One of the most popular attack strategies used by criminals to mislead consumers into doing the wrong thing is phishing. Phishing can occur via text message (SMS or instant messaging apps, coined SMiShing), social media or via phone, but email-based attacks are the ones most often linked to the term. It's easy for phishing emails to reach millions of users at once and to blend in with the many legitimate messages that consumers' inboxes are already flooded with. Phishing emails can target businesses of any size or industry. The attack could be part of a larger, global effort or could be the prelude to a more focused, sophisticated assault on your company designed to, for example, steal sensitive customer data.
Phishing by the Numbers in 2022
The ENISA Threat Landscape 2022 report highlights that: “Phishing is once again the most common vector for initial access. Advances in the sophistication of phishing, user fatigue, and targeted, context-based phishing have led to this rise.”
96% of phishing campaigns are sent by email, per the Verizon Data Breach Investigations Report. Meanwhile, Cisco found that in roughly 86% of companies, at least one employee fell for a phishing scam. Phishing attacks tend to increase by 52% on average in December alone, according to the same study by Cisco, which also indicated that phishing is more prevalent during the winter holiday season..
Login credentials, personal data, and health information are the top three categories of data typically stolen in a phishing attempt. Phishing, on the other hand, is the second most expensive cause of data breaches, with an average cost to enterprises of $4.65 million per incident. And Business Email Compromise (BEC) ranks first, costing businesses an average of $5.01 million per breach.
Phishing Defense Takes More Than One Safety Net
In practice, defense against phishing attacks is for employees to learn to have an eagle’s eye when it comes to spotting fake emails. However, the results of this tactic will be moderate at best. In addition, you need to augment your security architecture with additional safety nets—because when you do, your defenses against phishing attacks will be strengthened without negatively impacting your users' productivity.
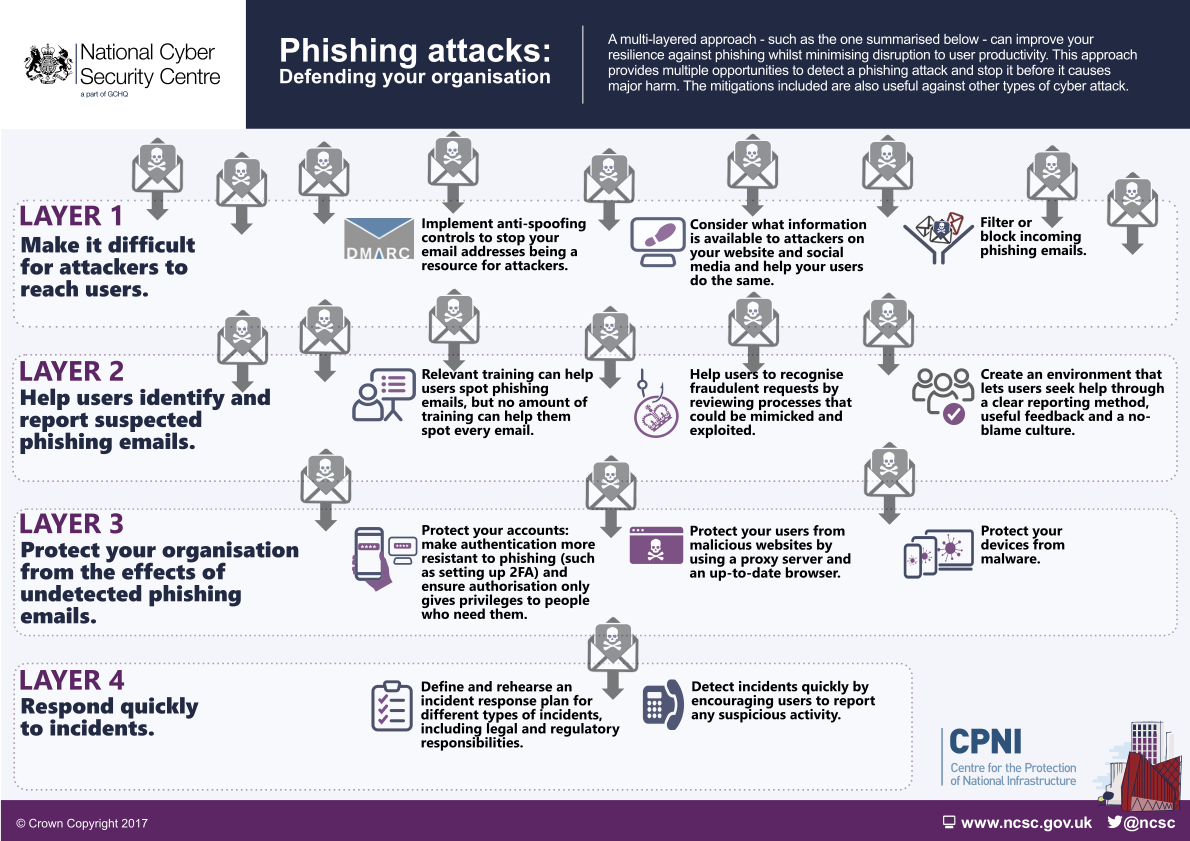
For example, UK’s NCSC suggests that a multi-layered approach to phishing defenses (see our related post in the series: “What Is an Enterprise’s Primary Line of Defense Against Phishing Emails?”) should consist of:
1. Complicate the path for attackers to reach your employees' mailboxes.
- Implement anti-spoofing controls, like registering business details with DMARC
- Filter or block inbound phishing emails using a dedicated email security solution supported by real-time intelligence
2. Identify for your employees how to identify suspected phishing emails and show them the process for reporting them.
- Provide training for the employees to spot phishing emails
- Help employees recognize processes that can be mimicked and exploited
- Create an environment where employees can easily seek help
3. Safeguard the company from potential harm caused by phishing emails that go undetected.
- Protect accounts with phishing-resistant multi-factor authentication (MFA)
- Protect employees from accessing malicious websites
- Protect devices from malware
4. Respond swiftly to reported incidents and close the feedback loop.
- Define and frequently rehearse an incident response plan
- Encourage employees to report any suspicious activity, and train them accordingly
These steps are essential because, as NCSC demonstrates, they can limit the potential impact of a successful phishing attack.
It is important to note that even if the targeted company had an email security solution in place, myriad phishing emails can still evade detection and reach employees' mailboxes. Hence, it is important to strengthen the second layer of defense—i.e., the human layer.
Helping Your Employees Recognize Phishing Emails Augments Your Defenses
The component of phishing defense that is sometimes underemphasized is providing proper training to your employees through phishing simulations and security awareness training. Without that, responding and clicking links within emails is commonplace, and with a lack of email security protection at the security architecture level, expecting individuals to be constantly watchful is unreasonable. In fact, no one is debating that it is challenging to recognize phishing emails, and spear phishing is even more difficult, and at one point in their careers or lives, most everyone will have been duped.
So when implementing training, make that evident right away and don't count on people being able to recognize them all the time. Also, never penalize individuals for having trouble identifying phishing emails; this is unwise for a variety of reasons. Employees who worry about retaliation will rarely, if ever, report errors. Thus, proper training will increase their desire to report future events and reassure them that it is acceptable to ask for more assistance when something seems strange or off. ALL departments across the enterprise must reinforce this message.
However, make sure that all your staff members, particularly those in departments that might be more susceptible to phishing attempts (such as HR which has access to confidential personnel information, Accounts Payable with access to financial accounts, or those areas restricted by compliance regulations) are aware of the dangers that phishing poses and provide them with specialized training or additional support. Because these types of employees or departments are more apt to be on attackers’ radar and may be the subject of more sophisticated spear phishing operations, whereas customer-facing departments may get enormous amounts of unsolicited emails, or those from unknown senders.
Spotting phishing emails can be hard, but it is achievable if you follow some of these tips.
Download our latest whitepaper, "A Window on Email Security," to learn more about the risks of unprotected email, and what you can really do about it.