The United States Government has substantially increased action against organizations and individuals responsible for breaches of the International Traffic in Arms Regulation (ITAR). This poses challenges for global defense corporations as data related to specific technologies may need to be transferred over the Internet or stored locally outside of the United States, in order to make business processes flow smoothly.
Business Problem
As an important USA export control law, the International Traffic in Arms Regulations (ITAR) affects the manufacture, sale, and distribution of technology in the defense sector. The goal of the legislation is to control access to specific types of technology and their associated data. Overall, the U.S. Government is attempting to prevent the disclosure or transfer of sensitive information to an unauthorized foreign national.
ITAR can pose challenges for global corporations, since data related to specific technologies may need to be transferred over the internet or stored locally outside of the United States in order to make business processes flow smoothly. The responsibility lies with the manufacturer or exporter to take the necessary precautions and steps to certify that they are, in fact, meeting ITAR compliance requirements.
Failure to comply can result in heavy fines, having to spend funds on remediation, compliance measures and may also require the party to submit to external audit. As a result, effective management of sensitive ITAR information becomes key in order to remain competitive and a trusted supplier.
Supporting ITAR Compliance with Clearswift
Data security will have different requirements for a commercial company, but there is a myriad of best practices that defense organizations must follow in order to appropriately secure ITAR data:
- Define and maintain an information security policy
- Build and maintain a secure network by installing and maintaining network defenses to protect sensitive data
- Protect sensitive data with encryption
- Regularly monitor networks
- Implement strong access control measures
- Track and monitor access to network resources and sensitive data
While this list is not exhaustive, it does highlight the need for an advanced solution that can: 1) detect ITAR information; and 2) ensure it is adequately protected as it flows between teams within the organization, and across the external boundary.
Clearswift provides a holistic cybersecurity platform that enables sensitive ITAR information to be identified and tracked as it flows through email. The platform, to include a set of optionally deployed components, seamlessly integrates with existing information security systems to enable improved ways of working, enhanced sensitive information security and visibility of information flow.
With email still being the primary business collaboration tool, defense organizations need to ensure that the ITAR content and information they send and receive is permitted to enter or leave the organization.
ITAR Protection with the Clearswift Secure Email Gateway Appliance
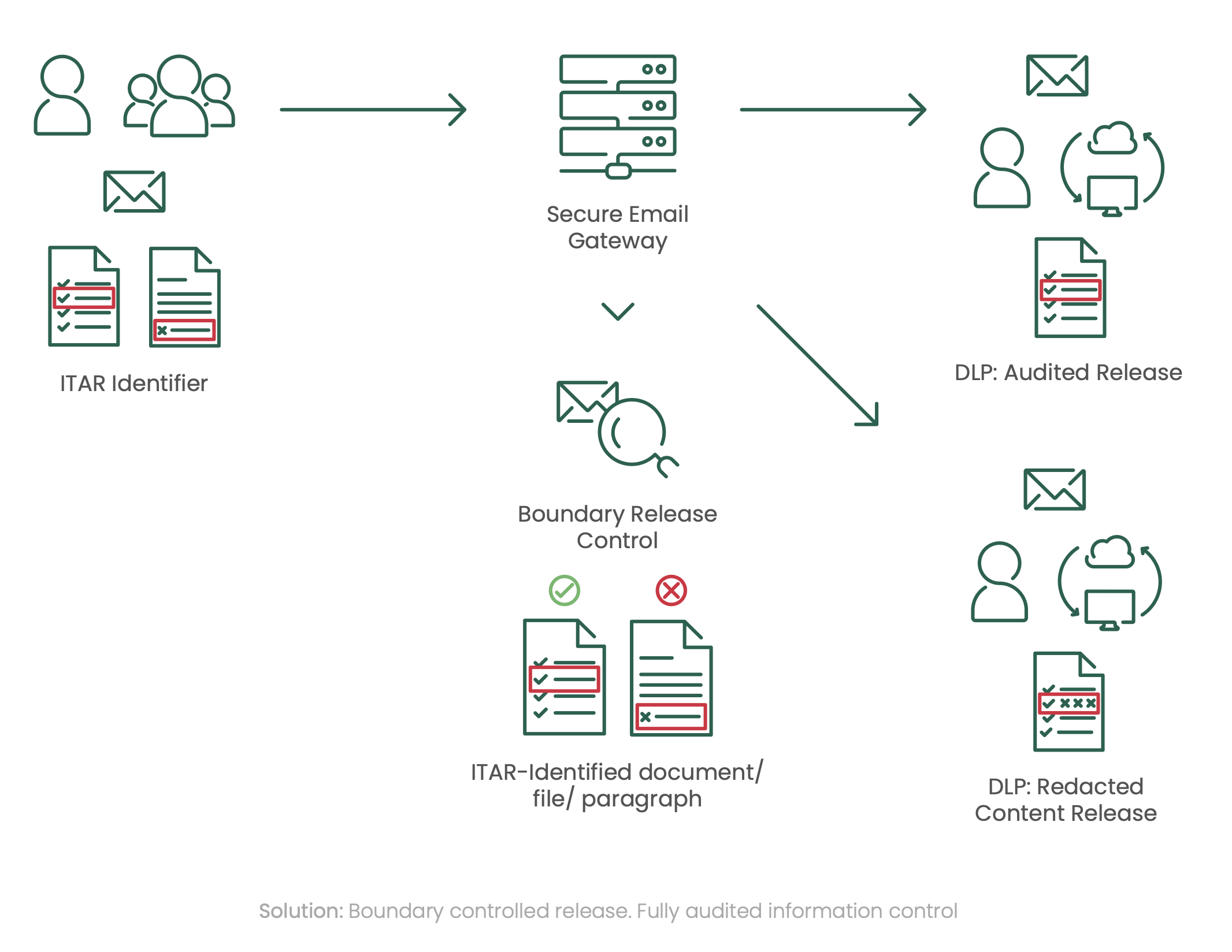
The on-premise Clearswift Secure Email Gateway (SEG) helps to secure against ITAR data breaches, protecting the organization and ensuring compliance with the current regulation. The Clearswift Secure Email Gateway (SEG) will:
- Scan emails for sensitive ITAR content – both inbound and outbound (as a compliance breach relates to both scenarios)
- Offer granular organizational policy to provide the necessary flexibility to permit multiple behaviours, depending on the senders and recipients of the message
- Provide logical segmentation of communication of sensitive information inside the organization, without the need for segregated email solutions (using the Clearswift Secure Exchange Gateway option)
- Adaptive Redaction functionality allows for content to be dynamically modified (redacted or sanitized) so the rest of the communication can be delivered, ensuring secure, but continuous, collaboration rather than having to ‘stop and block’ emails and force a remediation against a potential ITAR breach
- Apply encryption through policies where required
Clearswift's On-Premise Solution for Improving Control of Regulated ITAR Information
Features
Designed to meet small, medium and enterprise scale deployments, the Clearswift SEG appliance provides:
- Business-level information asset protection: focused on the asset value, risk profile, and the associated impact of the data associated with it;
- Secure handling: ITAR information shared through email systems and granular control based on content and context required to meet policy requirements;
- Multiple deployment options: on-premise or in the cloud;
- Classification tags: recognition and/or enforcement before information can be shared;
- Multiple encryption options: support for different communication policies, including TLS, PGP, S/MIME, and portal-based encryption;
- Optical Character Recognition & image-based text redaction: enables advanced features for dealing with scanned documents and image files;
- Sophisticated anti-steganography features: prevent infiltration of malicious code, or exfiltration of sensitive information in images;
- Coherent and consistent: ensures appropriate sharing of information within and across teams both internally and externally to the organisations that are holding or creating the data in support of the need for collaboration across multiple organisational and security domains;
- Full compatibility with Microsoft 365
- Data flow visibility: necessary controls and visibility of inbound/outbound data flow to support both audit and compliance under the specific collaboration policy requirements for ITAR;
- Support for operational requirements: for cybersecurity monitoring and incident response and multiple implementations of encryption that are common to international defense communities
Benefits
Designed to scale for organizations of all sizes, the Clearswift SEG appliance offers:
- Low friction: seamless deployment using an established, proven and assured security technology platform to minimize cost and maximize time to value;
- Deep content validation: proven capability to meet the specific demands of detecting ITAR-related content, especially in the ability to implement controls requiring deep content inspection checks, validation of information sensitivity and the adaptive requirements for content modification for an effective ITAR policy;
- User experience: innovation-led improvement to end user experience for secure sharing of information that reduces risk and the associated impact of an ITAR compliance breach;
- Reduced operational cost: specific features to deal with policy violations to minimize operational costs;
- Support: underpinned by a defense-aware organizational culture that is creative, passionate and built around a customer-focused ‘one-team’ approach, aligned with the essence of the Team Defense community, to ensure the low-risk delivery of enhanced protection