QBot and Emotet payloads contributed to more than 93% of reported payload volume in Q1, according to Fortra’s PhishLabs. While QBot represented the majority of attacks, this is the first known activity by Emotet actors since 2022 and the largest spike in Emotet reports since Q2 of last year.
Email payloads remain the primary delivery method of ransomware targeting organizations. PhishLabs’ Suspicious Email Analysis solution continuously monitors payload families reported in corporate inboxes to help mitigate attacks targeting their businesses. Below are the top payload threats to enterprises in Q1.
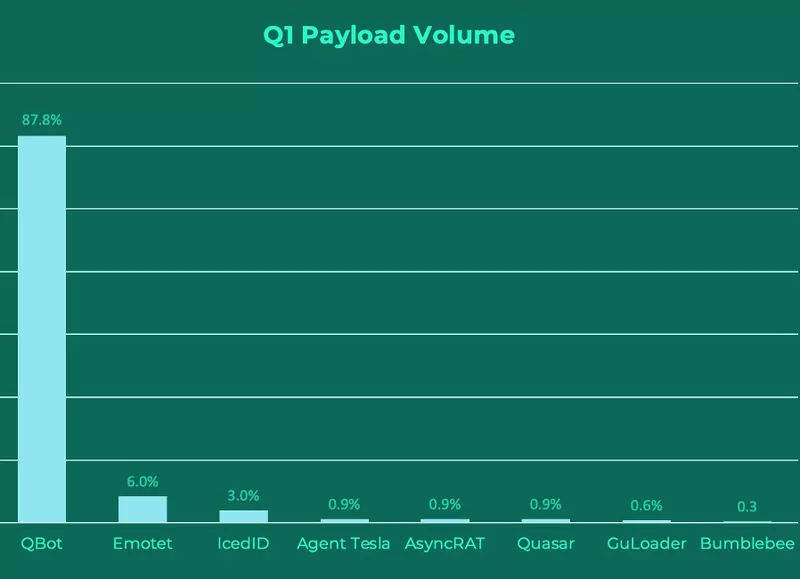
QBot
QBot (Qakbot) represented 87.8% of payload volume in Q1. QBot is a prominent information stealer and backdoor associated with ransomware actors Black Basta, Egregor, and Doppelpaymer.
QBot is primarily distributed via malicious attachments in email phishing campaigns, with operators regularly changing tactics to ensure the successful delivery of the malware. Most recently, OneNote and Adobe documents have been used to deliver QBot. It is also distributed in HTML smuggling campaigns.
QBot is capable of self-spreading, C2 communication, and sandbox detection, in addition to a host of other functionalities. This is the second consecutive quarter where QBot has led malware reports.
The below is a hijacked email thread delivering a QBot attachment. The attack is targeting a global financial institution and uses Email Subject: Account History.
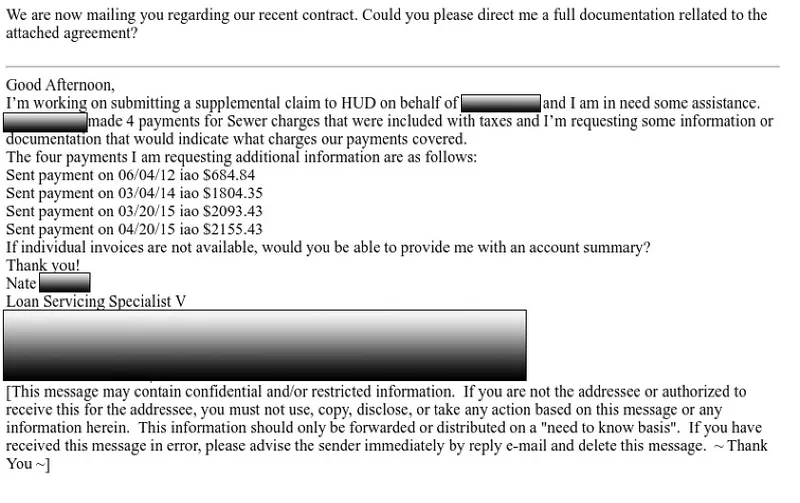
QBot Phishing Email
Emotet
Emotet represented 6% of payload volume in Q1, resuming operations in March after a multi-month hiatus. Emotet actors have previously halted operations for periods of time to add to or edit the malware’s functionality.
Emotet is a highly sophisticated and evasive malware that has been associated with ransomware families Ryuk and Conti. Emotet was considered one of the world’s largest botnets before its brief dismantling by authorities in 2021.
Operators are consistently enhancing the malware’s feature set and means of distribution. Recent Emotet campaigns are using binary padding as a way to bypass endpoint detection. This tactic involves inflating file sizes to exceed limitations imposed by anti-malware solutions.
Emotet Phishing Email
IcedID
IcedID was the third most reported malware family in Q1, making up 3% of payload volume.
Initially distributed as a banking trojan, IcedID operators have recently removed its banking functionalities. These changes allow newer variants to act as droppers for additional malware such as ransomware. Changes in malware functionality are common for malware families as priorities shift and new means of evasion are needed. The code updates to IcedID allow criminals to facilitate different types of attacks, thus expanding its user base in Ransomware-as-a-Service (RaaS) operations.
Recent IcedID campaigns have been distributed using OneNote documents in phishing campaigns.
The below is a phishing lure delivering an IcedID attachment.
IcedID Phishing Email
Malware continues to represent a significant threat to organizations. Damage associated with a malicious payload can range from network compromise, to harvested data or a ransomware attack. PhishLabs continues to monitor malware activity and tactics in order to better detect these threats and protect organizations from attacks.
Learn how PhishLabs protects against malicious payloads targeting organizations.
