According to a recent Cloud Security Alliance report, 98% of organizations worldwide use cloud services, including SaaS applications, complete cloud-native networks, and email services. It’s an overdue modernization that eliminates physical infrastructure to drive cost savings and integrate services for improved productivity
Chasing this move, cybercriminals intent on account takeover are evolving their tactics, targeting end users with various identity-based deception scams. Their evolving tactics and your defenses against them deserve a closer look.
Email is still the primary vector used by phishers to attack enterprises and consumers. And Microsoft itself is still one of the top abused brands when it comes to impersonation email attacks.
Common spoofing tactics include malicious emails disguised as an Office 365 password update and an invitation to edit a OneDrive document linking to a spear phishing page. O365 customers can add Microsoft Defender to help identify malicious links, but cybercriminals are getting crafty and can weaponize those links after the email is delivered.
So on the one hand, implementing Office 365 can drive triple digit ROI. On the other, business email compromise and spear phishing can wipe out the most robust ROI with just one successful attack that results in an account takeover, unauthorized transfer of cash, or loss of intellectual property or sensitive information.
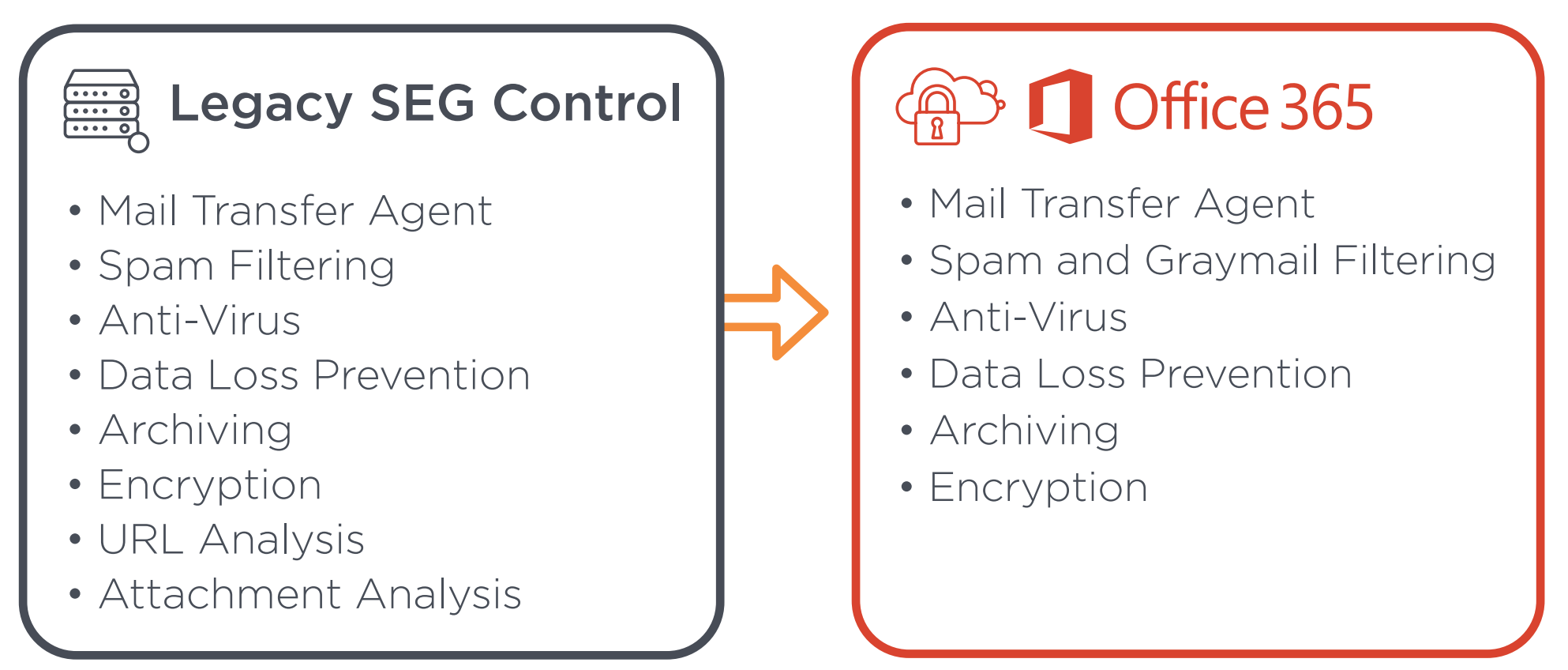
From LEG(acy) SEG to Microsoft Office 365
Particularly with the addition of Microsoft Exchange Online Protection (EOP) and/or Microsoft Defender, Office 365 is better protected than any platform that came before it.
Key capabilities such as anti-spam, virus/malware detection, data loss prevention and the aforementioned URL and attachment analysis traditionally found in the secure email gateway have been integrated as native capabilities in the platform. So with basic email security functions covered by Office 365, many organizations have eliminated their secure email gateway.
Meanwhile, attack sophistication has evolved from content-based techniques, such as malware and unsafe URLs, to crimes of identity deception that signature-based controls are ill-equipped to address. So, we are left asking – what solution out there can fill the gap?
Enter the Cloud Email Gateway!
Advanced email attacks can appear as plain text messages targeting basic human emotions such as fear, anxiety, and curiosity. These socially engineered attacks trick unsuspecting users into believing they are interacting with a legitimate person or service, when if fact they are being conned.
Fortra's Cloud Email Protection (CEP) delivers important capabilities to protect against identity deception attacks, secure the corporate email sending domain, and detect and respond to threats that have either evaded initial detection or have weaponized post-delivery, whether you have a cloud-based, on-prem, or hybrid email architecture. And new, just released capabilities allow CEP to also detect malicious QR codes and active executable codes in an email!
This is why enterprises who have adopted Microsoft Defender / Microsoft EOP are choosing to pair that investment with an integrated cloud email security solution (ICES) like Fortra's Cloud Email Protection. However, Fortra's Cloud Email Gateway differs in several remarkable ways from legacy security controls, especially when paired with the built-in controls of Office 365. Let’s peel back the layers.
Continuous Protection vs. Event-Based Detection
Through the power of AI and advanced machine learning, the Cloud Email Gateway fundamentally transforms email security from event-based inspection of incoming messages to continuous detection and response of newly discovered threats. This includes new messages as well as those that have already reached the inbox. This approach stops advanced email attacks including those that organizations have not seen before, and can delete messages from Office 365 inboxes that weaponize after initial security screening.
In this vein, Cloud Email Protection leverages a pre-train and fine-tune paradigm, adapting pragmatic pre-trained models to various downstream tasks, like:
- BRAND NEW: Extracts and analyzes URLs for any maliciousness
- ALSO NEW: Analyze the message body and attachments for presence of executable code
- Analyzes specific text-based email components, such as Subject Lines and body content
- Performs task-specific functions, such as determining message type or level of suspiciousness
- Identifies groupings or clusters in email data
- Creates data lakes with labeled data that can be used by other models
- And more!
CEP also automates the processes involved in Domain-based Messaging, Authentication, Reporting, and Compliance (DMARC), making it easy to authenticate messaging and reach enforcement. This prevents cybercriminals from impersonating the brand via email and the associated BEC attacks targeting employees (e.g., executive spoofing) and customers (e.g., customer phishing and fake invoicing).
The Benefit of Integrating Microsoft Office 365 with the Cloud Email Gateway
Fortra's next-generation Cloud Email Gateway has distinct advantages for Office 365 deployments and users. It’s a cloud-native offering that augments the native security controls found in Microsoft Defender for Office 365 / Microsoft EOP, and can remove messages from inboxes that have already passed initial security screening.
Learn more about the next-generation approach for email security.
Check out the Fortra Email Security + Microsoft Office 365 white paper.