The volume of malicious emails reported in corporate inboxes has reached a four-quarter high, according to the latest data from Fortra. These threats are largely composed of Response-Based, Credential Theft, and Malware attacks targeting employees.
Every quarter, Fortra analyzes hundreds of thousands of phishing and social media attacks targeting enterprises, brands, and employees. In this post we discuss intelligence collected through Fortra's Suspicious Email Analysis solution.
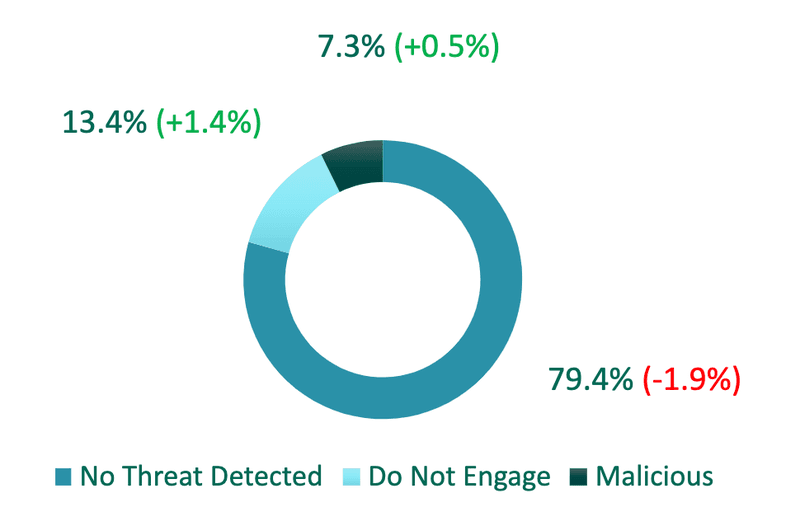
Q3 2022 Employee-Reported Emails
In Q3, end users reported the highest volume of emails categorized as Malicious or Do Not Engage in eight consecutive quarters, totaling more than 20% of share. Do Not Engage emails are considered suspicious yet lack specifically defined indicators that would classify them as malicious.
Malicious emails increased in Q3, accounting for more than 7% of overall volume. Emails categorized as Do Not Engage grew 1.4% and represented more than 13% of attacks. Emails with No Threat Detected declined 1.9% in Q3, and represented the majority of reports.
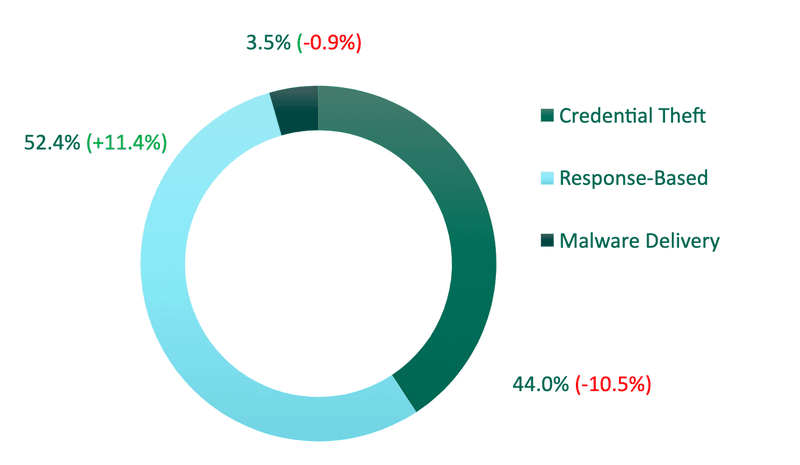
Threats Found in Corporate Inboxes
Response-Based Attacks
Of the malicious emails recorded in Q3, the percentage of Response-Based attacks reported in corporate inboxes overtook Credential Theft scams for the first time since 2020. The share of Response-Based threats grew more than 11% from Q2, to represent 52.4% of total threats. A large percentage of this growth can be attributed to the 15.5% jump in hybrid Vishing scams from Q2.
Advanced-Fee (419) Fraud, hybrid Vishing attacks, and Business Email Compromise (BEC) accounted for most Response-Based attacks. Advanced-Fee Fraud represented the top Response-Based threat type in Q3, despite declining 11.6% in share. This type of scam typically involves the promise of large sums of money if the victim agrees to pay a smaller amount up front. It is consistently the most reported threat-type within the group.
Hybrid Vishing attacks grew in share and count to nearly overtake Advanced-Fee Fraud in Q3. Barring a slight decline in Q1 2022, Vishing attacks have steadily increased since 2021 and more than doubled in count this quarter. Hybrid Vishing attacks incorporate phone numbers within email messages to entice victims to call and disclose sensitive data to fake representatives.
Business Email Compromise (BEC) attacks decreased in Q3, displaying the lowest percentage of share for the threat-type since 2021. Job Scams and Tech Support Scams represented 4.8% and 0.3% of share of Response-Based activity, respectively.
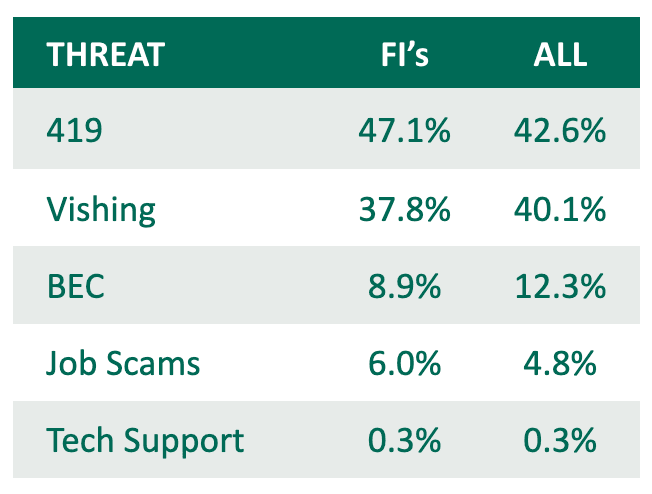
Q3 Top Response-Based Threats
Credential Theft
Credential Theft attacks contributed to 44% of attacks in Q3, after dropping more than 10% from Q2. Phishing Links represented more than three-quarters of Credential Theft attacks, despite declining 7.5%. Attachments accounted for 23% of attacks.
Credential Theft phishing links targeting Office 365 account credentials dipped in share and volume in Q3, after experiencing a six-quarter high in Q2. Despite this, O365 phish continue to represent the majority of Credential Theft volume, accounting for just over half of all phishing links. Compromised O365 credentials can provide broad system access to unauthorized individuals, making this specific login information highly sought after by bad actors.
Malware
In Q3, Redline Stealer led payload volume targeting corporate users, contributing to half of all reports. This is the first time since Fortra's reporting on payload families that Redline Stealer has stood among the top ten.
Redline Stealer, QBot, and IcedID combined to represent nearly 99% of all payload attack volume in Q3. Qbot has ranked either first or second among malware varieties for the past four quarters and contributed to more than 34% of Q3 share of volume. This is despite a decrease of 8.6% from Q2. IcedID reports were negligible in Q2 but jumped to represent 14.6% of share in Q3.
Notably quiet among reported payload families was Emotet, representing only 0.2% of activity.
Advanced email threats are increasingly making it past security controls and posing a risk to businesses and their employees. Attacks are continuously being adjusted by criminal operators to bypass email gateways and ensure successful delivery into inboxes. To prevent these attacks from being delivered, security teams should dedicate resources to the detection and analysis of relevant domain and email intelligence across online channels.
Learn more about how you can protect against advanced email threats and more with Fortra's Suspicious Email Analysis.
