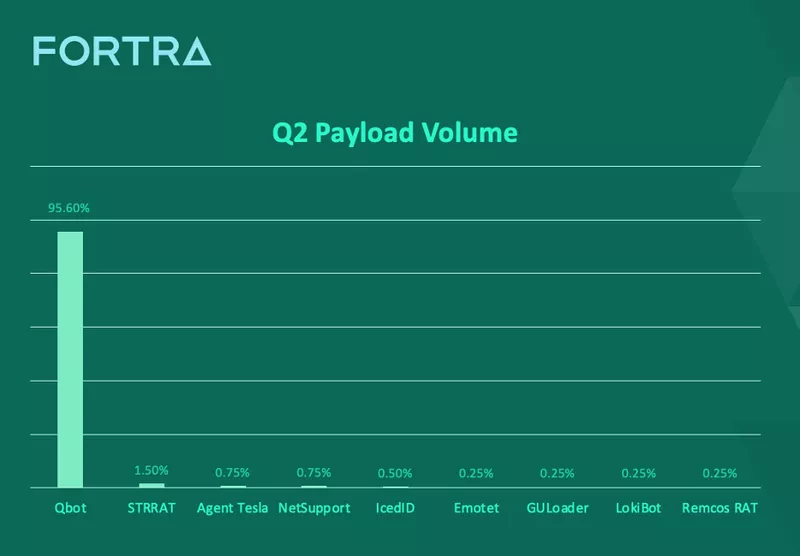
QBot dominated as the top payload in Q2 with more than 95% of reported volume, according to Fortra’s PhishLabs. This is the third consecutive quarter QBot has led all other malware varieties by a significant majority. QBot was also consistently reported as a top payload in 2022, falling second only to Emotet and Redline Stealer before its current streak.
Email payloads remain the primary delivery method of ransomware targeting organizations. PhishLabs continuously monitors payload families reported in corporate inboxes to help mitigate attacks targeting their businesses. Below are the top payload threats to enterprises in Q2.
QBot
QBot led all other reported malware varieties in Q2, with nearly 96% of attack volume. Former banking trojan turned dropper, QBot operators continue to make the malware more resilient with enhancements to the QBot architecture..
Most recently, QBot operators have been observed using compromised residential IP spaces for short periods of time as C2 servers to exfiltrate data or download additional malware.They also sell access to infected systems to other cybercriminals. Bot recruitment is achieved through email attack campaigns, where actors have traditionally played with a variety of file types to achieve successful delivery of the malware, including HTML smuggling, .zip files containing LNK files, and DLL hijacking.
QBot is also considered highly evasive, with several anti-VM and anti-analysis tools that help bypass security controls.
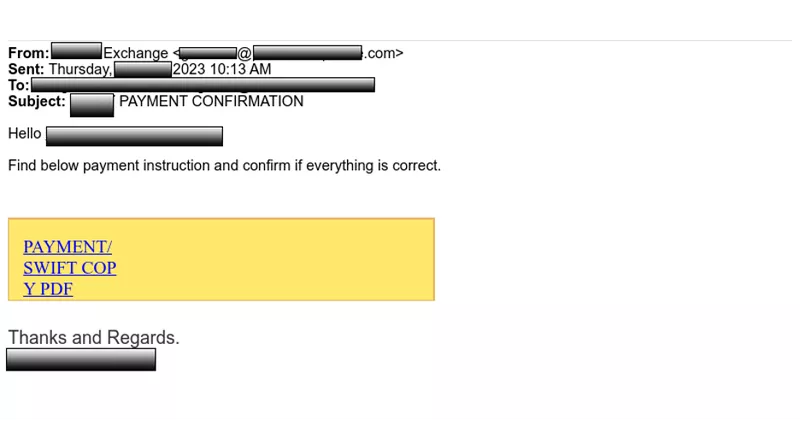
Below is a phishing email delivering a QBot attachment. The attackers were targeting a large energy company.

STRRAT
In Q2, STRRAT malware was the second most reported payload by end users with 1.5% of attack volume. STRRAT is a Java-based information stealer and backdoor that was first detected in 2020. This is the first time since reporting on payload data that STRRAT has been among the top reported incidents.
STRRAT is a multifunctional tool capable of logging keystrokes, stealing credentials, and remote control of infected devices. Notably, STRRAT will masquerade as a ransomware but lacks encryption capabilities.
The below is a phishing email delivering the STRRAT payload via a malicious link. The attacker was targeting a national automotive retailer.
Agent Tesla
Agent Tesla was reported 0.7% of the time in Q2, making it the third most reported payload. Originally advertised as a legitimate remote access tool in 2014, Agent Tesla has since proven to be a popular malware-as-a-service (MaaS) used for credential harvesting.
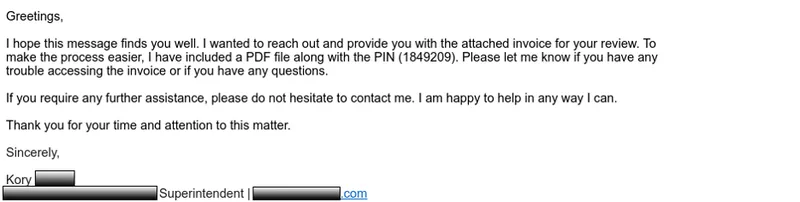
Agent Tesla is capable of screen grabbing, data exfiltration, keylogging, and the ability to steal clipboard data. The phishing email targeting a global financial institution below delivered Agent Tesla via attachment.
QBot continues to dominate payload volume in 2023 with the vast majority of malware campaigns containing a QBot attachment. QBot operators, in addition to other cybercriminals, are continuously changing file delivery and testing evasion techniques to improve their odds of a successful attack campaign. PhishLabs continuously monitors payload activity so that organizations may better prepare for and prevent these types of attacks.
Learn how PhishLabs can help protect against malware attacks.
