At Agari we often talk about the evolving nature of advanced email attacks and the identity deception tactics that go with them. These attacks bypass legacy controls and like a magician delighting a curious audience, they trick the human psyche by targeting core human emotions such as fear, anxiety and curiosity. Of course, the magic in this case comes with ill intent.
A good example of a sophisticated attack and one that we address in the Agari Fall’19 release is the use of email with voice message attachments to execute phishing schemes.
How Voicemail Phishing Attacks Work
A plain text email sent by a cybercriminal sails right through the secure email gateway (SEG) and lands in an employee inbox. It might contain what looks like a partial transcript and for Office365 environments might come with an EML file attachment. These attachments can contain hyperlinks and attachments and are blocked less frequently by the SEG.
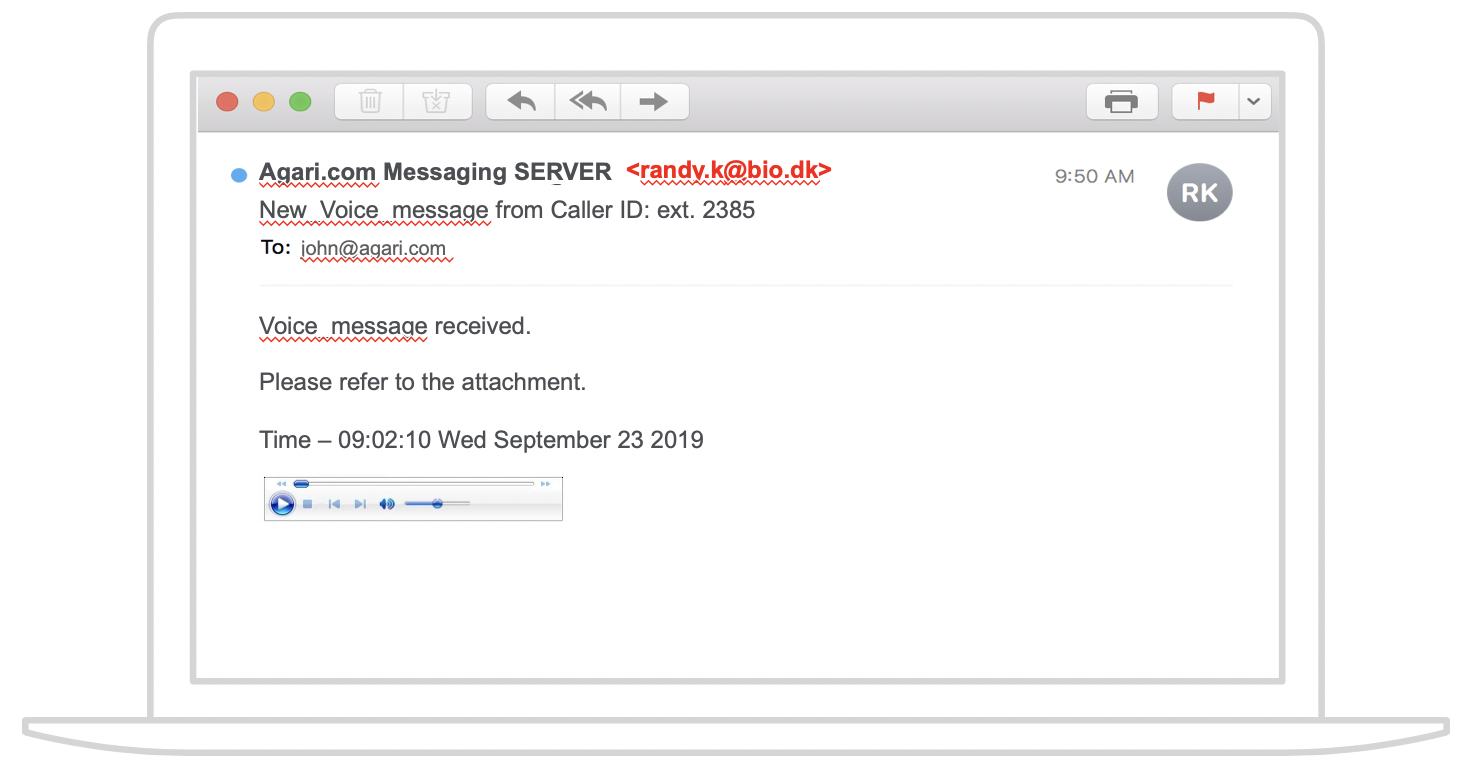
With a click of the attachment, Outlook displays a preview. Since it’s not a full window, users often click on a link to explore deeper.
With curiosity spiked by the transcript and preview, the user is then directed to a page that looks like a Microsoft account login page, and is prompted to authenticate with their user id and password to hear the message. Often, the initial login is designed to fail on the first try. The user, now chasing escalating curiosity then re-enters their credentials and typically gains access to an innocuous message that seems all but irrelevant.
The message of course is designed to be useless, but to raise little suspicions about the fake login that just happened. With the successful ruse tucked away in their consciousness, workers then move on all the while unaware they’ve just given log in credentials to a cybercriminal. Their email account has been compromised along with any files or business systems that use the same credentials. The threat actor is then free to monitor communications, peruse systems and files authorized to the legitimate user and to execute targeted email account-takeover based attacks.
Is this a security breach or a human fail? Well, cyber insurance companies might care, but the impact on the target organization is largely the same.
Organizations convinced of the latter often look to cybersecurity training, which can work maybe 98% of the time in a best-case scenario. This is a bit like training an audience to spot a magician’s trick. Show them the tactic, and they can readily spot it a second time. Show them something new and novel, and the human detection rate falls dramatically.
The problem of course is that like magicians, cybercriminals always come up with new tricks. But in cybercrime, the delight and laughter comes from the threat actor at the victim’s expense.
The Agari Fall ’19 release trains machine learning on this problem. Using our highly innovative identity graph to detect convergence or divergence to known emails and sending behavior, Agari detects these ever-evolving attacks in a way humans and legacy systems cannot because it’s looking for good behavior, not bad signatures.
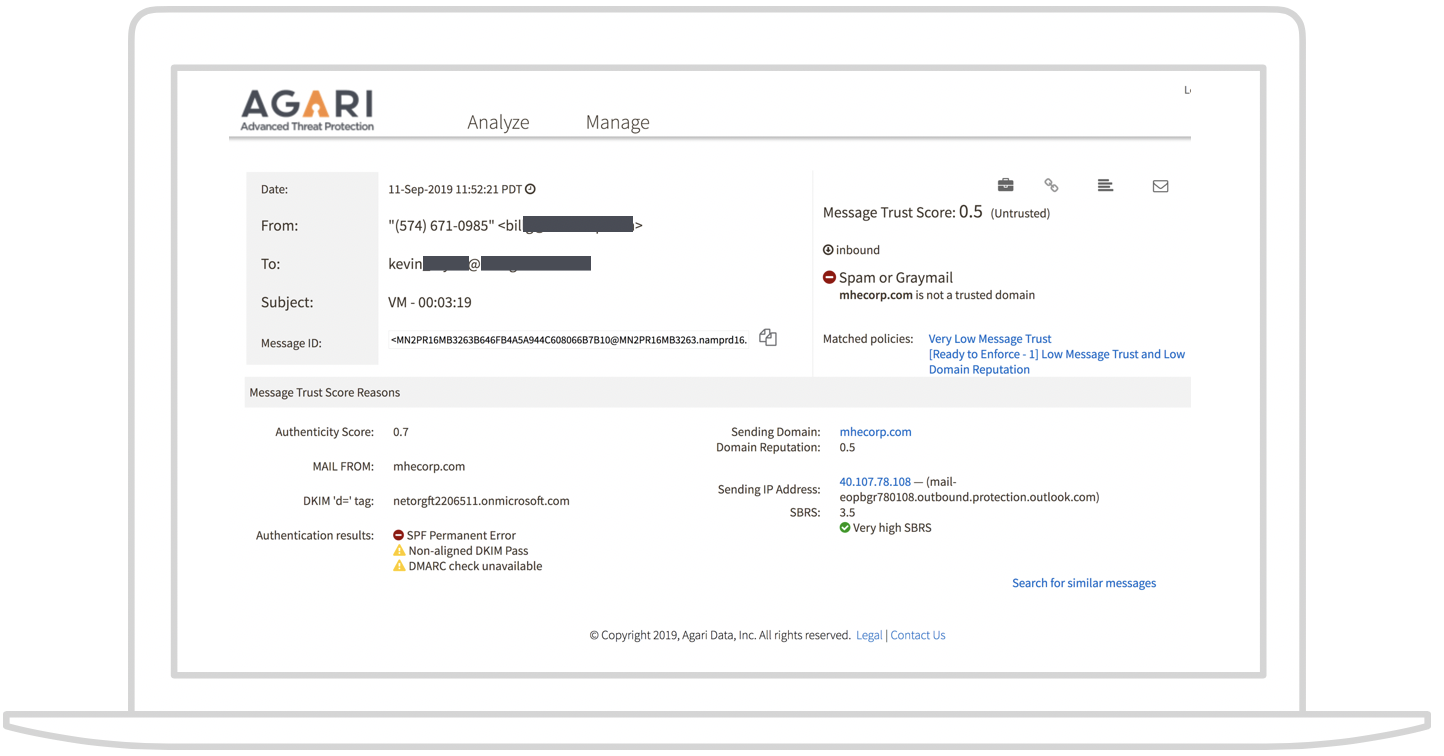
Like other attacks that target human emotions, the ruse obscures the scam, but the scam gets detected by email forensics. This is why enterprises need a dynamic approach that models identity and behaviors versus a static approach that looks for attacks matching previously detected patterns.
By dynamically modeling messages as they arrive globally on a scale of around 2T messages annually, new messages are evaluated in context of an entire global distribution of human-labelled messages. This enables attacks to be detected and stopped in real time and takes employees out of the direct line of fire of advanced email attacks.
Learn how Cloud Email Protection stops 99.987% of the attacks that secure email gateways missed.