Unique BEC Approach May Be a Sign of Things to Come in the Age of COVID-19
Amid a sharp rise in coronavirus-related phishing attacks worldwide, Fortra identified what may be the first documented use of the pandemic as a lure in an emerging breed of business email compromise (BEC) scams that can fleece businesses out of millions.
In January, we published a post about an email crime ring code named Ancient Tortoise, which has an especially devious approach to BEC.
By impersonating senior executives in email, this group acquires a company's accounts receivable aging reports and then targets that company's customers with requests for payment on invoices.
As we've continued tracking Ancient Tortoise, we've discovered that the group has seized upon the novel coronavirus, also known as COVID-19, as a hook in its email schemes.
During a recent active defense engagement, we provided Ancient Tortoise with a phony aging report containing a list of “customers” that traced back to a set of persona accounts. In short order, the group began reaching out to those "customers," requesting payment on past-due invoices.
In its emails, Ancient Tortoise used the coronavirus as pretext for new payment details—explaining that the global outbreak had forced a change in the bank being used to receive payments, which pointed to a mule account in Hong Kong.
With coronavirus-themed email attacks running rampant, this particular ploy could prove quite dangerous.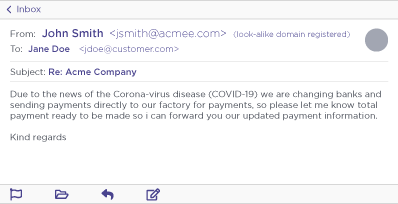
Example Ancient Tortoise Coronavirus-themed email. Names and persona domains have been changed.
Coronavirus: BEC Most Believable
The social engineering tactics employed in this scheme can be crushingly effective.
Emails sent to target companies include legitimate transaction details that presumably could only be known by the supplier being impersonated. And because the request for payment generally involves invoices that are overdue, there's built-in urgency. Citing coronavirus in these emails adds two additional factors to the ploy.
First, it puts a believable explanation to why payment details differ from those on record. Second, in a time when supply chains face tremendous upheaval, companies risk endangering themselves if they don’t reliably meet their financial commitments to suppliers—adding additional pressure for prompt payment.
It's a smart approach. According to the FBI, BEC attacks doubled last year, and have accounted for more than $26 billion in business losses since 2016. That's $700 million losses every month. And while a traditional BEC scam may net cybercriminals an average of $60,000, those that involve supply chain imposters average $125,000.
In Ancient Tortoise's case, a single financial aging report can provide information on numerous targets. Multiple companies could end up swindled. And the company that had its aging reports pilfered could face financial and reputational damage.
But coronavirus may drive the stakes up much higher.
When Crisis Spells Opportunity
Sure, email crime rings have always taken advantage of crises to prey on targets. But the coronavirus may be more than just the "lure de jour."
"Criminals are opportunists, and as seen in the past, any major news event becomes an opportunity for groups or individuals with malicious intentions," the US Secret Service warns in a recent statement distributed to state and local law enforcement agencies.
"In fact, the Coronavirus is a much more potent opportunity for enterprising criminals because it plays on one of the basest human conditions…fear." When flooded with information on a topic that makes people anxious, phishing attacks can blend in and capitalize on uncertainty.
So far, attacks have included phishing emails impersonating the Centers for Disease Control (CDC), the World Health Organization (WHO), and John Hopkins University, under the guise of delivering important information about the pandemic—often in the form of malware-infected attachments.
The Federal Trade Commission is also warning that fraudsters are posing as charitable organizations asking for donations and as e-commerce companies hawking medical masks, disinfectant, and bogus coronavirus cures.
Cyber-thieves aren't the only ones to look out for, either. According to SiliconRepublic, Russia, China, North Korea and other nation-states are taking advantage of the pandemic in phishing campaigns of their own.
Even so, this isn't your average cybercriminal news jacking opportunity. With coronavirus, the entire BEC attack surface is expanding exponentially.
What Email Crimes May Come
Think about it. One of the biggest impacts from the coronavirus is an even greater reliance on email communications and what Fortune calls the "world's largest work-from-home experiment."
With large numbers of corporate employees working remotely, look for higher volumes of email scams targeting individuals in HR, payroll, IT—and yes, accounts payable—at a time when many security, access, and accounting controls may not be functioning as well as possible.
In some fields, accessing business applications remotely may be unfamiliar to many employees, making them more susceptible to emails that fool them into entering login credentials on phishing sites disguised as Microsoft Office 365, Outlook, or critical management platforms. Just ask UK health system workers hit by a coronavirus credentials harvesting scam.
Malicious requests to HR or payroll asking for changes to direct deposit details are likely to rise. So might attacks targeting employees with fraud warnings about their 401K accounts due to girations in the financial markets.
For businesses, phishing simulation training will be more important than ever. So will identity-based defenses that block social engineering-based BEC scams, phishing attacks, and other advanced email threats.
Because if the sophistication seen in the BEC attacks from Ancient Tortoise are any indication of what to expect in the age of coronavirus, one thing is clear. Just as with the contagion itself, things could get a whole lot worse in the weeks ahead.