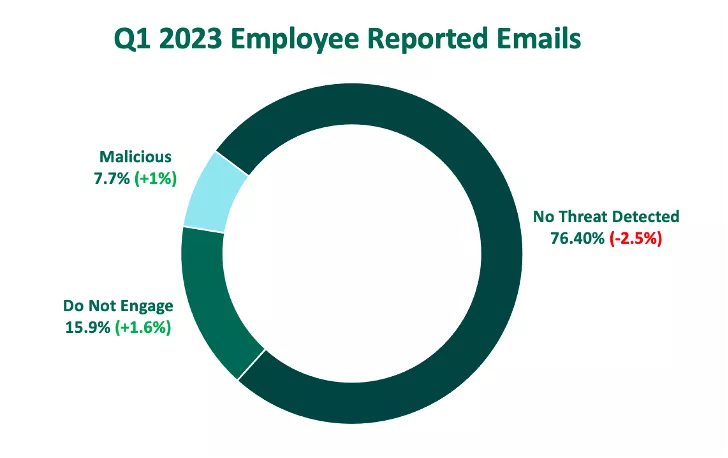
In Q1, the volume of emails classified as malicious or do not engage reached nearly a quarter of all reported emails. This is the highest combined volume of these categories since Fortra’s PhishLabs has documented this data point. Of those classified as malicious, threats considered email impersonation or, those lacking known signatures, made up a significant 98.7%.
Every quarter, Fortra analyzes hundreds of thousands of phishing and social media attacks targeting enterprises, brands, and employees. In this post we discuss the types of malicious emails making it into employee inboxes most, using intelligence collected through Fortra's Suspicious Email Analysis solution.
Malicious Email Breakdown
Both reported emails classified as Malicious and Do Not Engage increased in Q1 to make up nearly a quarter of all messages. This is the greatest combined volume of the two categories since reporting on this dataset.
Separately, Malicious emails increased 1%, representing 7.7% of share of volume. This is the greatest percentage of Malicious emails since Q3 2021.
Emails considered Do Not Engage are defined as suspicious messages that require interaction with the sender to verify malicious intent, and therefore should not be engaged with by users. In Q1, emails classified as Do Not Engage grew to the largest documented volume since Fortra first reported on the data in 2020.
Emails classified as No Threat Detected decreased for the fourth quarter in a row, representing 76.4% of total volume.
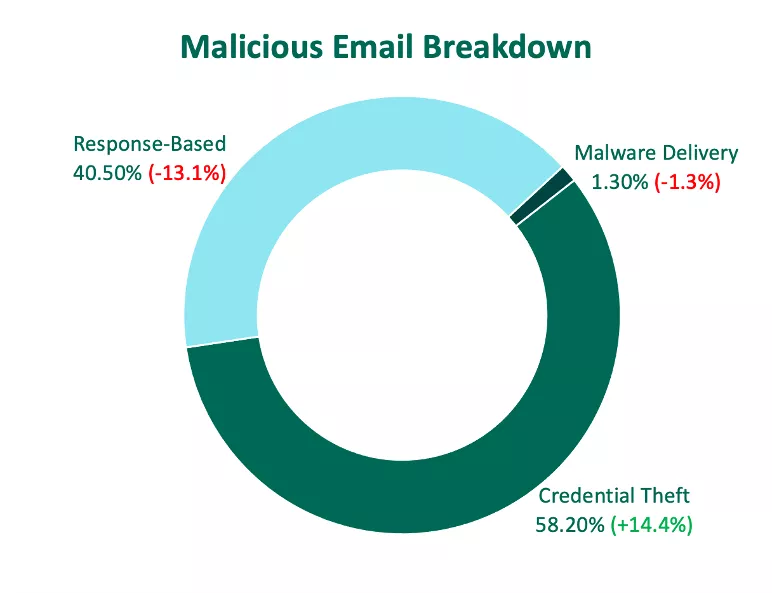
Credential Theft Attacks
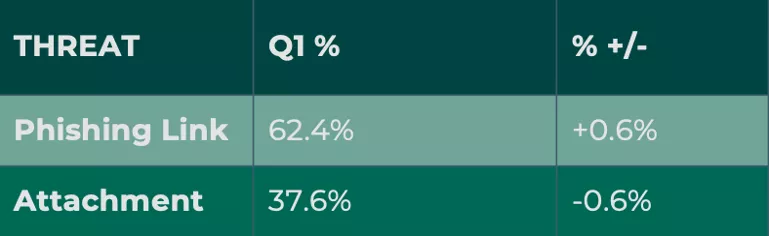
Falling under the umbrella of email impersonation, Credential Theft attacks jumped 14.4% of share from Q4, representing more than 58% of all malicious messages. Fortra categorizes Credential Theft into two groups, phishing links within emails that point victims to malicious websites, and emails containing attachments that redirect to malicious websites, otherwise known as Docuphish. Phishing links contributed to the majority of Credential Theft volume, with 62.4% of reports containing a link that led to a malicious website.
The majority of phishing link volume was driven by Microsoft O365 attacks, with 41.4% of all reported phishing links associated with this attack type. Microsoft O365 phish jumped 10% in share of volume over Q3, and nearly doubled in count.
Docuphish reports declined in Q4, contributing to 37.6% of volume.
Response-Based Attacks
Email impersonation attacks that are considered Response-Based experienced a dip in share of activity in Q1, totaling 40.5% of reported malicious emails.
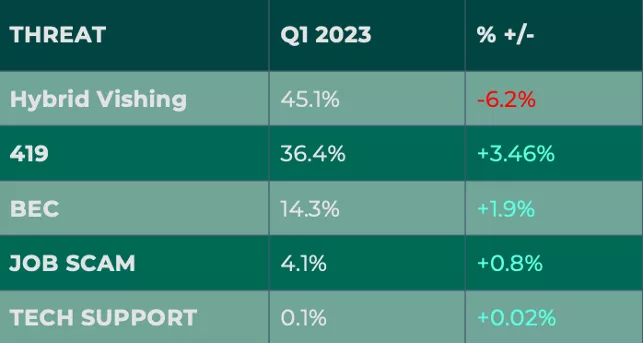
Hybrid vishing led the Response-Based group for the second quarter in a row, once again outnumbering historical leader 419/Advance Fee Fraud. This is despite a decline of 6.2% of hybrid vishing reports. Hybrid vishing emails have grown significantly since 2021, with criminals using this tactic more than 45% of the time in Q1. Hybrid vishing attacks are defined as email messages that contain phone numbers within the body of the message, with the intent to communicate with victims through both mediums.
In Q1, 419 attacks were reported more, growing 3.46% in share of volume. While 419 dropped to the second spot for the second quarter in a row, this threat type still contributed to more than 36% of total volume. Business Email Compromise (BEC) attacks increased in both count and share in Q1, representing just under 15% of attacks.
Both Job Scams and Tech Support experienced nominal increases in share in Q1. Job Scams grew to represent 4.1% of threat volume and Tech Support made up 0.1% of reports.
Malware Attacks
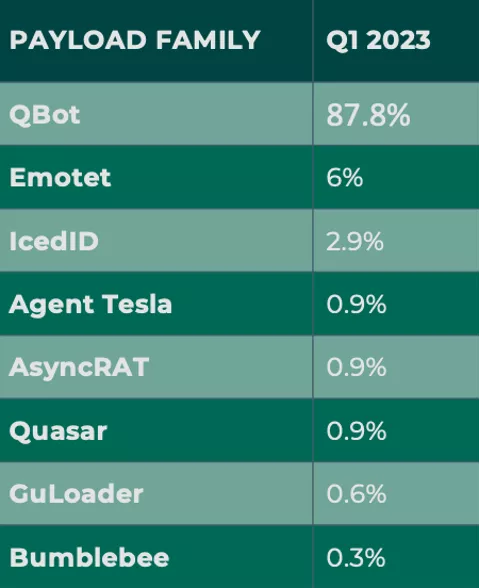
QBot was the payload of choice for criminals in Q1, representing 87.8% of reported volume. QBot is a malware-as-a-service (MaaS) known for its rapid infection chain. Emotet was the second most reported payload, with 6% of total volume. Emotet was absent for the first two months of the year, with the earliest attacks reported in March.
Former banking trojan IcedD came in third, contributing to just under 3% of payload volume. IcedID is increasingly desirable to cybercriminals after undergoing recent enhancements to its functionality that enable it to facilitate different types of attacks.
Agent Tesla, AsyncRAT, and Quasar all represented 0.9% tied in reported attacks, contributing to nearly one percent of total volume, apiece.
The increase in malicious email reports in Q1 indicates a gap in security controls’ ability to successfully identify attacks. Email impersonation threats specifically pose a glaring problem to organizations, as the lack of defined malicious indicators compromise traditional means of flagging and quarantining known threats. As cybercriminals increasingly model their attacks as text-based, security teams should implement advanced machine learning detection measures that will aid in the identification of socially engineered threats before they reach end users.
Learn how Fortra helps organizations combat malicious emails with our Suspicious Email Analysis solution.
