick unsuspecting recipients into clicking a link or opening an attachment that contains malware, ransomware, or in the case of Business Email Compromise (BEC),employs impersonation tactics to deceive the recipient to take action quickly (often by posing as an inside employee or trusted sender).
As day-to-day business continues to take place at the speed of light and the number of employees working remotely increases, cybercriminals often have the edge when it comes to dreaming up sophisticated schemes of trickery. This leaves overburdened SOC teams to juggle multiple security vendors to try to ward against these evolving threats, manage multiple logins and UIs, and stay on top of ever-increasing compliance requirements.
Currently, managing email security is becoming untenable because too many threats are still getting into inboxes. In the latest Quarterly Threat Trends & Intelligence report from Agari and PhishLabs, more than 95% of email-based threats in Q2 2022 were attributed to credential theft and response-based attacks. Why? Well, the on-prem Secure Email Gateways that almost all organizations have had in place were designed to stop spam and malware by looking at the content or payload of an email. And most leading SEGs still rely on the approach of detecting “bad” or malicious content like malware, keywords, or high volumes of attacks from a single IP address.
Now That We Know the How, What About the Why?
Why are phishing emails and other social engineering methods continuing to succeed? First, most organizations’ content inspection process is too shallow. If you’re not inspecting deeply enough into existing content (beyond the subject line and “From” field)—including the message body, attachments, images, and more—then you are increasing the chances of the email infiltrating. Most enterprises have this gap and insiders will exploit it.
Another issue is that cybercriminals have innovated faster with social engineering schemes and account takeover-based tactics that strive to entrap employees to be fooled into unwittingly engaging with attackers than the email security industry can keep up with. These types of identity-based threats—such as executive and brand impersonation—bypass traditional security controls because those aren’t attuned to recognize and catch them.
And finally—from a compliance perspective—SOC teams struggle to enforce policies because they are inflexible and lack granularity. This inability to detect good from bad emails endangers business communication flow and, in turn, runs the risk of businesses becoming non-compliant.
Fortra Is Your Email Security Ally
Through a layered approach, Fortra fills major gaps in email platform security by protecting users from external threats and safeguarding your sensitive data from being leaked both inside and outside your organization. By integrating with your existing infrastructure–whether in the cloud, on-prem, or in hybrid environments–it can improve your SOC team’s effectiveness and efficiency. But how?
- Our Deep Content Inspection engine protects your inbox from advanced email cyberattacks and prevents against outbound data loss through deep inspection capabilities. During the pre-delivery phase, our Secure Email Gateway inspects incoming emails and spam, malware, and ransomware that can be intentionally buried in emails or attachments in phishing campaigns and prevents them from reaching user inboxes.
Then, through the sanitization of suspected or confirmed malicious messages and removal of threatening elements, like HTML script from the message header, subject, body, and various custom file formats using binary signatures, the Secure Email Gateway removes embedded Advanced Persistent Threats without disruption to inbound messages. Additionally, it scans for and sanitizes inappropriate images (i.e. anti-steganography) in a safe Sandboxing environment. It can also remove attachments based on the message’s classification as identified by policies, and perform real-time URL lookup, resulting in either the removal of or blocking of the links, or rewriting URLs through easily integrated 3-party solutions.
But it can also help on the OTHER end by blocking sensitive data from leaving your organization or being shared among employees to avert data loss and/or compliance failures through Optical Character Recognition, redaction capabilities, and adaptive data loss prevention mechanisms. This way, compliance managers have real-time visibility and remediation controls to meet requirements and make sure that policies are being enforced.
- When it comes to more complex identity-based threats, this is where our Identity Threat Detection comes into play. Fortra's Email Security features can combat the upward trend of deception through predictive artificial intelligence—Agari's Identity Graph which leverages machine learning to stop socially engineered attacks. This approach allows us to deploy a predictive defense system that recognizes identity deception techniques, such as spear phishing, targeted email attacks and others, at massive scale and speed. It's an approach that gets smarter every day by leveraging an increasingly vast data set to give customers a level of protection against identity deception they can't get anywhere else.
It does this by studying sender-receiver behavior, mapping identities, and authenticating everyone employees communicate with inside and outside of the organization. It then takes all this data and models relationships and patterns that represent known “good” behaviors and compares the hundreds of message characteristics against multiple behavioral models that determine its trust score (by changing variance or deviation from the expected behavior considered to be “trusted”).
- Lastly, our Global Inbox Threat Intelligence gathers and sources intel from reported emails from your employee base—the first line of defense for email threats—and across our global client base to curate a unique set of intel that feeds directly into your security architecture. With phishing campaigns and other advanced social engineering threats constantly evolving and being delivered in a myriad ways, you need a comprehensive, central source of intelligence to serve as a foundation for your overall security that supports the continuous improvement of your email security suite.
Fortra’s research analyst team scopes out any indicators of compromise and evidence of any mule accounts and crowdsources threats for known malicious indicators like file hashes, email addresses, and URLs into a SINGLE intel feed. By gathering threats from user-reported emails within your organization, as well as from our entire user base and other Fortra solutions like PhishLabs' Credential Theft service, Social Media Protection, Domain Monitoring and global BEC feeds, we extract all of the threat indicators and feed them back into the SEG to strengthen your security architecture against the latest relevant threats.
Then the indicators are utilized to detect and proactively remove, or claw-back, threats attacking multiple inboxes and suspend O365 lures, BEC, ransomware, malicious attachments, lookalike domains, and more. These threats are automatically fed into PhishLabs’ URL Detection Feed, which identifies malicious indicators—such as URLs, domains, and email addresses. Our continuous detection & response capability continues to gather more malicious indicators, thereby improving the strength of the threat identification and mitigation process and responds to the end user via push-through alerts, by employing auto-actions, and monitoring for real-time policy enforcement.
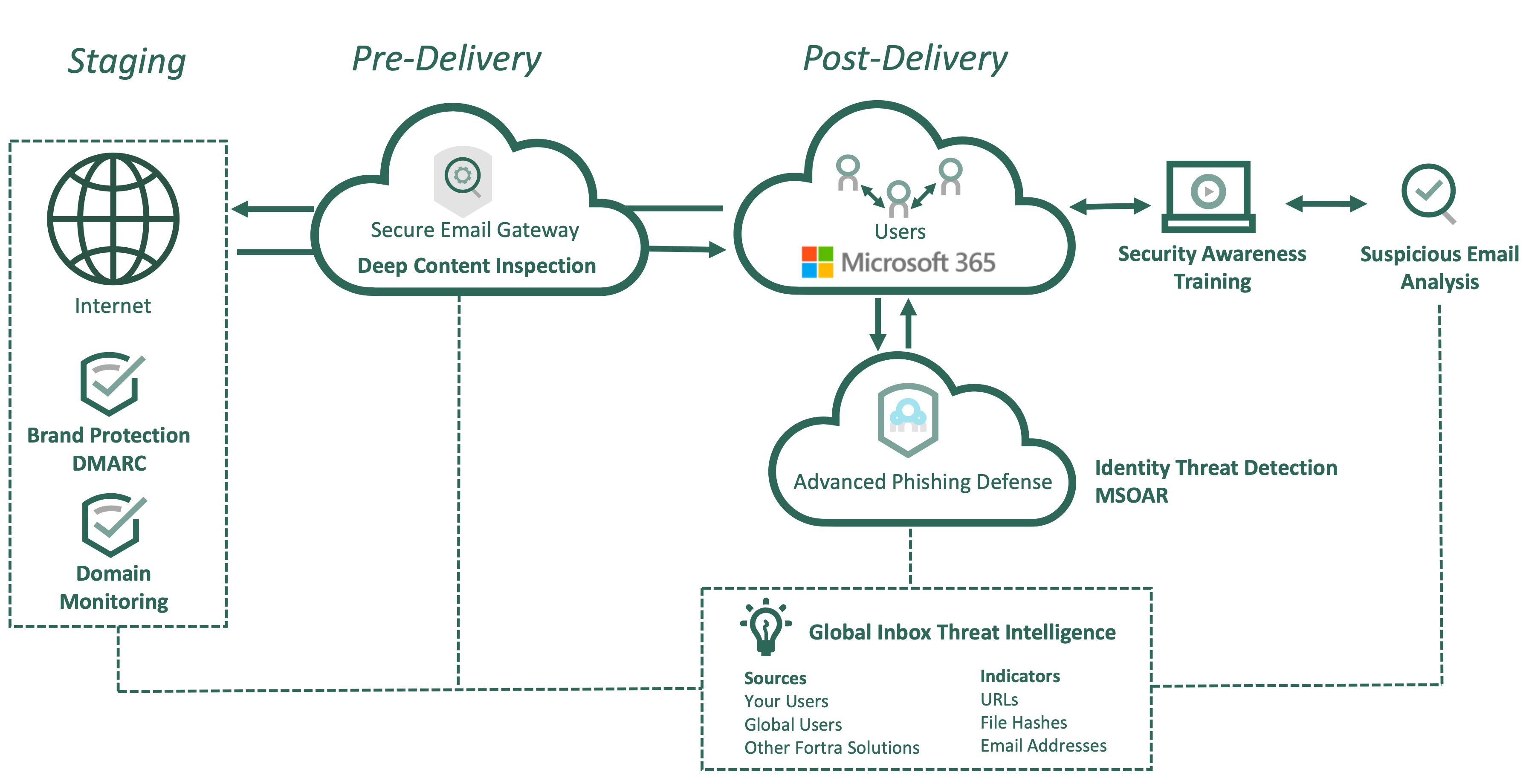
As the email protection rages on for enterprises, Fortra Email Security can be YOUR ally in defending against advanced email threats, socially engineered attacks, and more.
Read our latest whitepaper, "A Window on Email Security," which tells enterprises how to protect their businesses from hidden email threats.
