Social media threats targeting enterprises more than doubled last year. Attacks on the retail industry specifically have grown, as threat actors are targeting victims with impersonation and counterfeit ad campaigns.
Purchasing behavior is increasingly influenced by social media, making it an attractive vector for these kinds of campaigns. The tendency of social media users to consume information rapidly and not apply the same levels of scrutiny as they would for other communication channels like email can lead to widespread brand damage and revenue loss.
In this post, we take a look at impersonation and counterfeit ad campaigns targeting retail on social media.
Impersonation
According to PhishLabs’ Q4 Threat Trends & Intelligence Report, impersonation was associated with 86% of all social media attacks targeting retail organizations. Impersonation is used to enhance the credibility of attacks, help actors evade detection, and extend the longevity of campaigns. These organic attacks include the abuse of logos, copy, images, and other IP.
The increased presence of retail brands on social media makes it easy for threat actors to collect trademarked data and repurpose it in the form of fake pages, posts, messages, and more. Below are two examples of fake social media pages using the name, images, logos and content of legitimate retail brands.
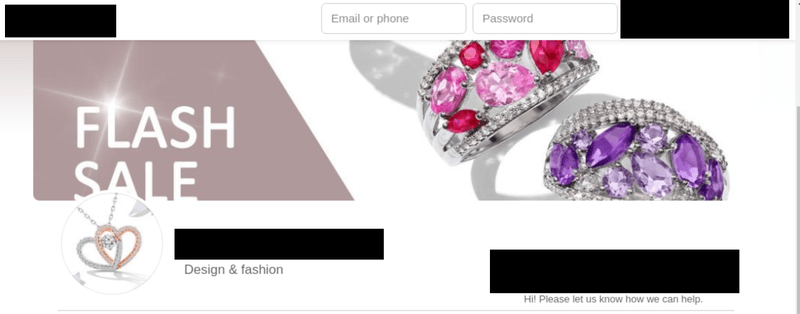
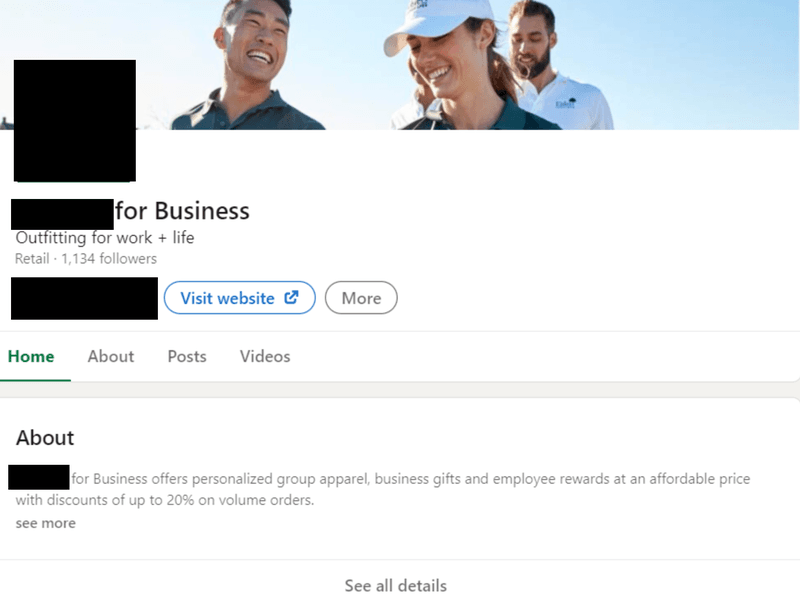
Counterfeit Ad Campaigns
Cybercriminals are increasingly incorporating paid social media ads into multichannel counterfeit campaigns. These sponsored ads are built through falsely-branded business pages and use the stolen content and official images of retail brands. When a victim clicks on one of these ads, they are routed to a malicious website selling counterfeit goods.
Social media sponsored ads are attractive to threat actors because they are low-cost, easy to launch, and can be targeted to a preferred audience based on age, location, behavior, and more.
Below are two examples of social media ads being used in counterfeit campaigns.
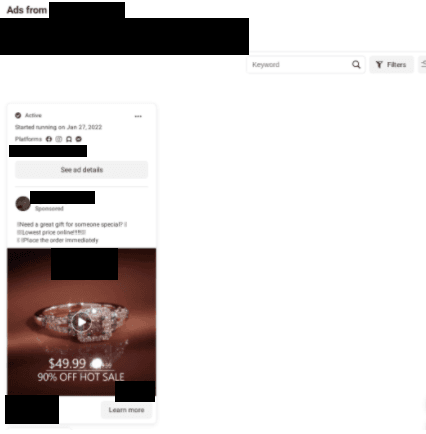
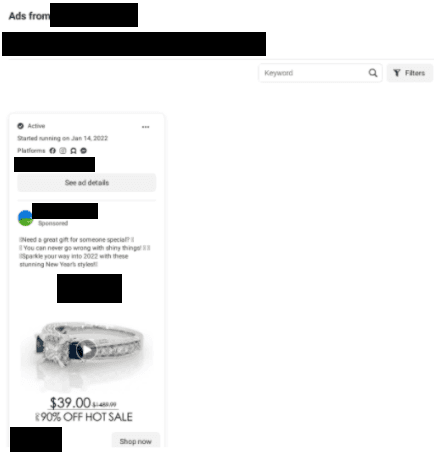
Retailers are being targeted more than ever on social platforms, and the negative consequences of an attack can be far-reaching. The fast-moving nature of social media is desirable to threat actors, as users communicate information rapidly compared to channels with more stringent security standards. This means stolen content used to impersonate legitimate brands via social pages and targeted ads can often pass as real without arousing suspicion.
In order to minimize the threat of social media attacks, security teams should invest time learning the unique policies and procedures platforms require to remove suspicious content.
Discover how we can work for you
Find out how we can help with your organization's policies to help minimize the threat of social media attacks.