Imagine going to the doctor and only being able to say “pain” or “sick”. You can’t say where you feel the pain, or what type of pain, or what is making you sick. Without this information, it is nearly impossible for the doctor to know how to treat you. From a cybersecurity perspective, this is very much like calling every email attack a “phishing attack" or even a “hack”. It limits the ability to identify proper countermeasures, and it frustrates meaningful comparison between potential approaches.
With cybercrime on the rise, threatening individuals, enterprises, and governments, it has become vital for the security industry to establish a common way of talking about the problem. It is our responsibility to enable organizations and their information security teams to clearly convey their concerns and request guidance matching their needs.
To address this need for a common language, Agari has developed a classification system for types of cyber threats—a threat taxonomy—that breaks down common email attacks in terms of how they are carried out, and what the attackers wish to achieve. At the same time, this taxonomy serves as a guide for enterprises and organizations with a need to enunciate their security concerns and priorities. While the taxonomy is not in any way limited to Agari’s solutions, it is currently limited to attacks leveraging email or other types of messaging.
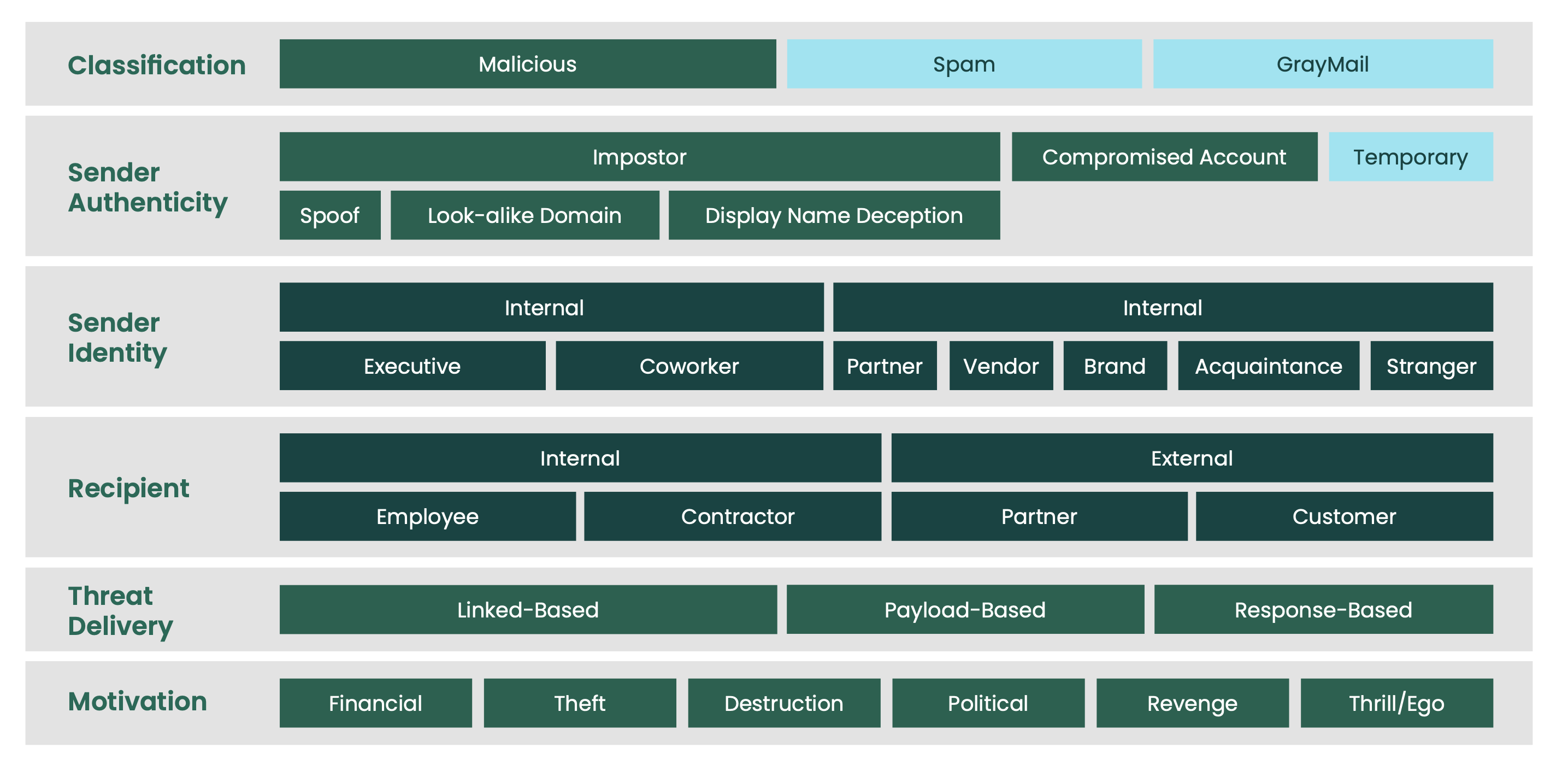
The threat taxonomy describes communication-related threats from various perspectives or dimensions. It starts by considering the classification of the message: Is it a malicious message? Or is it simply an unsolicited message such as spam or gray mail? Next, the taxonomy looks at sender authenticity. If the sender is not who they say they are, is that person using an imposter email address, a compromised account, or a temporary account? Using these two dimensions alone, many of today’s common threats can be described in a straightforward manner. Additional dimensions detail the sender identity, recipient, threat delivery, and motivation.
As an in-depth description of the threat taxonomy is beyond the scope of this post, we can instead provide an overview of certain aspects that many of our customers have expressed an interest in. We do this by describing two common types of email-based attacks using the taxonomy: business email compromise (BEC) attacks and targeted attacks using compromised accounts, known as account takeover-based (ATO) attacks.
The Threat Taxonomy and BEC Attacks
BEC attacks were virtually unknown a few years ago, but have since risen to become one of the most prominent email-based threats—the FBI estimates these attacks are responsible for more than $26 billion in exposed dollar losses over the last five years. This dramatic rise can be explained from several perspectives. One is that it is a targeted attack, meaning that the volume is low and the individual variation is relatively high, making the use of methods based on blacklisting largely irrelevant. This means that traditional security technologies simply don’t apply, leaving most mail systems vulnerable—which means, in turn, that the malicious emails will be delivered.
A second reason is that these attacks take advantage of existing workflows and mimic business-as-usual conversations, making them instantly credible. In one common version of a BEC attack, the criminal simply creates a free webmail account and sets the display name to match the party he or she wishes to impersonate. Since reputation-based email filtering methods will typically deliver all emails from webmail accounts—except those that have been observed to spew millions of unwanted emails—malicious BEC emails are almost always delivered. And since most users, even when being careful, rarely look further than the display name when determining who an email is from, this type of identity deception is successful.
Now, let’s use the threat taxonomy to restate what we just said: Consider the first dimension of the taxonomy: classification. Since BEC attacks are inherently malicious, this is an easy one. Next, the sender authenticity can be an imposter, since these attacks commonly use display name deception. However, we have kept all our options highlighted here as BEC can take any form of sender authenticity. Looking at sender identity and recipient, we know that these emails are typically sent from a trusted source, such as an executive or partner, and they are sent internally to employees. Next, threat delivery showcases a response-based email. While typical consumer phishing emails contain URLs, and many ransomware attacks have attachments, cons like BEC attacks have neither as they typically look to receive a response from their target.
As such, they are commonly harder to detect—especially for security vendors that use the approach of blacklisting URLs or attachments known to be bad. Turning to the last dimension of the taxonomy, motivation, it is clear that the BEC attacks of today are either aiming to steal funds (financial) or data (theft or destruction). A common type of data that BEC criminals aim to steal is W-2 data and/or other personally identifiable information.
The Threat Taxonomy and ATO Attacks
While the account takeover-based attack is relatively uncommon, it is increasing dramatically in commonality due to its abilities to circumvent all traditional countermeasures, whether the technique is used to infiltrate victim organizations, plant ransomware, or steal sensitive data. This is because if the criminal uses compromised accounts as launchpads to attack the contacts of the users whose accounts were compromised, the intended victims receive emails from people they have interacted with in the past.
Typical security solutions implicitly assume that this is “good” email traffic—almost independently of the content of the email—which means the malicious emails get delivered. And if the attack is crafted in a cunning manner, the users receiving these emails believe these messages are secure—and either open the attachments or follow the instructions that they would have ignored if the email came from a stranger.
The most common type of email compromise involves a user getting phished. For concreteness, let’s say that Alice receives an email that looks like it comes from her email provider, and it instructs her to log in, maybe under the premise that unwanted access attempts have been made such as in the 2016 John Podesta attack. As Alice “logs in”, the attacker steals her password.
The attacker automatically searches Alice’s email communications and determines that Alice interacts with Bob, a very wealthy businessman. And now, the attacker sends an email from Alice’s account to Bob, saying “Sorry about the long wait! I just realized that I never got around to sending this. Talk to you soon!” … and then attaches a file, that when opened, will put ransomware on Bob’s computer.
In this scenario, the classification of Alice's email is malicious since the attacker is using it to wreak havoc on Bob. The sender authenticity is a compromised account since this is an actual account used by someone Bob knows—someone with an internal/coworker sender identity. Since this is ultimately a ransomware attack, the threat delivery is payload-based with a motivation of financial gain.
Using the Threat Taxonomy
In conclusion, there are many different email-based attacks. Their similarities and differences are best understood by breaking down the nature of the attacks, which can be done using the taxonomy we describe above. We have shown how to describe two important attacks using this taxonomy—BEC attacks and ATO attacks. These, of course, are just two examples. As cybercrime continues to grow, we'll uncover new ways that criminals use email to target their victims, and continue to update this taxonomy.