Back in July, we wrote about an emerging trend we have observed that involves attackers requesting aging reports from Business Email Compromise (BEC) targets. As we discussed in that post, aging reports are used by finance teams to track unpaid customer invoices. These reports are integral in the accounts receivable realm to maintain visibility into a supplier’s payment collection process. Aging reports also contain a wealth of information that can be used by cyber threat actors to leverage for malicious purposes.
In early November, we observed a BEC email impersonating the CFO of one of our customers that was sent to one of the company’s accounts receivable specialists requesting a copy of an updated aging report, as well as the contact information for each of their customer’s accounts payable contacts.
Building off our previous research, we conducted an active defense engagement with this group, which we call Ancient Tortoise, to learn more about what happens after an employee inadvertently sends a company aging report to a malicious BEC attacker.
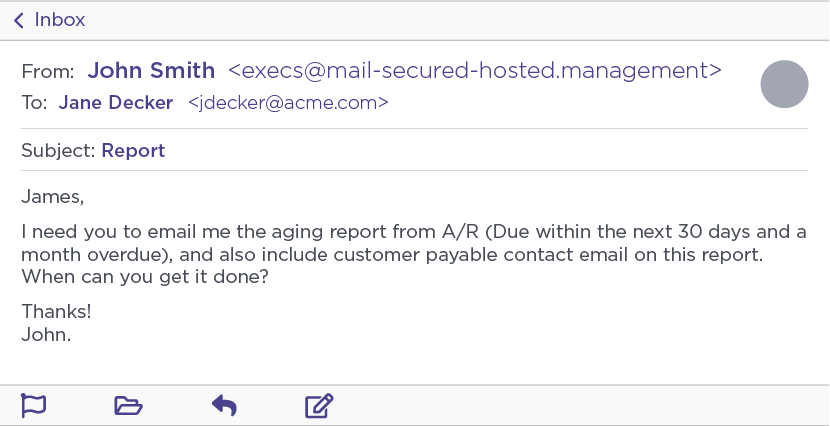
Example Ancient Tortoise email requesting a company aging report.
(NOTE: Names and persona domains have been changed.)
At this point, we initiated an engagement with the Ancient Tortoise attacker, pretending to be a finance employee at a different company who was responding to their “CFO.” Just like in the initial attack email, the scammer responded with a request for our fake company’s aging report. This time, we happily obliged and sent them a fake aging report containing the names of purported customers, the amounts of overdue payments, and the names and contact details for each of the “customers’” accounts payable points of contact.
Of course, none of these companies or contacts were real. They were all entities created and controlled by us.
After we sent out this fake aging report, we sat back and waited to see what would happen next. It didn’t take long for Ancient Tortoise to make their next move.
Synthetic Aging Report Snares Threat Actors
Two days after we sent our fake aging report to the Ancient Tortoise actor, each of our fake “customers” received an email requesting payment for the outstanding invoices referenced in the aging report. To make their email look legitimate, Ancient Tortoise registered a new domain about an hour and a half before sending the messages that closely mimicked our fake employee’s domain. Of course, the display name and username used by the scammer also matched our persona as well.
Because this email to a vendor’s customers appears to come from someone who is likely a known contact to the recipient and the content of the email contains legitimate information about the customer’s actual past due payments, these secondary attacks are much more realistic-looking than general types of BEC attacks.
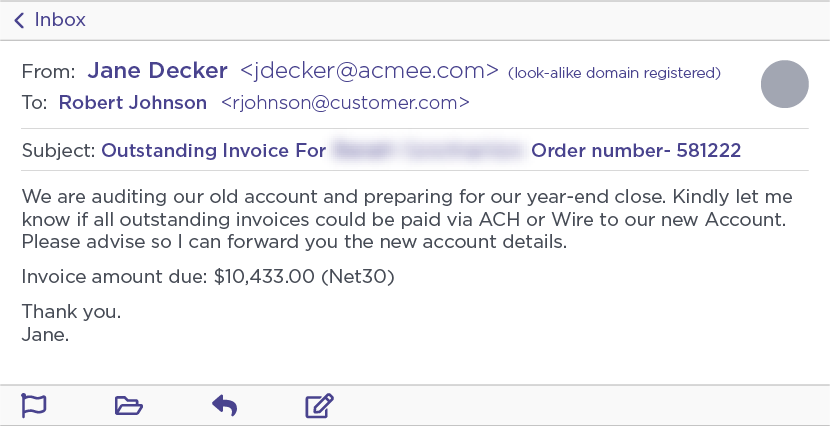
Ancient Tortoise email targeting aging report customers.
Once all of our fake persona “customers” had received emails from the scammer/”vendor,” we re-engaged Ancient Tortoise from many of these accounts to understand how they would respond to different requests.
Faux Invoices on the Fly
Noticing that the Ancient Tortoise actor mentioned that the vendor had a “new” bank account (read: money mule account), our first method of engagement was to simply inquire about where to send our supposed outstanding payment. These engagements continued in a similar manner to most wire transfer BEC attacks, with the attacker directly providing the details for the account where the payment should be sent.
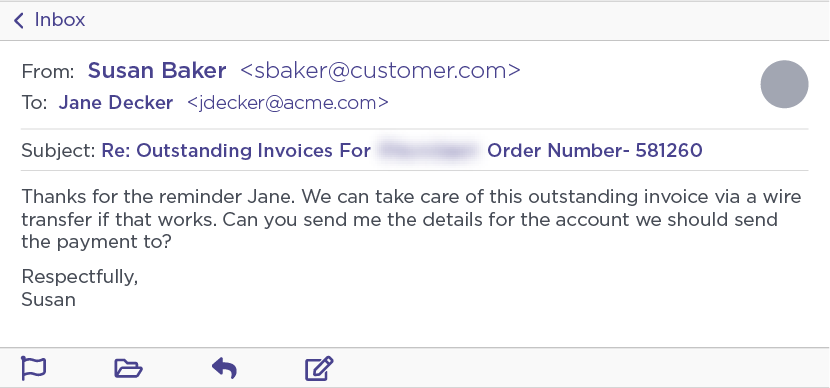
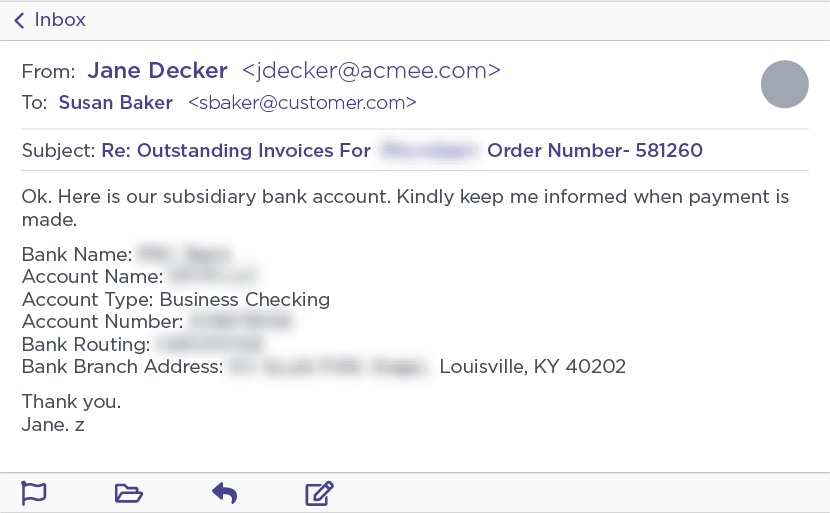
Continued Ancient Tortoise engagement requesting “payment” account.
In other engagements, we requested that the Ancient Tortoise scammer send us an invoice for the overdue payments to unmask the process cybercriminal groups like this go through to manufacture fake invoices that mimic a company’s legitimate document.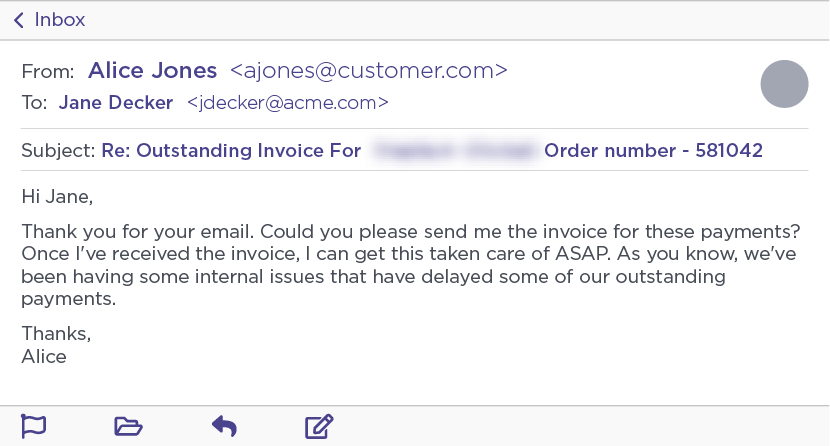
Eleven minutes after sending the above email, the Ancient Tortoise actor sent an email to our original fake persona target, requesting a copy of the invoices for our fake customer.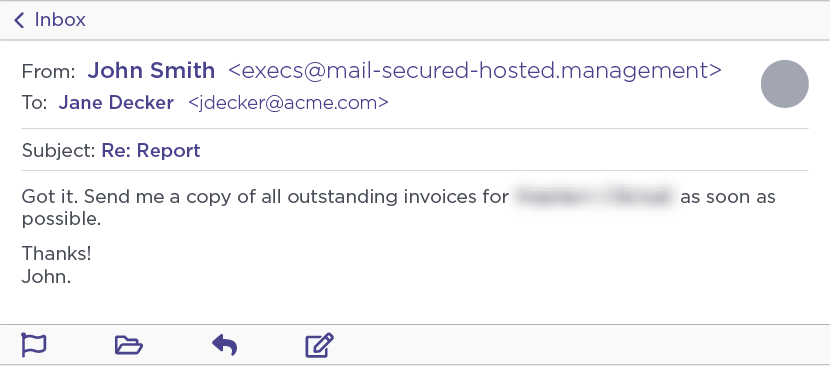
Expecting this request, we had created a fake PDF invoice to send to the scammer. Thirty minutes after sending the fake invoice to the Ancient Tortoise actor, he sent a copy of the invoice—with modified payment account details—to our fake customer.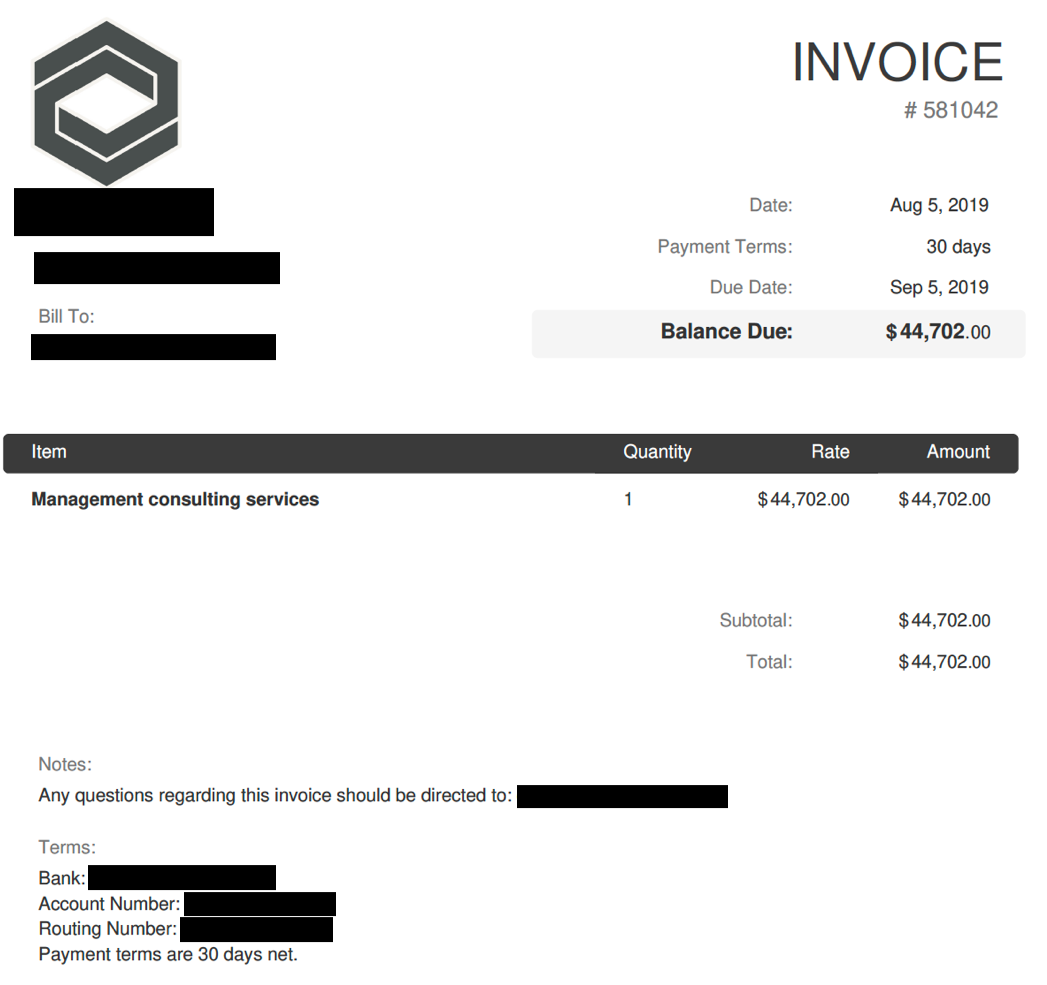
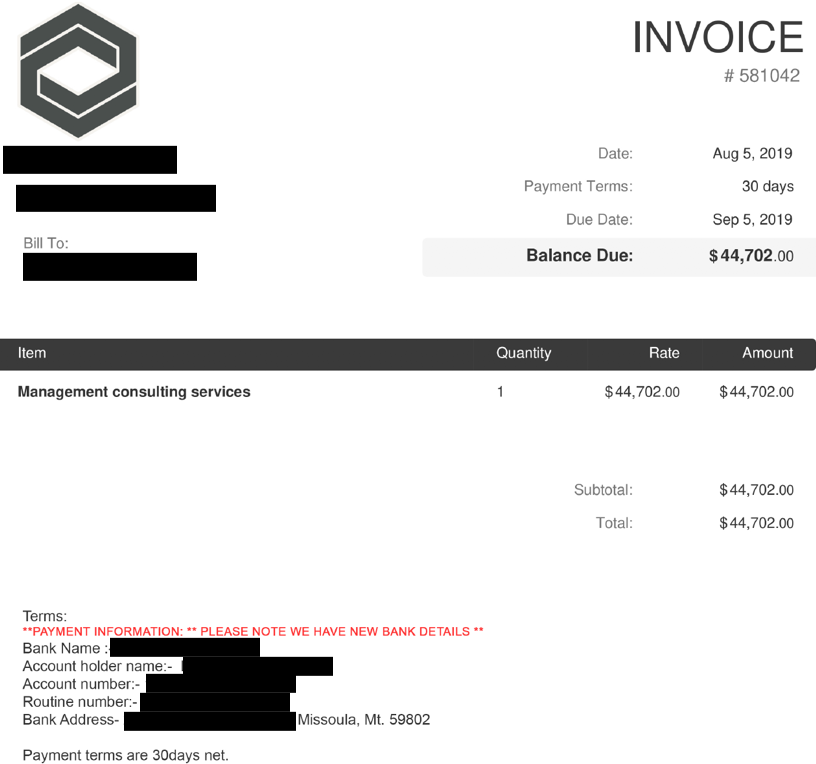
LEFT: Original fake invoice.
RIGHT: Invoice modified by Ancient Tortoise.
A forensic analysis of the forged invoice provided additional insight about Ancient Tortoise. The document’s metadata indicates the scammer uses a Macintosh computer and to manipulate the document, the actor used Adobe Photoshop 21.0 (also known as Photoshop 2020, which was released on November 4, 2019).
An analysis of the fake invoice also showed that the scammer’s computer was set to a +4 GMT timezone. This information lines up nicely with additional intelligence collected during our engagements that indicates the Ancient Tortoise actor was likely located in Dubai, United Arab Emirates.
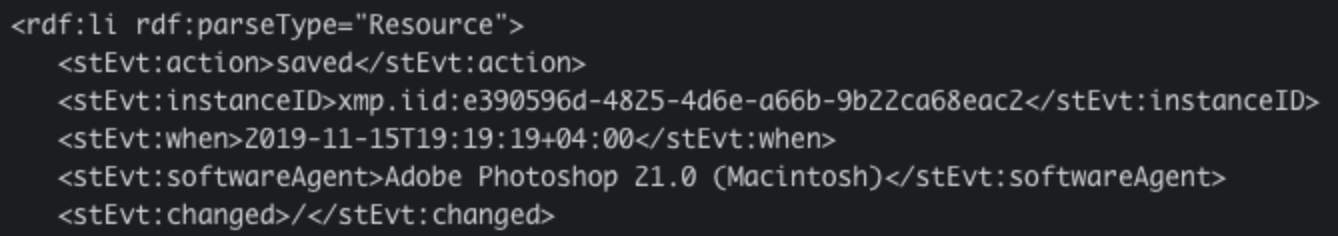
Sample metadata from a modified Ancient Tortoise invoice.
Protecting Yourself Against Aging Report Phishing Attacks
Aging report attacks are a twist on the emerging plague of Vendor Email Compromise (VEC) attacks that have been quickly become the biggest cyber threat impacted businesses all over the world. Like VEC attacks, aging report attacks compromise the business supply chain by targeting both ends of a financial transaction: the supplier and their customers.
While the fake invoice we sent to Ancient Tortoise only included a small number of fake customers, some real aging reports can contain information on hundreds or thousands of patron companies. For example, during our research into Silent Starling, a Nigeria-based cybercrime group that specializes in VEC attacks, we observed the group compromise aging reports for a company that works with thousands of small and medium-sized businesses across the United States. In one case, Silent Starling received a consolidated aging report that included details for more than 3,500 customers with past due payments totaling more than $6.5 million.
Because aging report BEC attacks impact both vendors and their customers, each should take precautions from becoming victims of these attacks.
For vendors and suppliers, where the initial malicious email usually impersonates a company executive, a multi-layered approach to email security is essential, which includes implementing strong anti-phishing email and email authentication protections that specialize in defending against advanced identity deception attacks and brand spoofing.
For companies that work with external suppliers, in addition to utilizing identity deception defenses—for aging reports, attackers impersonate vendors rather than executives—having a formal process for handling outgoing payments (especially if supplier’s normal payment account has changed) is one of the best ways to prevent these types of attacks.