Unfortunately, there are numerous inherent complexities of DMARC (Domain-based Messaging Authentication & Reporting) and it takes more than the average layperson to know what they are and how to find them. If you remember the ‘90s online game, Acrophobia—which had players brainstorming new acronyms—or even if you don’t . . . the fear of acronyms can be real.
For one, DMARC can fail based on the configuration of your alignment mode. Then for full DMARC authentication to occur, either SPF or DKIM needs to be aligned but they each have their own alignment modes that can be set to either “relaxed” or “strict” and if you set either of them incorrectly, authentication can fail. But once your authentication protocols align and DMARC is all set up correctly, then the fun of plowing through all the DMARC reports begins!
Reading (DMARC Reports) Is Fundamental. . .
Why is it so important to analyze DMARC reports?
Well, it makes it so organizations can detect malicious emails and prioritize source configuration, all of which is crucial for maintaining their email security and reducing the risk of unauthorized access to sensitive data.
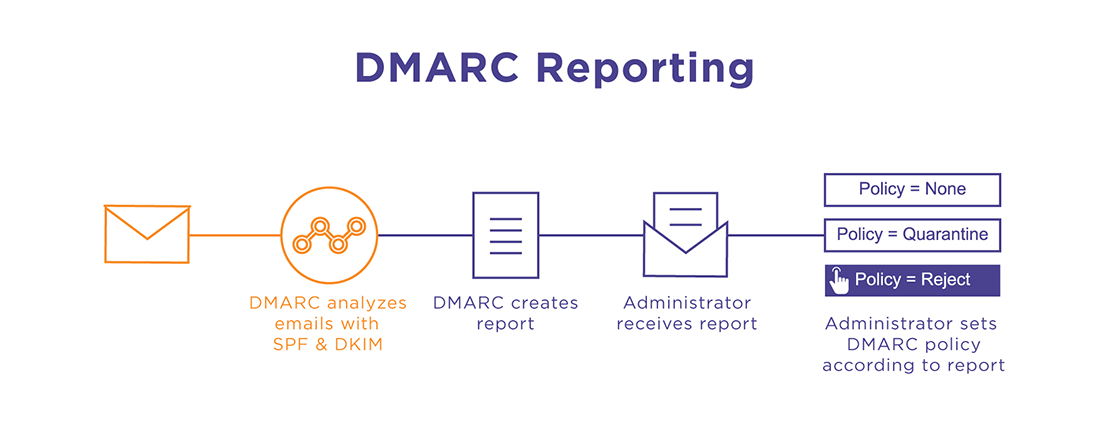
Basically, DMARC reports allow you to see which emails on your domain are passing DKIM (DomainKeys Identified Mail), SPF (Sender Policy Framework), and DMARC checks. Monitoring your mail flow from your DMARC report allows you to update your DMARC policies with stricter enforcements gradually, further strengthening your protection against spoofing attacks. We all think that having more information at our fingertips is good – however, most enterprise organizations will see several hundred DMARC reports per day so it’s important for you or your IT team to be able to read and understand them!
. . .Understanding Them Is Resoundingly Difficult
There are two types of DMARC reports, both of which come in machine-readable file formats–DMARC Aggregate (RUA) and DMARC Forensic, or Failure (RUF)–and they are generated based on how much email your domain sends.
RUA Reports
RUA reports contain information regarding the authentication status of messages sent on behalf of your domain and show which messages are passing DKIM and SPF validation, and which ones haven’t. These details include the domain used to send the message, the IP address the message was sent from, the date, and the result of the DKIM/SPF authentication check. These reports can identify spoofing attempts, as well as outline or inform future “reject” policies.
RUF Reports
RUF reports contain information when an email sent through your domain fails either DMARC, SPF, or DKIM validation. Since they contain more message details including the subject, the full “From” address and URL, they can help you identify the source of these messages and even fix the issues. RUF reports are valuable for both troubleshooting deliverability issues, as well as identifying sending IP addresses of attackers who are actively attempting to spoof your domain.
It’s common practice for organizations to start off with their DMARC policy set to none, then move to quarantine, and ultimately a policy of reject. This strategy gives you time to fully review your DMARC reports and adjust accordingly without the risk of accidentally impeding legitimate mail flow. Lastly, it’s best to set up a dedicated mailbox specifically for DMARC reports. This helps keep the reports organized and doesn’t overwhelm a shared inbox with a constant deluge of messages to sift through.
Need to get to DMARC enforcement as a destination? Use this tool to look up your record to start!

