Over the last five years, Business Email Compromise (BEC) has evolved into the predominant cyber threat businesses face today. Since 2016, businesses have lost at least $26 billion as a result of BEC scams and, based on the most recent FBI IC3 report, losses from BEC attacks grew another 37 percent in 2019—accounting for 40 percent of all cybercrime losses over the course of the year.
The information contained in our new report, The Geography of BEC, comes from more than 9,000 active defense engagements conducted by ACID between May 2019 and July 2020. As a result of these engagements, we are able to collect crucial intelligence that allows us to better understand the operations of BEC criminal organizations. This includes the locations of the threat actors who perpetrate these attacks, as well as the money mules who play such an integral role in laundering the proceeds that result from them.
We were able to identify BEC actors in 50 different countries, demonstrating that while Nigeria has been the historical epicenter of social engineering activity, BEC actors and the individuals who enable their attacks can be found all over the world. Within our dataset, Nigeria was only home to half of the BEC operators we observed, which may be surprising given the historical role this country has played in the evolution of this form of fraud.
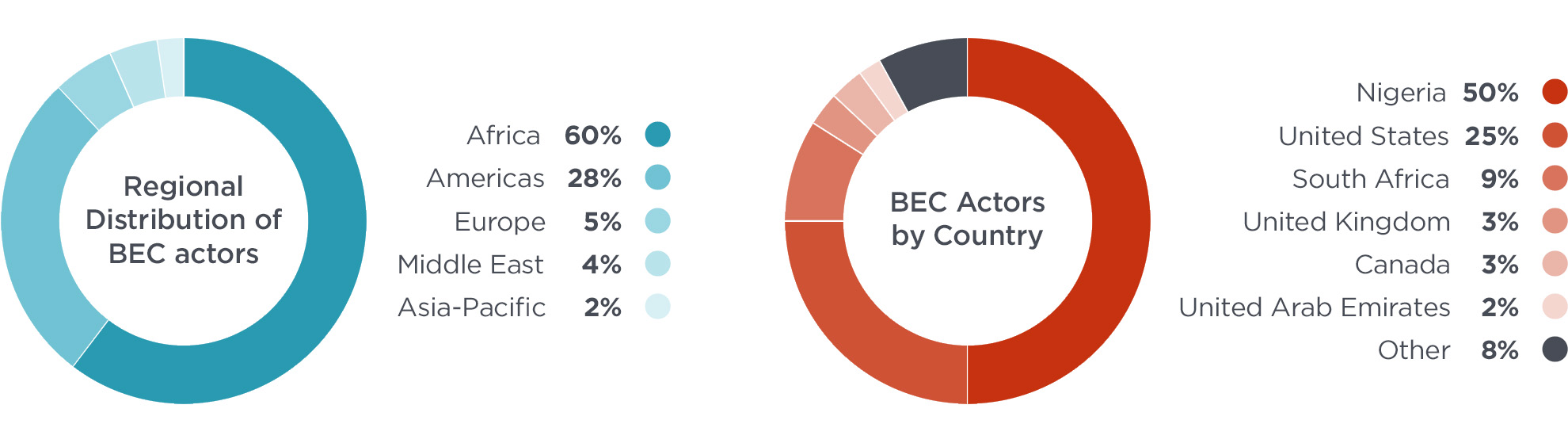
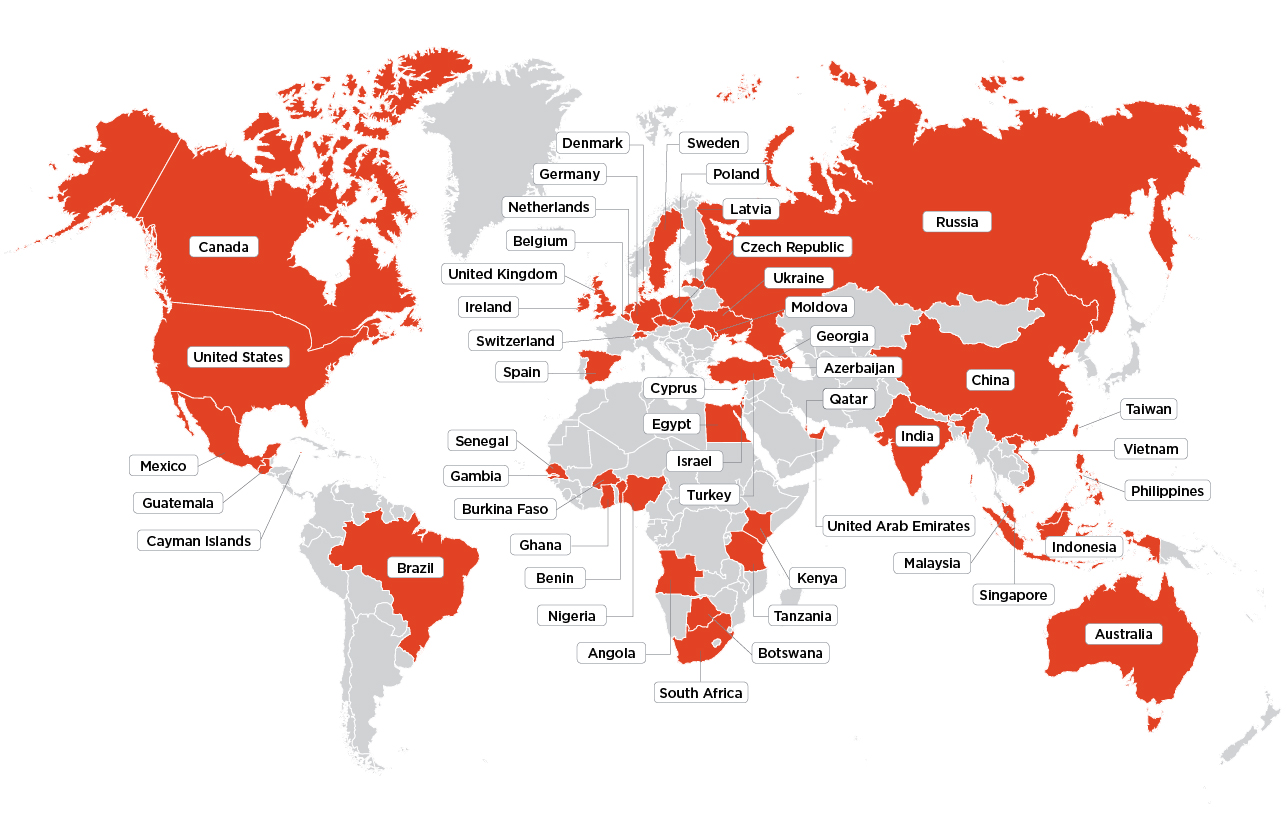
Surprisingly, a quarter of all BEC attackers had a home base in the United States. Nearly half of US-based BEC actors were located in five states: California, Georgia, Florida, Texas, and New York. Looking at the data more granularly, we observed clusters of actors around a handful of metro areas, including Atlanta, GA; New York, NY; Los Angeles, CA; Houston, TX; and Miami, FL. Incidentally, these metro areas match the locations where many recent BEC arrests have been made, including those made in Operation reWired, an international law enforcement operation that resulted in 281 arrests worldwide.
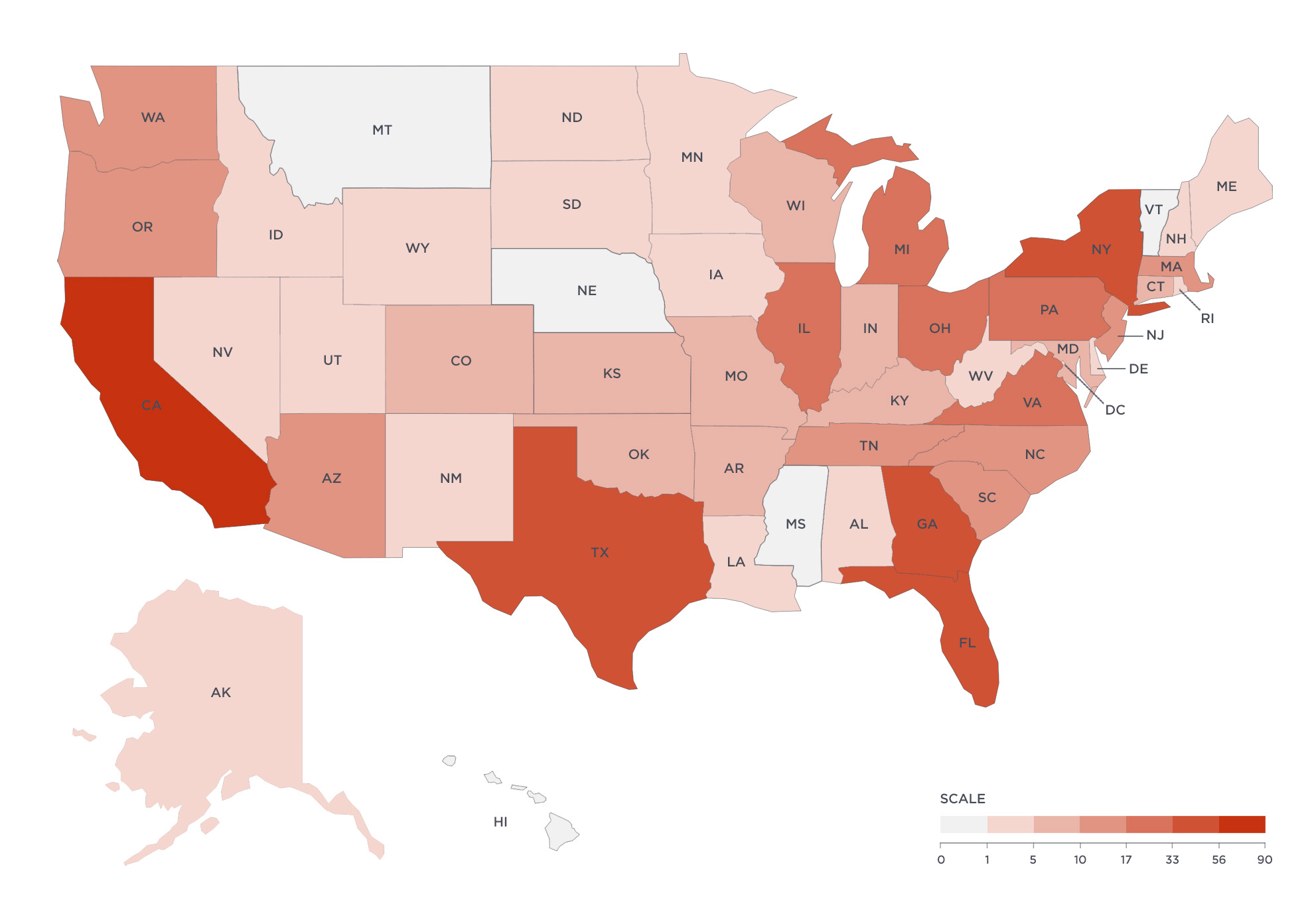
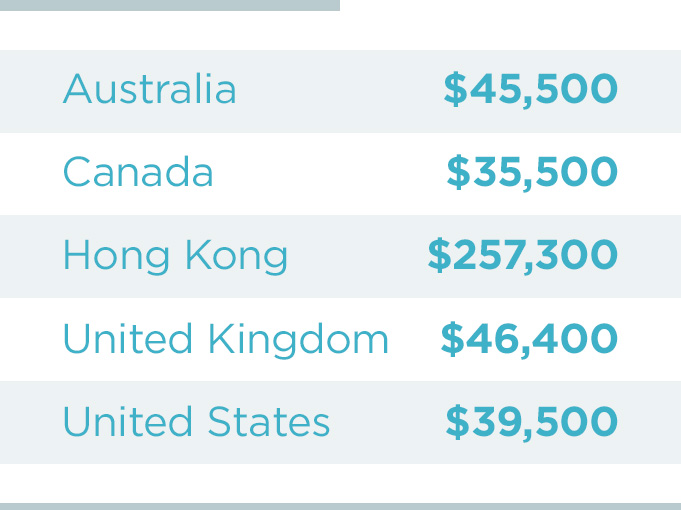
Money mules, one of the most important components of the BEC financial supply chain, were also observed around the world. Over the course of 15 months, we collected 2,900 mule accounts in 39 countries, through which scammers intended to receive more than $64 million in stolen funds from BEC victims. While 80% of these mule accounts were located in the United States, the requested payment amounts destined for those accounts were significantly lower than those seen in other countries. For example, the average amount of payments to US-based mule accounts was $39,500, while payments directed to mule accounts based in Hong Kong were $257,300—more than six times their stateside counterparts.
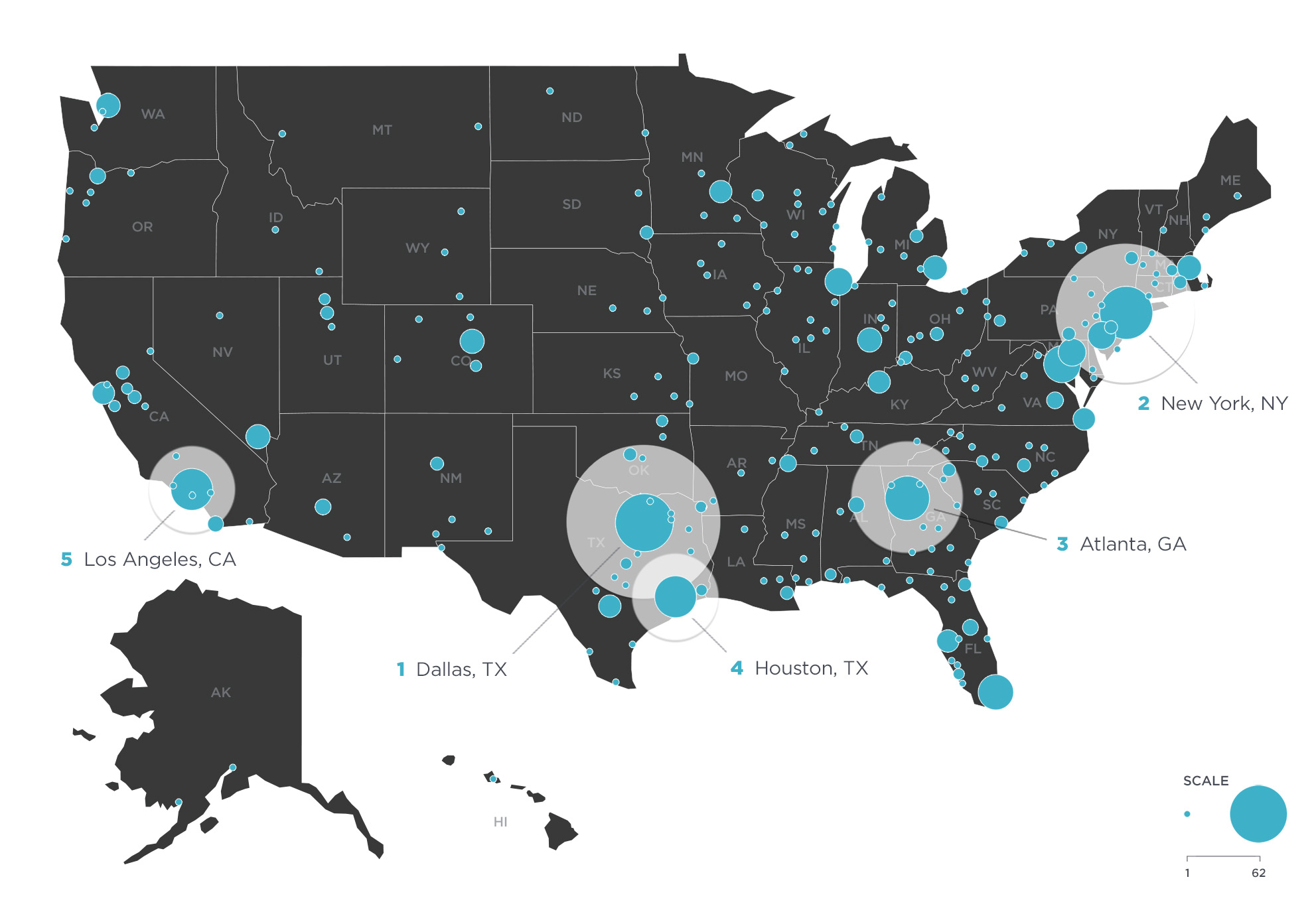
Within the United States, more than 900 mules were identified across all 50 states, as well as the District of Columbia. Many of these mules are likely to be unwitting victims of other social engineering attacks, such as romance scams and work-from-home cons. And a significant number of BEC mules were clustered around a small number of cities, indicating these areas may be hubs of BEC activity in the US. Mirroring the clusters of BEC actors, the top metropolitan areas for US-based money mules were Dallas, TX; New York, NY; Atlanta, GA; Houston, TX, and Los Angeles, CA.
While the global footprint of BEC demonstrates that the source of the problem is not contained to a small part of the world, it also shows that the simplistic geo-blocking capabilities of SEGs and firewalls are not a silver bullet to identifying malicious threats. Cybercriminals can hide behind VPNs and other proxies (something the actors we identified were not using), but our study also shows that a large percentage originate in places you might not expect, like the United States. This reinforces the need for comprehensive identity deception detection capabilities to defend against BEC attacks and other types of cyber threats.
For more information on the location of BEC actors and their money mules, download the full Geography of BEC report and register for the webinar.