In the second in our series of blogs on the Fundamentals of Phishing we will explore how to identify fraudulent emails.
Not that long ago, phishing attempts were quite primitive and often full of errors, and it was easier for consumers to identify when something was amiss. In addition, consumers weren’t accessing their inboxes from multiple devices and mobiles, nor did they expect to receive highly personalized emails detailing their transaction history with a company.
A recent example of email phishing illustrates how sophisticated today’s cybercriminals are in using social engineering to plan and execute phishing attacks. A highly publicized phishing attack centered on the US Federal Government’s Office of Personnel Management (OPM) data breach. In the wake of the breach, OPM issued a statement saying that email would be its primary form of communication with users around the breach. However, almost immediately after these emails went out, cybercriminals started distributing almost identical phishing emails.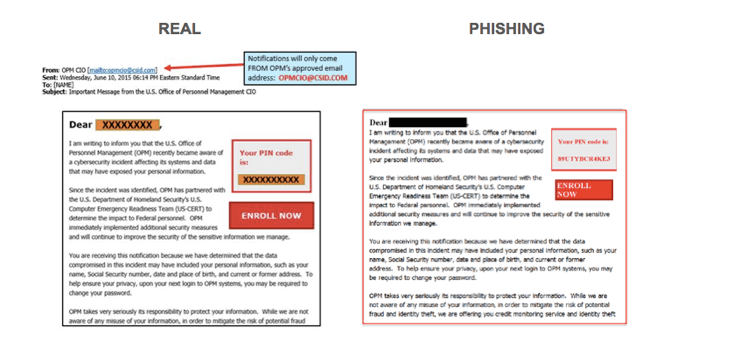
This example of phishing highlights some of the popular tactics used by cybercriminals. Taking advantage of the fact that OPM used a third-party domain, csid.com, fraudsters used something similar to convince users of email’s authenticity. In addition, since the OPM email address used was not secure, anyone could send emails claiming to be from it and recipients couldn’t tell the difference. Furthermore, OPM’s legitimate email included an “Enroll Now” button, prompting victims to sign-up for credit monitoring services. Savvy cyber criminals were able to include a similar feature that directed victims to a malicious website instead. The “Enroll Now” button could be used to obscure the link (which in OPM’s case was a long, questionable-looking URL) that meant receivers were unable to tell the difference between the real and phishing emails. In this particular example, the US Army flagged legitimate emails as a phishing attack.
As OPM’s experience shows, today’s cybercriminals are clearly highly sophisticated in the planning and execution of phishing attacks, leveraging social engineering tactics to get email receivers to do what they want, especially in times of crisis. To help consumers protect themselves from cyber attacks there are various organizations that are driven to educate the users on cyber safety. Stop.Think.Connect. is one such organization. It is a global awareness campaign that helps digital citizens around the world to practice safe practices online. The group encourages internet users to be more vigilant about their online habits.
The Stop.Think.Connect. message is perfect to keep in mind when checking your email:
- Stop: Pay attention when checking your email. If you have multiple emails and are viewing them on your phone, make sure to check each one closely - do not just blindly open them.
- Think: Take a moment to be certain the subject is legitimate. Make sure to notice red flags, such as messages that only contain links or attachments or a large amount of spelling and grammatical errors.
- Connect: Make sure you stay connected with the right people by filtering your email. Most providers allow you to pick and choose who should be considered a high priority, and will filter unknown names into another folder.
You can also practice a few additional email safety tips to keep yourself secure:
- Don’t be afraid to hover: Hovering over the sender’s name will bring up the domain the message is sent from, so if you don’t recognize the domain, it’s a safe bet that message is not legitimate. Additionally, if there is a hyperlink within the message, hovering over it will bring up the full URL.
- Pick up the phone if you have to: Unless you know the sender, any request for personal information should be ignored. If you receive an email from your bank asking for sensitive information and you are not sure if it’s legitimate or not, click out of the email and call the sender.
- Don’t get attached: Be wary of attachments in emails that you are not sure about. Well-known companies and brands rarely send out attachments, so it’s a safe bet you should ignore one should it come through.
While cybersecurity is a topic that should be at top of mind every month (and every day!), using the information and resources available during National Cybersecurity Awareness Month is a good idea to refresh your online behavior and make sure you’re keeping your sensitive information safe.