Receipts and invoices—two accounting powerhouses that require little introduction. But step a little further into the world of finance and accounts, and you can quickly become a fish out of water, as the terminology to this numerical land seems to multiply exponentially.
That said, in some of our recent active defense engagements with BEC cybercriminals, we have observed a new way scammers are using specialized accounting terminology against finance teams to obtain sensitive financial data and identify future targets of BEC attacks.
An aging report, or schedule of accounts receivable as it is also referred to, lists unpaid customer invoices and unused credit memos. It’s an essential tool for both accounts and management to maintain an overview of their credit and collection processes, and breaks down outstanding debts into thirty-day increments, culminating with payments that are more than ninety days overdue. It’s these reports that bad actors have identified as premium intelligence material, containing all the information they need to intercept existing payment channels and target your customers.
Asking for the Aging Report
During some recent engagements, we directly observed BEC scammers trying to obtain a copy of an aging report by leveraging the identity of criminals' favorite persona: the organization’s CEO. Using free and temporary email accounts and employing display name deception, these scammers made a straightforward request for the document.
Unlike many BEC scams, the scammers didn’t want the target to make a payment to a vendor bank account or purchase gift cards for outstanding employees. Instead, they simply asked that the target email them a copy of the aging report from “A/R”, i.e., Accounts Receivable.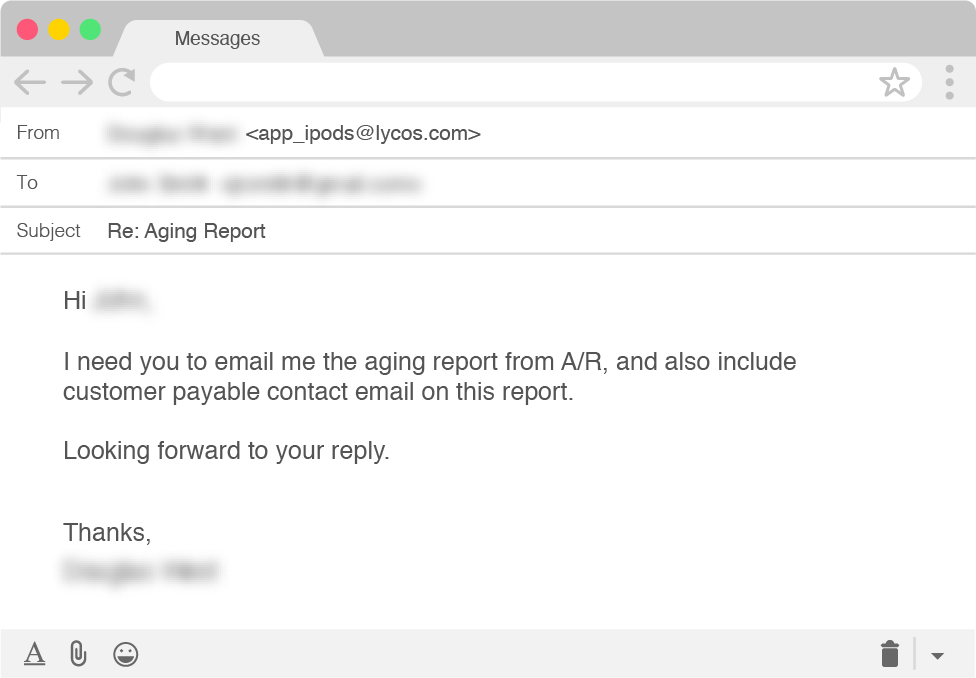
So if the scammers aren’t looking to get money from our fake personas, what exactly do they want?
Moving Beyond the Report and Into Customer Inboxes
After sending the scammers a copy of a fake aging report, their next request made their intentions a little more clear. In addition to providing a list of our customers and their outstanding debts, the scammers also wanted the email addresses for those customers on our aging report.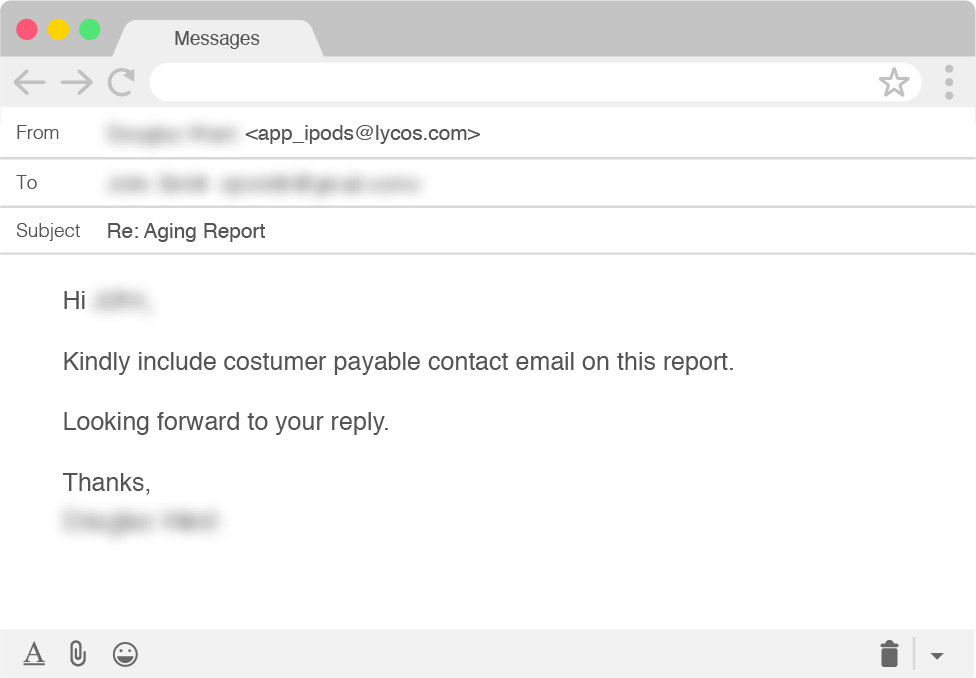
Armed with this intelligence—customer names, their outstanding balances, and contact information—the scammers’ next targets would be our fake company’s customers. With this information, they can create a credible-looking email account alias, assume the identity of an employee on our finance team, and request that they pay the outstanding balance referenced on the aging report.
The scammers will likely offer incentives for them to resolve their “debts” more quickly, such as reducing the amount they owe if they settle their outstanding balance immediately. The actor is then only left to inform the payee that there has been a recent change of banking details and provide them with updated account information for an account controlled by the criminals.
Your Customers Become the Victim
The full impact of being tricked into handing over sensitive information such as this cannot be understated. It pollutes established payment communication channels and requires proactively contacting all exposed customers to alert them to the possible threat. Beyond this initial danger, there are also latent risks, such as the inclusion of contact details for customer accounting personnel will increase the likelihood they will be targeted with future BEC attacks.
To protect your employees, organizations, and customers from becoming victims of this type of attack, we recommend taking a multilayered approach. Logically, none of this can play out if the initial CEO identity deception fails to reach the inbox of the intended target, so having strong email defenses against advanced email threats is an essential foundation layer to neutralize the danger.
In addition, internal processes for handling sensitive data, including aging reports, should be reviewed to ensure every contact point within the organization is aware of the threat. Doing so will lead to increased employee awareness so that those most-often targeted are more prepared to react with caution if they receive an email such as the ones above.
Learn more about how cybercriminals target businesses in a recent threat actor dossier on a cybercriminal organization named Scattered Canary.