As email scammers become more sophisticated and cybercriminals expand their tactics, phishing and BEC attacks from compromised email accounts continue to rise in popularity. We’ve seen a 35% increase in attacks launched from compromised accounts in the last six months. This means that email account takeover-based threats are more prevalent than ever before. And since this is the hardest attack type to protect against, these threats are only going to become more dangerous.
Compromised Email Accounts Aren’t the Worst of It
Making this problem even worse is the fact that once a cybercriminal has gained access to one account, it is fairly easy to move from account to account within your organization, scamming other employees out of sensitive information and their own account credentials. Imagine a scenario where a cybercriminal gains access to an email account run by a member of your finance department.
With only a few clicks, he could establish persistent control of the account without ever alerting the victim and continuously monitor activity—preparing for the right moment to strike. Then, when he sees the opportunity, he can easily and quickly launch a targeted email attack against the contact list of the controlled account. The type of targeted email attack will be dependent on his previous reconnaissance and could consist of a business email compromise scam to extract funds or a spear-phishing campaign to gain a deeper foothold into the organization.
Perhaps most concerning is that once the attacker has access to the account, he can move laterally throughout the organization, accessing private information through systems like OneDrive and SharePoint and even using the same account credentials to log in to financial systems and divert money.
Introducing Insider Impersonation Protection
Legacy systems simply cannot protect against this type of threat. Since they launch from trusted internal accounts, they bypass email authentication, secure email gateways, and other security controls. Few security systems have the ability to inspect east-west internal traffic, and even fewer have the advanced machine learning algorithms needed to successfully detect a malicious email from a compromised account.
Today, that changes with the introduction of insider impersonation protection technology, a new capability available in Cloud Email Protection. With this inclusion, Cloud Email Protection is the only product on the market that simultaneously scans incoming, outgoing, and internal employee-to-employee email traffic to detect and prevent advanced email threats—including account takeover-based attacks.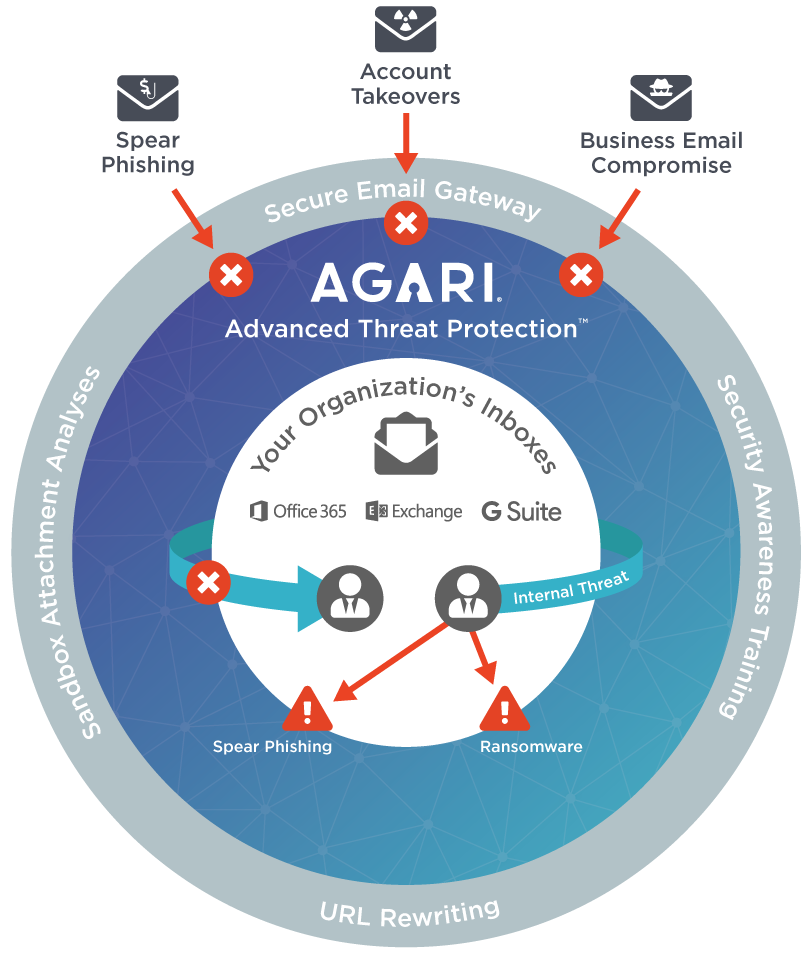
Insider Impersonation Security Gap
Recent analysis from Osterman Research shows that 49% of organizations do not have the right tools to stop insider impersonation attacks, despite the fact that these threats account for the majority of issues with which security teams must contend. Because of their difficult-to-detect nature and the fact that they exploit the trust humans have in their previously established relationships with coworkers, compromised accounts can do serious damage—until now.
By applying the three phases of the Agari Identity Graph™ to determine if the email is legitimate, no matter where it originates, Cloud Email Protection can automatically remove or quarantine malicious emails and provide notifications for outgoing threats. By scanning both outgoing and internal email traffic, this technology effectively prevents the lateral spread of malware, ransomware, and spear-phishing attacks—keeping you safe from data breaches, financial loss, and other threats.
Discover more about how Cloud Email Protection protects your organization from advanced email attacks.