Business Email Compromise (BEC) is “one of the most financially damaging online crimes” according to the FBI1. It is a cunning form of email impersonation that when combined with human error, can be incredibly damaging and disruptive.
Understanding Email Impersonation
Modern email impersonation attacks exploit the identity of trusted colleagues and brands. There are a variety of ways identity-based email attacks work and each varies in the tactics and techniques used. Understanding these differences is critical in defending against these attacks effectively without disrupting legitimate email communications. To decipher BEC from other email impersonations, here are two additional ways cybercriminals attack.
Customer Phishing: Cybercriminals use brand impersonation techniques, such as domain spoofing and malicious content including phishing URLs, to evade security controls and trick their victims. Also, keeping content generic while launching scattershot attacks allows cybercriminals to reach as many recipients as possible.
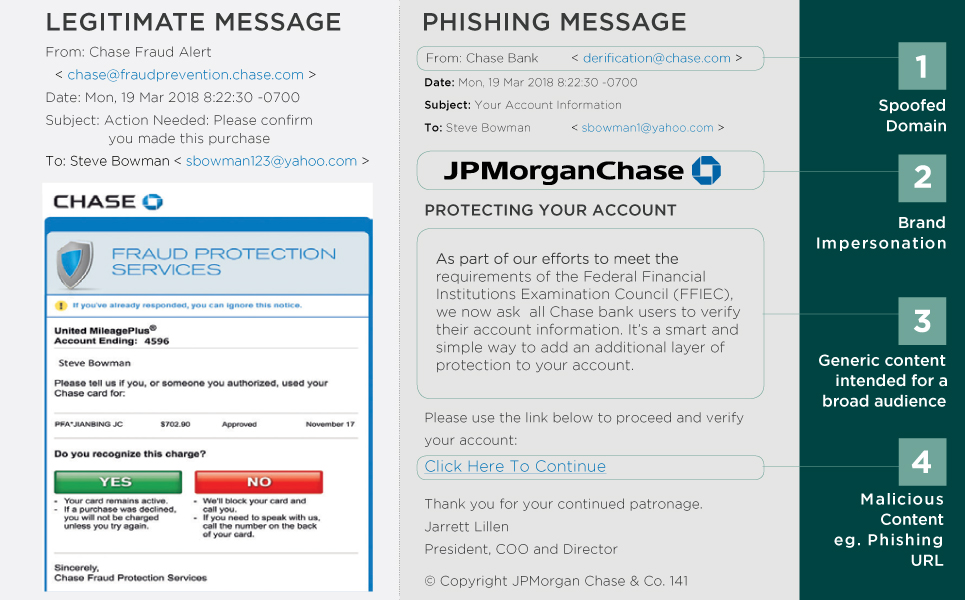
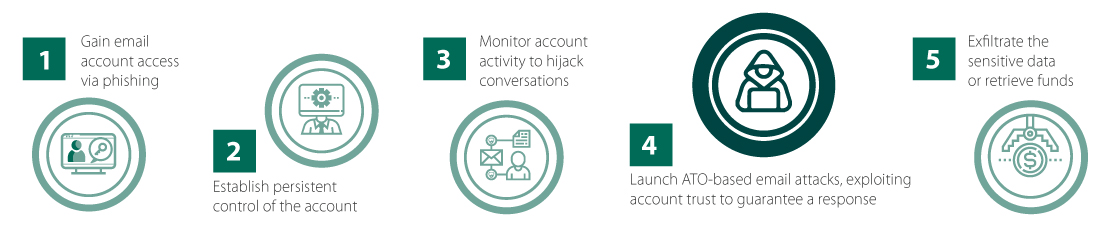
Account Takeover (ATO)-Based Email Attacks: Cybercriminals use a multi-step process that initially compromises a previously established, credible email account to launch subsequent targeted attacks such as BEC, spear phishing, or ransomware. ATO-based email attacks exploit the existing trust between the compromised account and its known contacts, which increases the cybercriminal’s success rate.
Why BEC Is a Formidable Threat
BEC uses social engineering to masquerade as executives, colleagues, and third-party vendors – tricking victims into believing they’re interacting with a trusted sender. Unlike email threats that incorporate malicious attachments or links, BEC relies purely on sender impersonation and social engineering to deceive recipients. With no malicious code or links, BEC can more easily bypass traditional email security solutions. A successful BEC attack can lead to the illegitimate transfer of funds, data breaches, or other harmful actions against victims and their organizations.
Stages of the Attack
Research
Preparation
Execution and Deception
Action
Just How Effective Is BEC?
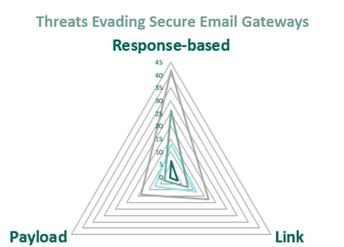
From afar, BEC attacks may look obvious and easy to avoid, but these attacks can be cultivated and methodical. In late 2022, Fortra™ reported that 97% of email threats involve email impersonation. So, it’s no surprise that BEC was the third-highest response-based threat in volume. The report also found that 21% of reported emails were either malicious or considered do not engage. This is the highest percentage of malicious and do not engage emails recorded in nine quarters.2
As long as cybercriminals continue to find success with fraudulent emails such as BEC, security teams should anticipate these threats will persist. In fact, Cybersource reported in their 2022 Global Fraud and Payments Report3 that eCommerce revenue lost to payment fraud increased in every major global region from 2021 to 2022. In the same report, phishing remained the most utilized vessel for fraud attacks globally.
Why Is BEC So Difficult to Combat?
Email impersonation attacks, such as BEC, are particularly successful in bypassing security controls because:
- They lack threat indicators such as payloads, blacklisted URLs, etc., that would normally be flagged by traditional security controls.
- Targeted social engineering content can be convincing to users and renders signature-based detection ineffective.
- Cybercriminals abuse legitimate mail services to avoid blocklists and ensure deliverability.
- Spoofed or lookalike domains aid deliverability and make these attacks more difficult to detect.
What Does This Mean for Your Organization?
Cybersecurity teams cannot depend on traditional signature-based email security controls to detect BEC. While there are no perfect remedies, many organizations have implemented additional layers of email security to minimize the risk posed by BEC. These solutions take advantage of machine learning innovations, stronger authentication mechanisms, threat intelligence, and automated threat response to prevent, detect, and respond to BEC and other advanced email threats. In our next article, we take a closer look at these solutions and how they better protect organizations from BEC attacks.