Since the beginning of February, we have seen more than a 3,000% increase in Coronavirus-themed phishing attacks targeting our customers. The spike in attacks is as logical as it is repugnant. With an estimated 75 million employees more reliant than ever on email during the largest "work-from-home experiment" in history, phishing scammers and other threat actors seem hellbent on exploiting heightened anxieties and upended organizational processes stemming from the outbreak.
Let's take a look at just three of the COVID-19 related credential phishing emails we've seen recently to better understand how phishing threat actors are exploiting the global pandemic.
Impersonating First Responders
Since the beginning of February, 17% of all COVID-19 Brand Display Name Imposter phishing attacks we have observed have impersonated either the World Health Organization (WHO) or the US Center for Disease Control and Prevention (CDC). The use of these organizations in phishing attacks is meant to add a sense of authority and credibility to a malicious email.
This first example of COVID-19 credential phishing leverages the name and logo of the WHO to pose as an email that supposedly links to a Docusign document containing basic information about how to stay healthy during the pandemic. Clicking on the “Review” button in the body of the email takes a victim to a Docusign login page where they are asked to “sign in” to view the document. Of course, once they log in, the document they are shown is nothing more than a decoy and their account has effectively been compromised.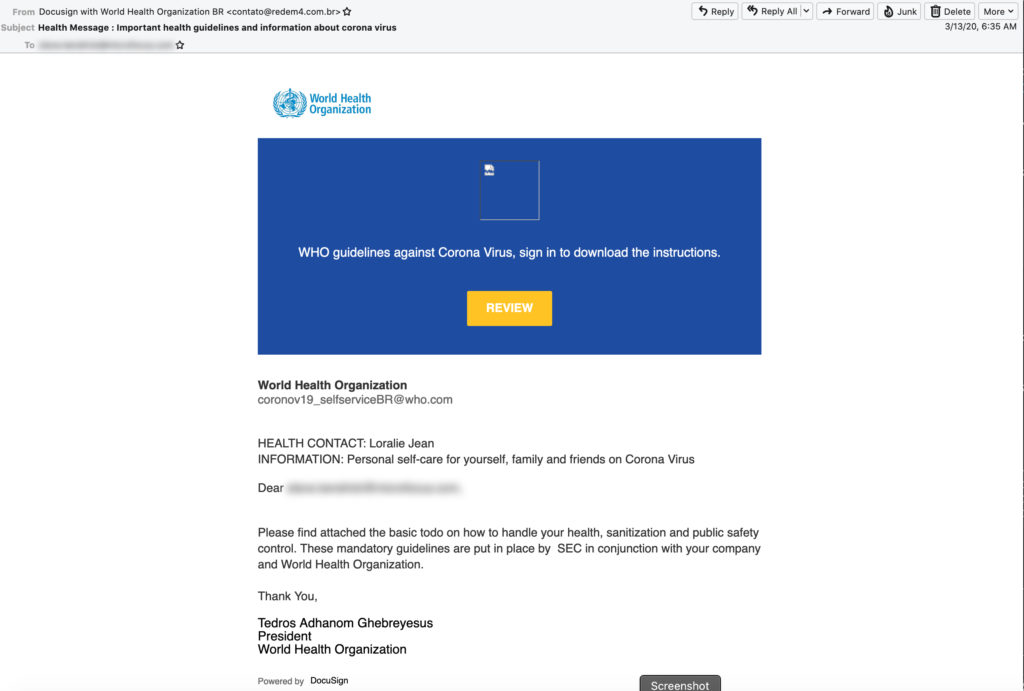
Credentials Harvesting Cuts Close to Home
This second phishing email from “Department of Health” claims to contain a link to a list of new COVID-19 cases in the target's own city. But look closely, and you'll see that instead of coming from a legitimate health organization, the email address is actually “zacks.com,” a financial investment firm whose domain is likely being spoofed.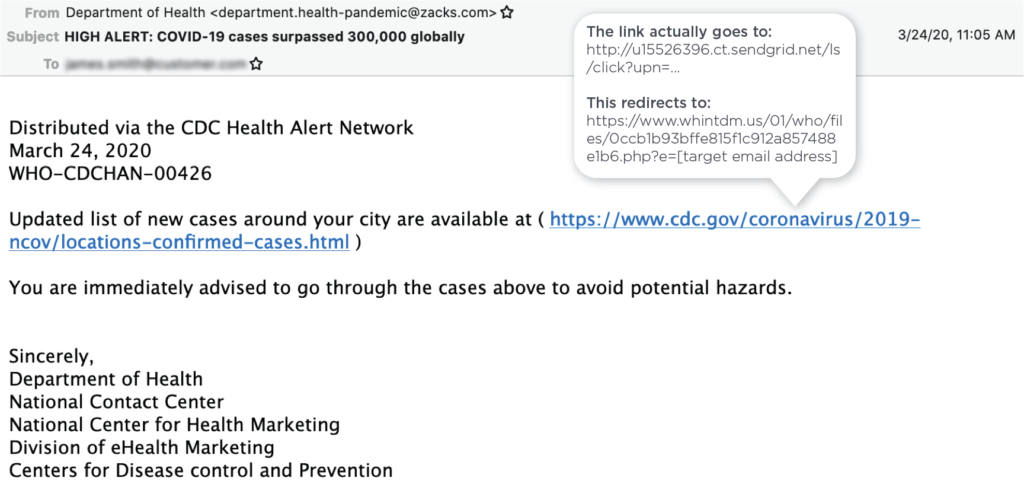
While the embedded link looks as if it leads to an official Centers for Disease Control (CDC) webpage, it's actually a SendGrid URL that redirects the recipient to a bogus Microsoft Outlook login page.
The inference here is that in order to view the information about new local COVID-19 cases, the target must first enter their email login credentials to authenticate their identity. The target's email address is even pre-populated, so all they need to enter is their password. Once they do, the victim's email account is compromised, while they're redirected to a legitimate CDC webpage containing a summary of worldwide COVID-19 cases. The victim? None the wiser.
According to the FBI, an unprecedented wave of scams is targeting three states in particular—California, New York, and Washington—which rank among the hardest hit by the outbreak so far.
Impersonating HR in an 'Official' Company Announcement
Similar to the recent trend of phishing emails posing as e-faxes or electronic voicemails, this next attack masks itself as an important document about COVID-19 from the Human Resources department at the target recipient's company.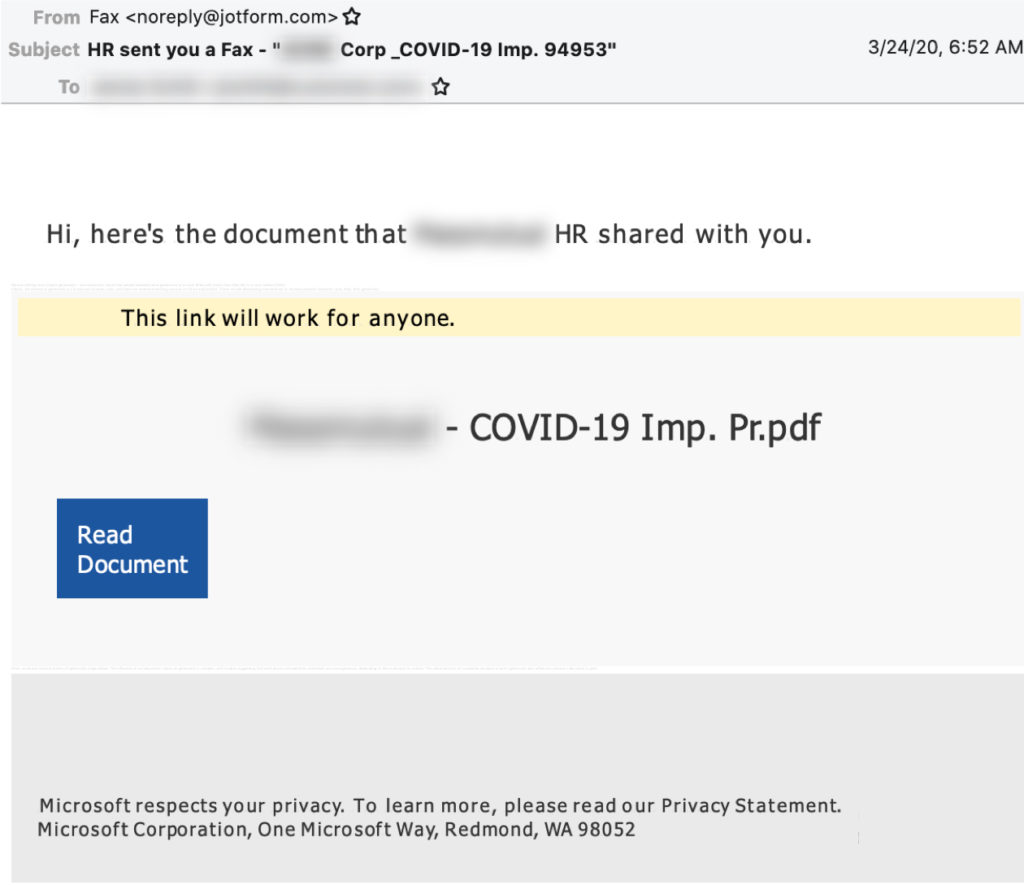
The “Read Document” link takes the target to a sham SharePoint page with a pop-up prompting them to either download the supposed Word document or view it online.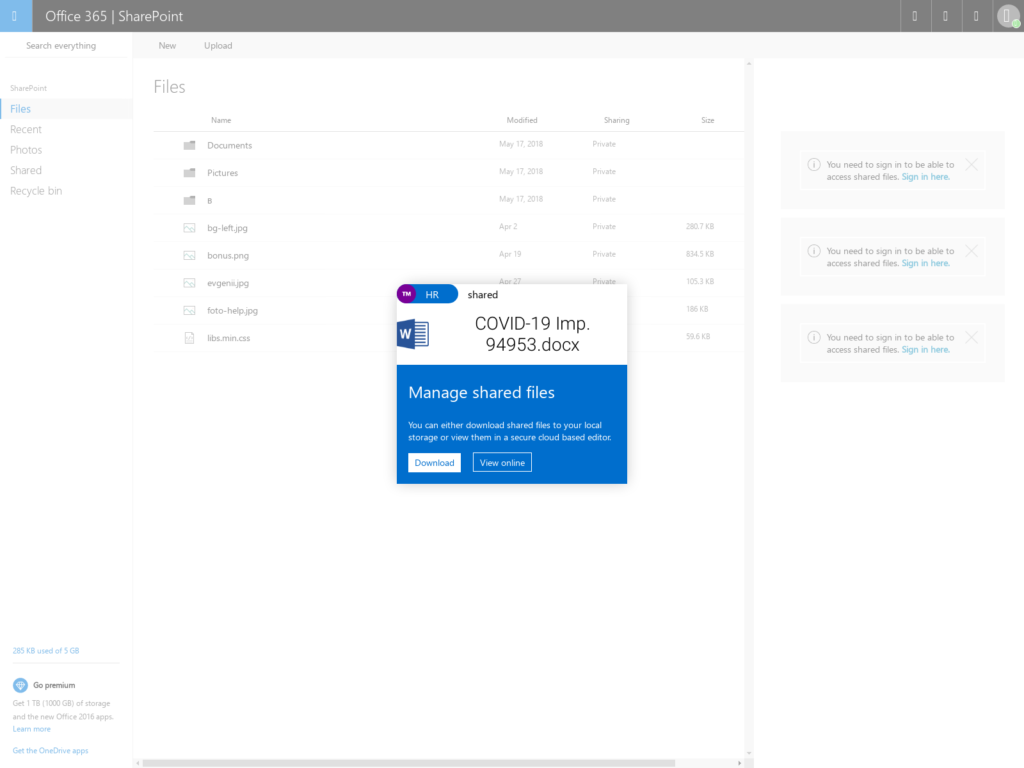
Clicking on either button takes the user to a mock Microsoft login page, prepopulated with their email address, and a message stating, “You are about to access sensitive information. Confirm your password to continue.” Once the victim enters the password, their account is compromised and they're shown a phony document with “important COVID-19 information.” Meanwhile, the fraudsters behind the attack have gained a foothold from which to move laterally through your organization in search of valuable IP, customer data, and more.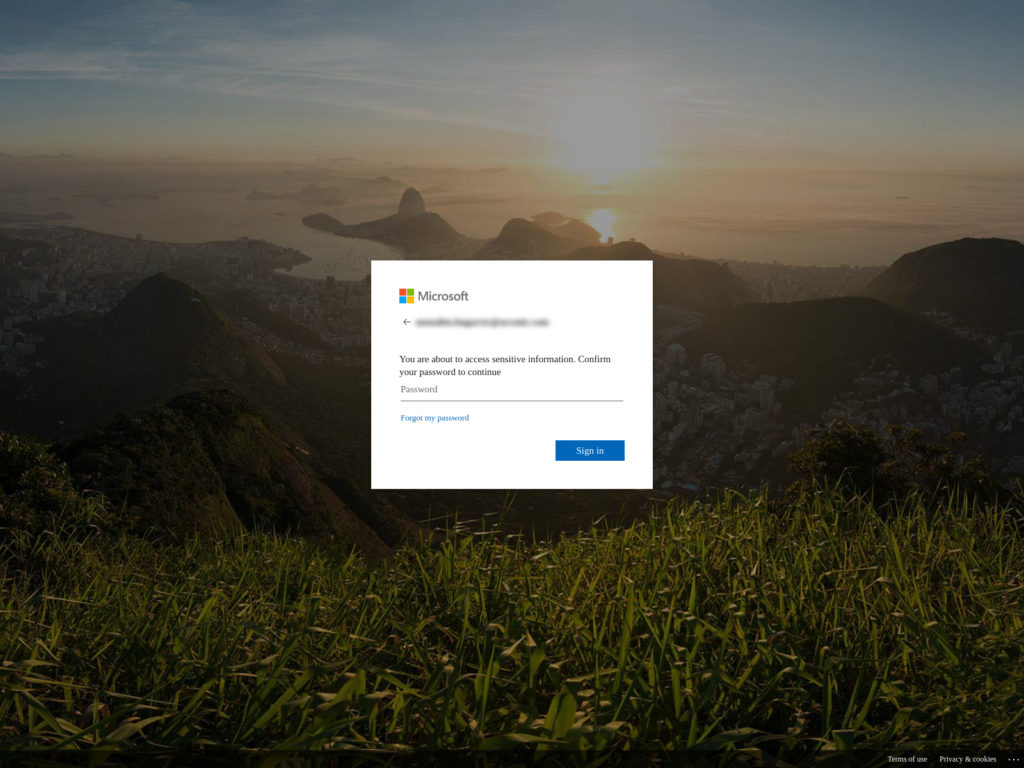
As goes the latest news about COVID-19, so goes the threat from phishing attacks that exploit it. Businesses seeking to protect themselves should consider phishing simulation training to help employees better spot new scams, as well as advanced phishing defenses that minimize the number of attacks that make it to employee inboxes while mitigating those that do. As the coronavirus outbreak reaches its apex in some major cities over the coming weeks before changing its trajectory, one thing seems certain: the volume and nature of phishing attacks will continue to evolve along with it.