What is an Account Takeover Attack?
An account takeover attack is a type of cyberattack where an attacker gains unauthorized access to a user's account, typically by stealing their login credentials.
Once the attacker controls the account, they can misuse it for various harmful activities, such as:
- Financial exploitation: Conducting unauthorized transactions or transferring funds.
- Phishing: Sending deceptive emails from the compromised account, leveraging the victim’s reputation to trick recipients.
- Data theft: Accessing sensitive information, like personal or financial data, stored within the account.
- Spamming: Distributing mass spam or malicious emails to the victim's contacts.
- Identity impersonation: Using the victim’s identity to gain access to other accounts or commit fraud.
How Do Account Takeover Attacks Begin?
There are different ways by which attacks can compromise and steal passwords. Most common methods include:
- Credential stuffing: Attackers use stolen usernames and passwords from other data breaches to try and gain access to other accounts on different platforms or websites. Since many people reuse the same credentials across multiple services and platforms, this attack exploits that common behavior.
- Phishing: Attackers trick users into revealing their login credentials, such as usernames and passwords, by impersonating legitimate websites, services, or individuals. The goal of this credential harvesting is to steal the victim's credentials to gain unauthorized access to their accounts or systems.
- Brute-force password cracking: Attackers gain unauthorized access to an account or system by systematically trying all possible combinations of passwords until the correct one is found. It relies on trial and error and can be applied to any login system that does not have robust security measures in place to block or limit repeated login attempts.
Anatomy of a Compromised Account by Takeover
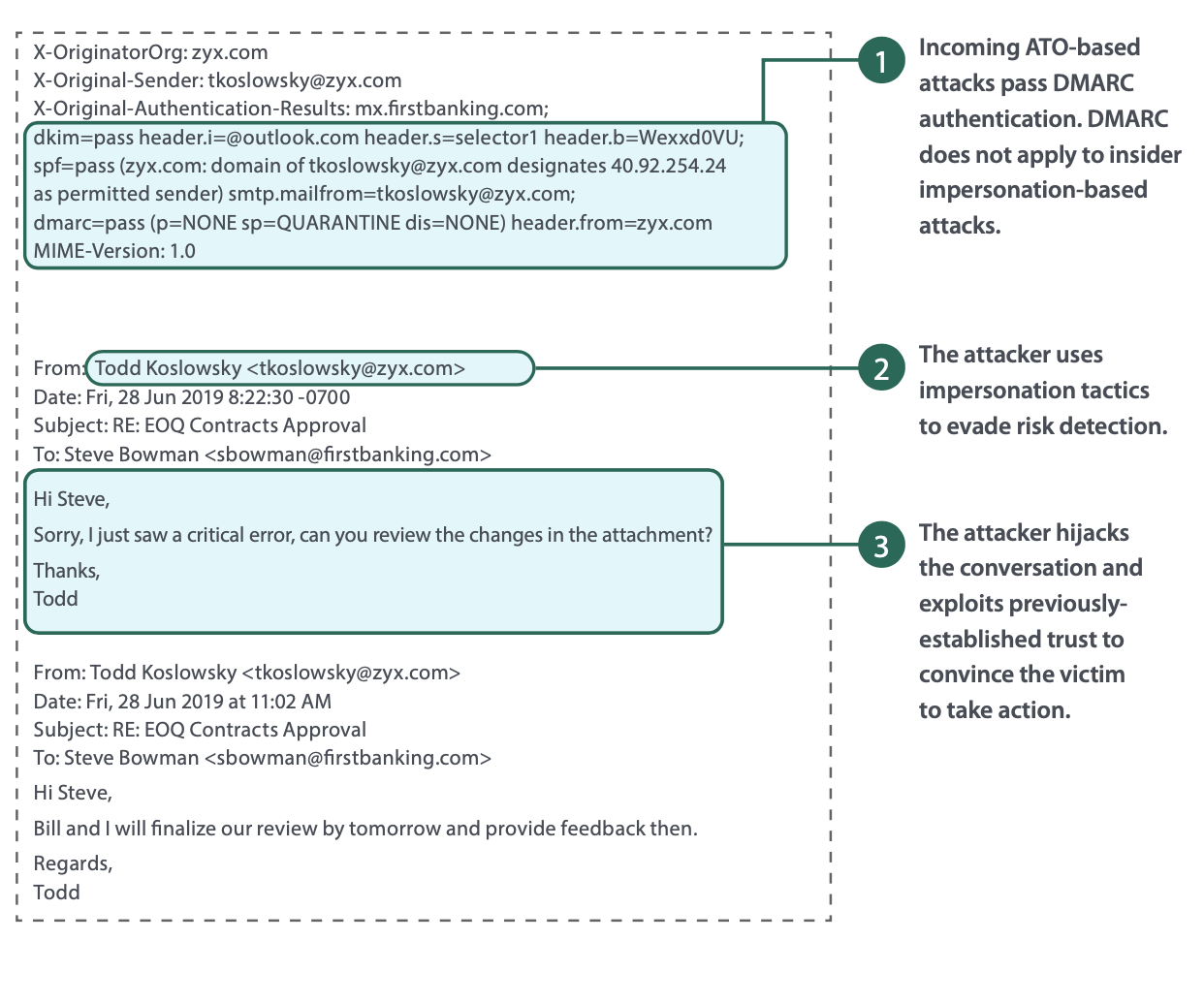
How Can My Organization Prevent Account Takeover Attacks?
An integrated cloud-based email security solution, or ICES, can perform the necessary steps to detect account takeover attacks, such as Fortra’s Cloud Email Protection, which prevents email-based account takeover attacks from reaching employee inboxes. It also inspects email flowing within an organization for indicators that an internal email account has been compromised for unauthorized use.
Once an account takeover is suspected, Cloud Email Protection prevents the spread of malicious emails from affected accounts laterally within and externally to the organization. It does this via advanced data science that combines ML models, LLMs, and neural networks to analyze hundreds of email characteristics, header data, attachments and URLs in order to detect impersonation and social engineering techniques. This results in a reliable determination of the trustworthiness of incoming emails.
So, implementing Cloud Email Protection affords organizations the prevention capabilities needed to stop these types of attacks—ensuring critical-business communication continues to flow securely and uninterruptedly.
