What is Account Takeover?
Account Takeover (ATO) is the process of taking unauthorized possession of online accounts using stolen credentials. This unsanctioned access allows cybercriminals to launch various attacks such as phishing, Business Email Compromise (BEC), financial lures and scams, data loss, and the list goes on.
According to Sift's Q3 2023 Digital Trust & Safety Index, account takeover attacks increased 354% year-over-year in 2023.
Types of Account Takeover
There are many types of account takeover attacks, however the majority are phishing scams or impersonation tactics aimed at harvesting credentials. Other common techniques include:
Anatomy of an Attack
Account takeover-based email attacks are among the toughest to detect — and the most devastating. Launched from compromised accounts of legitimate users, these attacks prey on the trust established amongst individuals, such as trusted colleagues or other credible senders.
PHASE 1: Acquisition
Initial Compromise
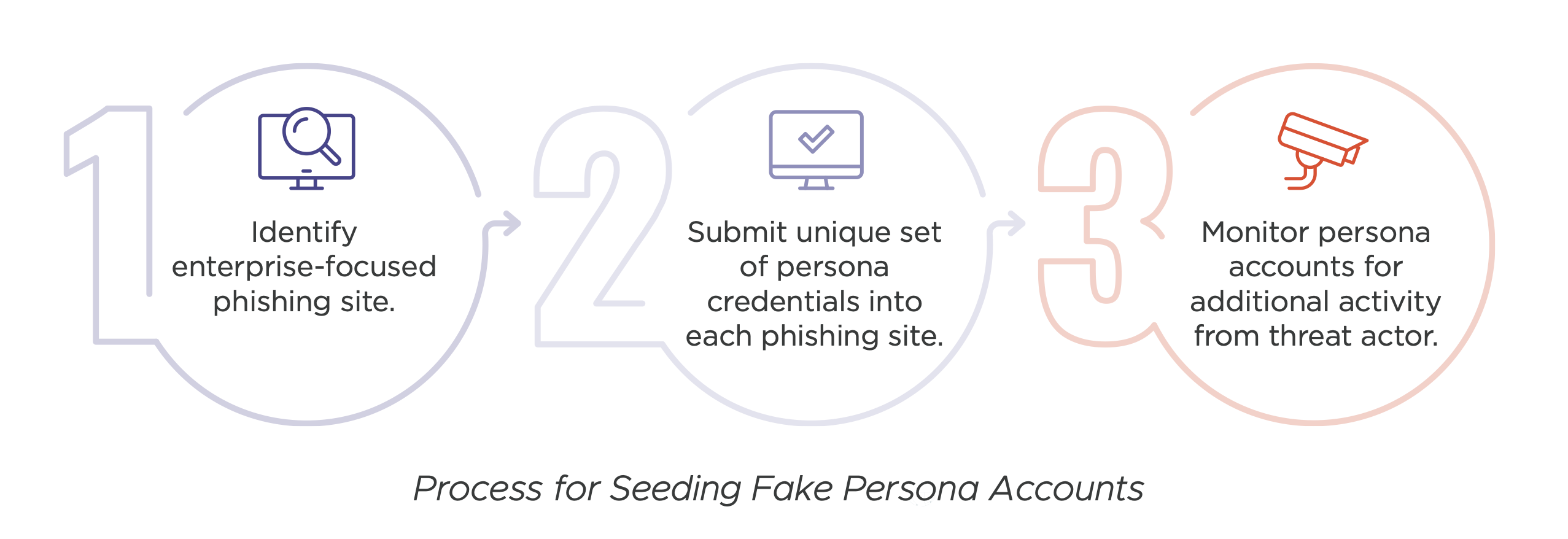
Cybercriminals collect email account credentials or user client access via phishing attacks or purchase credentials over the dark web. They continue to harvest credentials until they strike their attack.
Initial Compromise
Cybercriminals collect email account credentials or user client access via phishing attacks or purchase credentials over the dark web. They continue to harvest credentials until they strike their attack.
PHASE 2: Control
Establish Persistence
The attacker logs into the compromised account and changes account passwords or sets up a mail forwarder to establish control.
Establish Persistence
The attacker logs into the compromised account and changes account passwords or sets up a mail forwarder to establish control.
PHASE 3: Infiltration
Log in & Lay Low
The attacker monitors account activity and waits patiently to hijack important conversations amongst high-profile individuals.
Log in & Lay Low
The attacker monitors account activity and waits patiently to hijack important conversations amongst high-profile individuals.
FINAL RESULT: Exfiltration
Depending on the type of con, the cybercriminal reaps its reward of full access – either the target's credentials are captured, their sensitive data is ransacked, or stolen funds are retrieved—all under the guise that the attack came from a legitimate user.
Depending on the type of con, the cybercriminal reaps its reward of full access – either the target's credentials are captured, their sensitive data is ransacked, or stolen funds are retrieved—all under the guise that the attack came from a legitimate user.
How Can You Prevent Account Takeover Attacks?
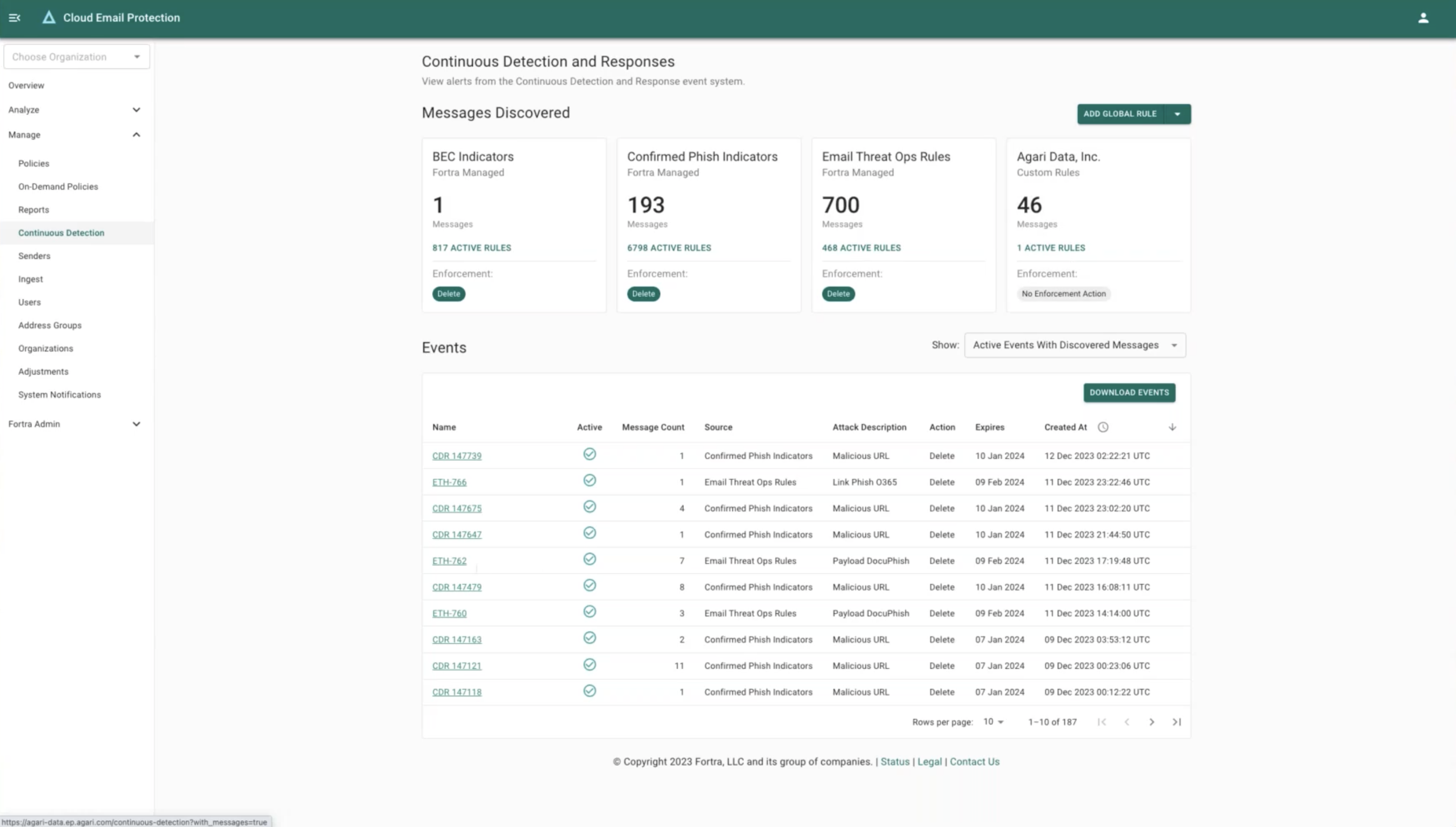
Account Takeover Discovery
Detecting unauthorized users in legitimate email accounts or user clients is critical to defending against account takeover-based attacks.
Leading account takeover solutions understand the complex information behind the email message and analyze expected behaviors between sender and recipient to accurately determine if a message from a previously established email account should be trusted. With protection for both internal and outbound email, you can obtain 360° security for all advanced threats.
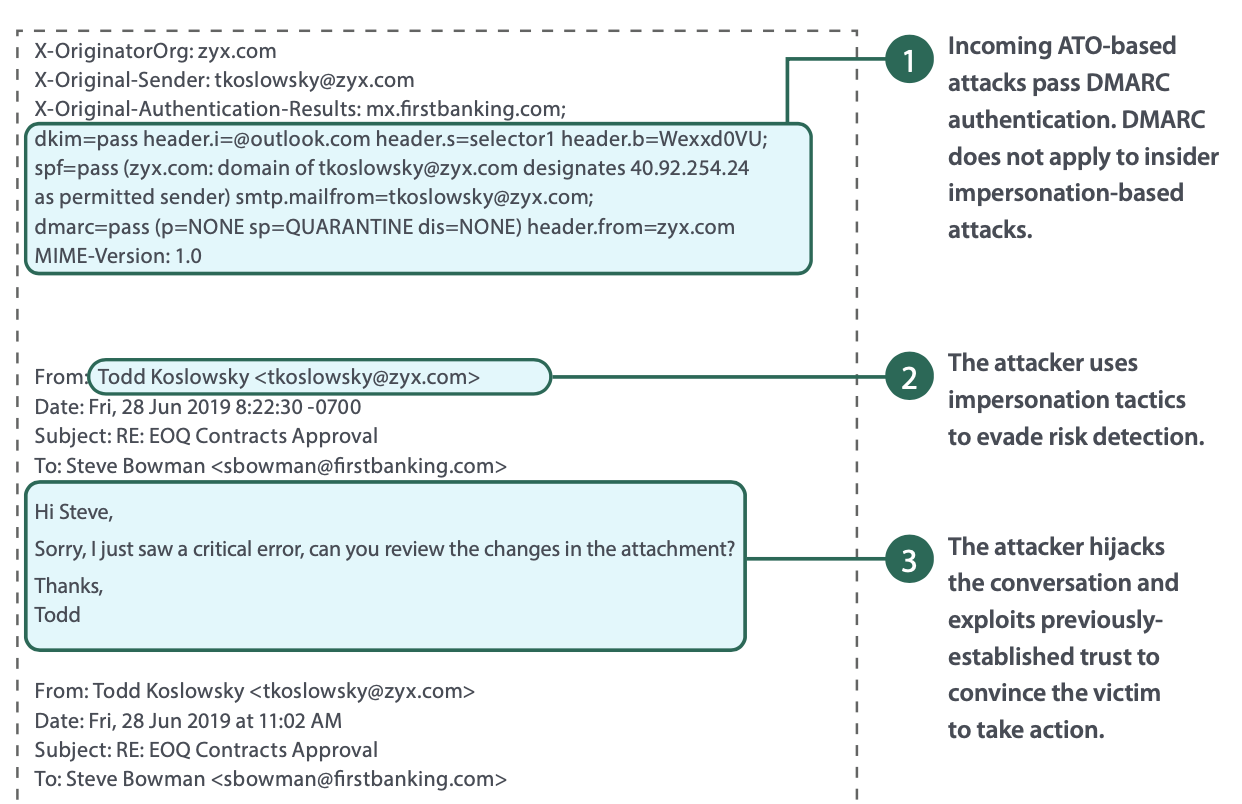
Account Takeover Prevention
Convincing people into downloading malware or logging into a fake website is core to an ATO-based attack. Identity deception makes it difficult for the victim to know if the sender has malicious intent, and advanced attacks hijack the conversation at appropriate times so the recipient never suspects anything.
Leveraging advanced data science and machine learning models, Fortra Email Security solutions can spot anomalies and patterns that differ from the norm. Emails can be blocked based on the severity of divergence to ensure untrusted email never reaches the inbox.
Growing Smarter Every Day
It’s not enough to react and detect attacks from a compromised account, but to prevent and deter them before they strike. When phishing attacks are identified early, businesses can protect valuable customer information and reduce the risk of account compromise.
By combining best-of-breed services from Fortra, the Customer Phishing Protection product bundle stops domain spoofing, detects phishing campaigns, and mitigates the infrastructure threat actors rely on.

Even though your business may not have seen a threat, Fortra likely has. And because we're already at work protecting organizations worldwide, our platform grows smarter and more effective each day.
See Cloud Email Protection In Action
Integrated cloud email security platform that combines AI, threat intelligence, and automated remediation to stop threats that bypass traditional defenses.