When it comes to email authentication standards, should you use DKIM, SPF, or both? We’re going to cover these terms, when you should use them, what they do—and how best to protect your email domains.
Is it DKIM vs. SPF—or BOTH?
Should the battle really be DKIM vs. SPF? While not mandatory, it’s highly recommended to use both SPF and DKIM to protect your email domains from spoofing attacks and fraud while also increasing your email deliverability.
At a time when millions of corporate employees remain working from home post-pandemic, email continues to be one of the most important communication tools for business. Unfortunately, it also happens to be one of the most profitable vectors for email crime networks. According to the 2023 FBI IC3 report, over $50 billion in losses across the globe has been attributed to BEC fraud over a decade span from 2013-2022!
And according to the "Journal of Cybersecurity" in 2021, the largest and most prominent of data breaches experienced by organizations resulted in lost business and significant reputational (e.g., intangible capital loss) of 5–9%! Even if you avoid regulatory fines or lawsuits, your own legitimate email marketing and communications programs can see deliverability rates tank—if your domains aren't blacklisted all together.
Per Intuit's Mailchimp, email blacklisting can "cut off your access to new leads generated through surveys, activity on your website, and the lists of qualified leads offered by marketing service providers. Perhaps even worse, [it] can deny you access to loyal, long-time customers who value and crave the content you offer. Should this happen, you could lose your most valued customers. Depending on the platform that blacklists you, it could cost you a significant percentage of your regular revenue."
How Does Domain Spoofing Work?
In order to spoof an email, all a fraudster has to do is set up or compromise an SMTP server. From there, they can manipulate the ‘From’, ‘Reply-To’, and ‘Return-Path’ email addresses to make their phishing emails appear to be legitimate messages from the individual or brand they're impersonating.
This identity deception is made possible by the fact that SMTP—the Simple Message Transfer protocol used by email systems to send, receive, or relay outgoing emails—lacks a mechanism for authenticating email addresses.
Early email authentication standards such as S/MIME failed to gain enough traction to make much of a dent against this threat. But beginning in the mid-2000's, a pair of emerging email security standards started to succeed where other approaches failed—SPF and DKIM.
So What Are DKIM and SPF?
So what is the SPF email standard (or Sender Policy Framework), and what is the DKIM standard (or DomainKeys Identified Email)? They both are important email security standards designed to help prevent hackers from spoofing your domains for use in email attacks targeting your customers, partners, and the general public. To understand why, let's take a look at these standards, why it's smarter to leverage both instead of just one—and how to do it right.
How Does DKIM Work?
DKIM uses asymmetric encryption to give email senders a way to digitally sign all the outgoing email from a given domain, and publish the public key(s) necessary to validate those digital signatures. This enables receiving email providers to confirm that no changes have been made to the email in transit. Learn more with our DKIM guide for setting it up. Once you do, use a tool to look up DKIM email records to make sure receiving email servers can locate your public key.
When an SMTP server receives an email with such a signature in the header, the server asks the sending domain’s DNS for the public key TXT record. Using the public key, the receiving server is able to verify whether the email was actually sent from that domain.
If the check fails, or if the signature doesn't exist, the receiving email service provider might mark the email as spam or block the sender's IP address altogether. This makes it harder for fraudsters to make emails look like they came from your domain address.
How Does SPF Work?
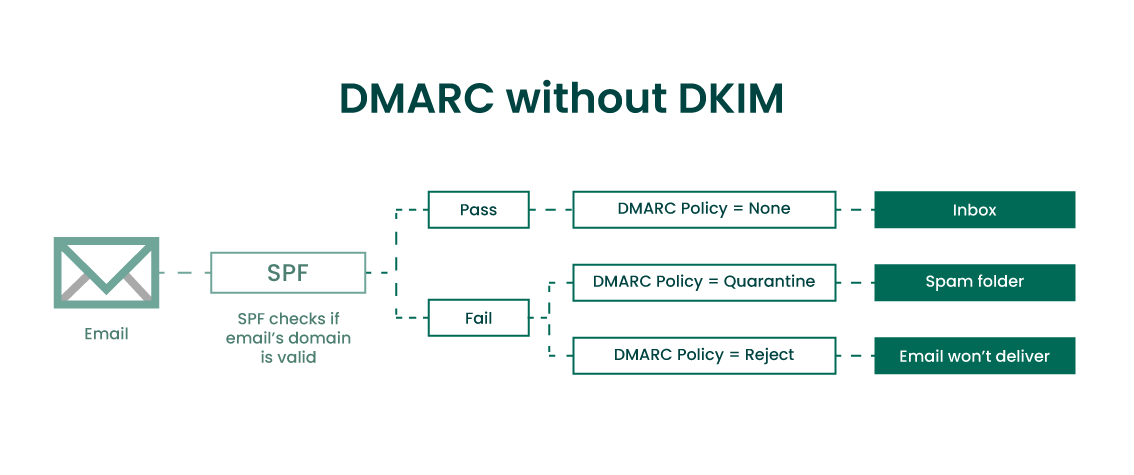
At its most essential, SPF allows email senders to specify which IP addresses are allowed to send email from a given domain. For example, a domain owner can stipulate that only IP 5.6.7.8.9 is allowed to send email from @YourCompanyURLHere.com by publishing that policy as a TXT record in the specified domain's DNS. You can see which servers are authorized to send emails for your domains by using a tool to look up SPF email records.
During an SPF check, receiving email servers query the DNS records associated with your sending domain to verify that the IP address used to send the email is listed in the SPF email record. If it isn't, the email will fail authentication—helping to weed out malicious emails attempting to exploit the associated domain.
Implement DKIM, SPF, or Both – Ah, That Is the Question
Ultimately, this isn't an either/or or one vs. the other proposition—it's a "better together" scenario. That's because SPF and DKIM address two integral, but discrete, issues central to email security. SPF helps confirm whether an email purporting to come from your company was in fact sent from one of your established IP addresses, and DKIM confirms that the email hasn't been faked or altered on its way to its intended recipient. So the truth is they are more like frenemies than enemies!
But it's also important to note that whether they're used on their own or together, DKIM and SPF do not provide a complete solution for email authentication. For that, we'll need to add an additional acronym to the conversation: DMARC.
How Does DMARC Work with Both of These Protocols?
First introduced in 2012, Domain-based Message Authentication, Reporting & Conformance (DMARC) is a standard email authentication protocol that adds a policy layer to SPF and DKIM.
With DMARC, companies can publish policies telling email providers when they should rely on DKIM and SPF for a given domain, and what to do when messages fail either of those tests. DMARC's most aggressive enforcement policy option is reject (p=reject), which means email messages that don't pass DMARC authentication will be rejected by the receiving email server and stopped from being delivered to the intended recipient. To learn more, read our DMARC setup guide.
It's relatively easy to generate a DMARC email record and assign it to a DNS. But for large organizations, implementing DMARC across a large number of domains can get very complicated, very fast. Using email ecosystem management solutions designed to help organizations make full use of SPF, DKIM, and DMARC authentication can dramatically simplify the process—causing phishing emails sent by fraudsters seeking to impersonate their businesses to drop to near zero in a matter of weeks.
What's more, organizations that do adopt these solutions and approaches have realized extraordinary results. A real-world Agari DMARC Protection customer, a Fortune 500 large insurance company, ratcheted up their DMARC policy to p=quarantine, resulting in all of their failed messages being rejected and filtering into the Spam folder instead of hitting their inbox. These included a deluge of emails coming from unknown IP addresses with low reputation scores from a myriad of irregular countries without host names. Thanks to Agari DMARC Protection's automated authentication solution setting them at the most stringent level, these messages were blocked outright!
Plus, using newer, DMARC-enabled standards like Brand Indicators for Message Identification (BIMI), organizations can display their brand logos next to the subject line of their emails within the recipient's email inbox—boosting brand presence while providing assurance that the email can be trusted.
Learn how securing your email and protecting your brand from impersonation can ensure email deliverability and increase brand loyalty.
