“At some point, Russian and Eastern European cybercriminals are going to start thinking to themselves, ‘Why am I spending all of this time and money setting up infrastructure and hiring malware developers when I can just send someone an email, ask them to send me money, and they’ll do it.’”
For more than a year, this is a line we have used over and over again, expecting that some of the world’s most dangerous cybercriminals would move into the world of business email compromise (BEC) because the return on investment for basic social engineering attacks is much higher than more sophisticated malware-based attacks.
Today, our newly-released threat actor dossier shows how these expectations have now become a reality, detailing a Russian criminal organization we call Cosmic Lynx.
BEC attacks have become the predominant cyber threat businesses face today. Since 2016, businesses have lost at least $26 billion as a result of BEC attacks and, based on the most recent FBI IC3 report, losses from BEC attacks grew another 37 percent in 2019, accounting for 40 percent of all cybercrime losses over the course of the year. Evidence that more sophisticated threat groups are adding BEC to their attack repertoire should concern everyone. Unlike traditional BEC groups, Cosmic Lynx has demonstrated the capability to develop much more complex and creative attacks that sets them apart from other more generic BEC attacks we see everyday.
We have observed more than 200 BEC campaigns linked to Cosmic Lynx since July 2019, targeting individuals in 46 countries on six continents. Unlike most BEC groups that are relatively target agnostic, Cosmic Lynx has a clear target profile: large, multinational organizations. Nearly all of the organizations Cosmic Lynx has targeted have a significant global presence and many of them are Fortune 500 or Global 2000 companies.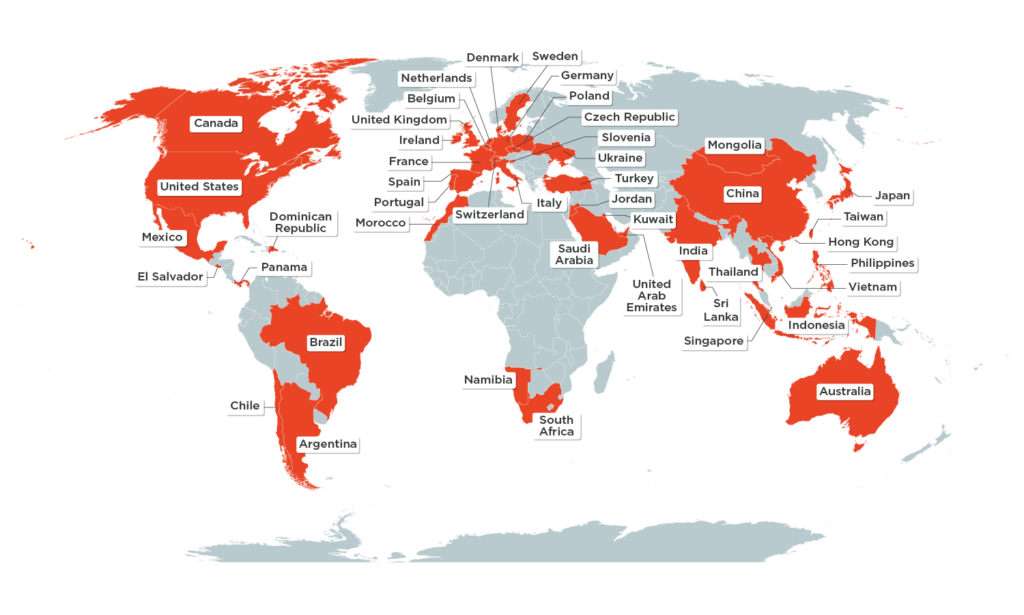
Map of Cosmic Lynx targets
The target employees of Cosmic Lynx are senior-level executives. Like other BEC groups, it seems Cosmic Lynx identifies employees to target based on their title. Three quarters of employees targeted by Cosmic Lynx hold the titles of Vice President, General Manager, or Managing Director.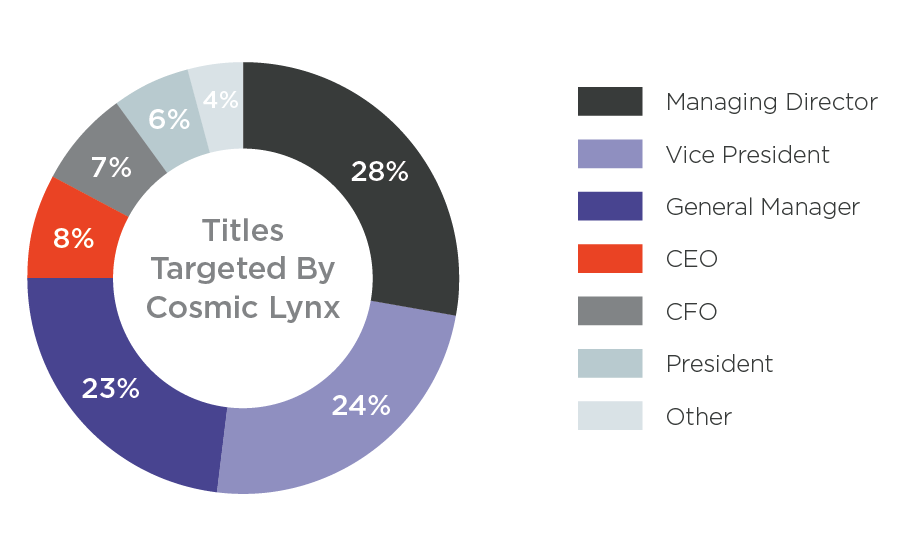
Titles targeted by Cosmic Lynx.
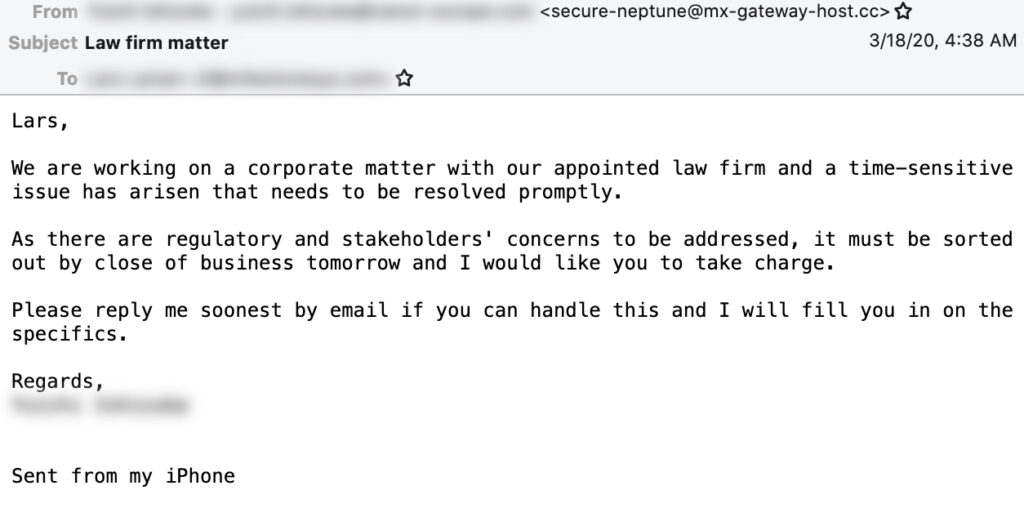
Cosmic Lynx employs a dual impersonation scheme. The pretext of their attacks is that the target organization is preparing to close an acquisition with an Asian company as part of a corporate expansion. First, they impersonate a company’s CEO, asking the target employee to work with “external legal counsel” to coordinate the payments needed to close the acquisition. Then, Cosmic Lynx hijacks the identity of a legitimate attorney at a UK-based law firm whose job it is to facilitate the transaction.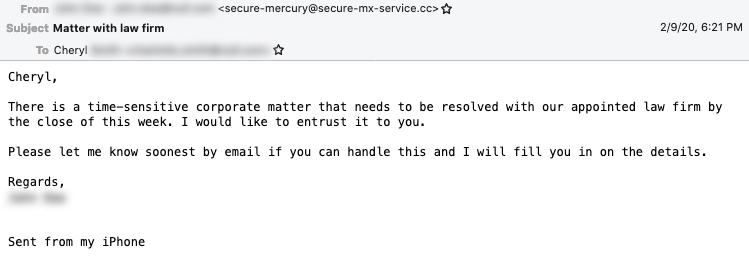
Example initial email from Cosmic Lynx.
The final stage of a Cosmic Lynx BEC attack is getting the target to send one or more payments to mule accounts controlled by the group. While the average amount requested in most executive impersonation BEC attacks is $55,000, the average Cosmic Lynx attack requests is $1.27 million. Cosmic Lynx prefers to use mule accounts in Hong Kong to receive stolen funds. The group is actively resistant to using mule accounts in the United States, but has provided secondary accounts located in Hungary, Portugal, and Romania.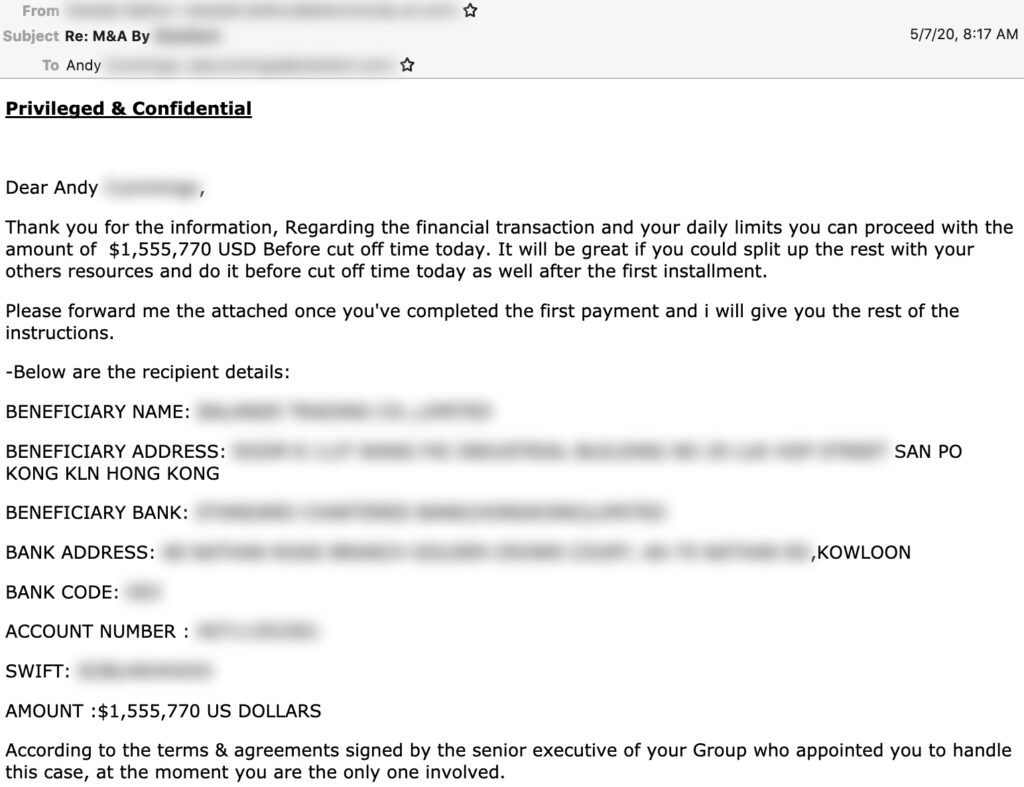
Hong Kong mule account provided by Cosmic Lynx.
While a vast majority of BEC attacks use free webmail accounts or registered domains to send malicious emails, Cosmic Lynx exploits DMARC controls to spoof the email addresses of impersonated CEOs, making their attacks appear much more authentic. For organizations that have implemented an established DMARC policy set to reject (p=reject) or quarantine (p=quarantine), Cosmic Lynx modifies the display name impersonating a CEO to include their email address, which still gives it the look that the email is coming from the CEO’s account.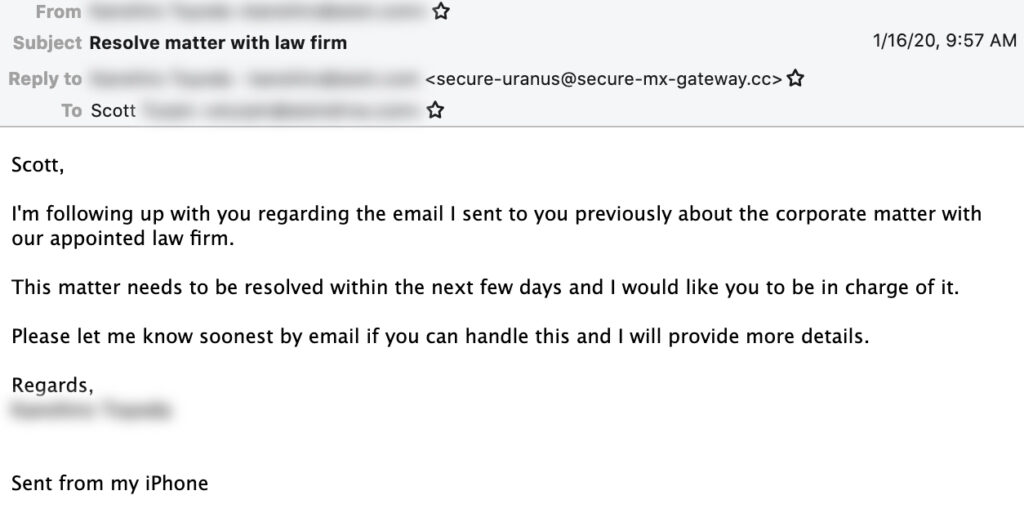
Spoofed (top) vs. non-spoofed (bottom) Cosmic Lynx emails.
Domains registered by Cosmic Lynx are named in a way to mimic secure email and network infrastructure (e.g., secure-mail-gateway[.]cc, encrypted-smtp-transport[.]cc, mx-secure-net[.]com). The mailbox referenced in a Cosmic Lynx email address usually references celestial bodies, like planets and stars--hence the “Cosmic” in Cosmic Lynx-- similar to the naming convention of some SMTP or DNS name servers.
To make their infrastructure more resilient and mask their identity in Whois records, Cosmic Lynx has registered a number of their domains with NiceVPS, a bulletproof hosting and anonymous domain provider. Cosmic Lynx’s infrastructure has also been linked to other types of malicious activity, including Emotet and Trickbot banking Trojans, Android click fraud malware, a popular carding marketplace, and Russian fake document websites.
NiceVPS home page.
To protect against threats like these, organizations first need to understand and accept the state of today’s cyber threat landscape. Most email-based threats today, like BEC attacks, are very simple social engineering attacks that are technically unsophisticated. To effectively protect against these threats, companies need to make sure they have defenses in place that are equipped to detect identity deception attacks that traditional inbound filters are not accustomed to handling. Additionally, organizations should have good internal processes in place, so payment requests, regardless of source, are verified before they are processed.
Learn more about Cosmic Lynx and their indicators of compromise (IOCs) associated with their previous attacks, download the full report.