Security incidents hit 81% of organizations over the past twelve months, and internal threats pose a serious challenge for security teams, according to a new report from Osterman Research. The latest research says that the most common incidents are advanced threats—including spear phishing, social engineering, and account takeover-based attacks.
The report also says that too many organizations “do not have the necessary tools in place” to prevent these internal threats or remediate them quickly. And it highlights the areas where organizations can improve their defenses: better email security technology and better awareness training for employees and executives.
Why Do So Many Advanced Email Attacks Succeed?
Every major email application—including Microsoft Office 365 and Google Workspace—includes built-in security features. So with the vast majority of organizations using these cloud-based platforms, why do many attacks get through? Unfortunately, the fact is that while platform security tools are good at detecting spam and other basic threats, they are simply not as sophisticated as third-party solutions that specialize in catching the latest types of advanced attacks.
Organizations that rely solely on those built-in tools for email security are vulnerable to advanced attacks like business email compromise, which has cost businesses in the United States more than $13.5 billion in the last five years. That said, combining third-party tools and app-native security gives organizations more comprehensive protection and allows for greater control over the environment.
Email attacks can also succeed when people don’t know what to watch out for when a malicious email does make it through security controls. Dark Reading recently reported that 55% of organizations do not mandate any sort of security awareness training. And among those that do, less than 10% require training during onboarding and just 6% offer monthly training sessions to keep employees aware of new and emerging threats. This said, humans will always be the most vulnerable link in the security chain—but there’s no reason to leave them defenseless against spear-phishing and account takeover-based threats.
Wanted: Better and More Frequent Training
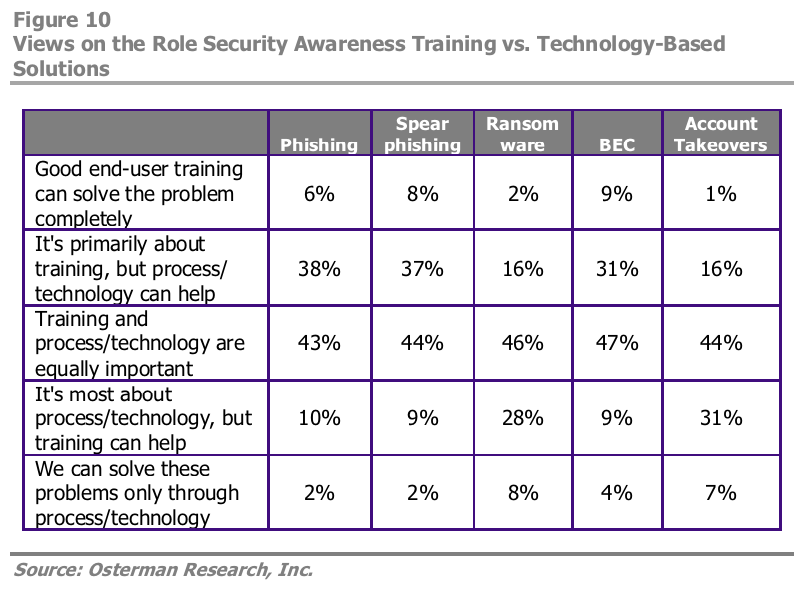
Despite the low numbers for training, more than 40% of security decision-makers surveyed by Osterman said that phishing and BEC prevention are mostly or completely about good awareness training. And Osterman found that training executives and employees can deliver a “substantial” ROI—especially at larger organizations.
What does a good security awareness training program look like? It goes far beyond quarterly mandatory meetings and email reminders to create a “culture of security.” A GovTech interview with Lear Corporation CISO Earl Duby describes how the automotive equipment supplier internally markets security best practices as “digital self-defense” through onsite events, gamified training modules, podcasts, and internal social media campaigns. The results included more reported phishing attempts, fewer clicks during phishing tests, and more employee engagement with security awareness resources.
Wanted: Better Tools with Artificial Intelligence Capabilities
While security awareness training can definitely help employees spot phishing emails and BEC scams, it is not the final solution for all types of attacks. Awareness training presents its own set of problems, including an increase in the number of false positives, but it cannot protect against the most dangerous type of threat—account takeover-based attacks. In fact, only 1% of the decision-makers Osterman surveyed said that end-user training can completely solve the problem, and 38% agreed that technology is needed to curb the threat. Since these threats originate from compromised accounts, they are incredibly difficult to detect, especially if the cybercriminal has access to entire conversations.
Overall, Osterman found that security leaders want cloud-based solutions, and almost 60% want to deploy “much more” artificial intelligence and machine learning technology against advanced threats. Recognizing that AI and ML can improve ATO protection is important. However, not all security leaders realize the scope of the ATO threat. A mere 7% of respondents in a Symantec survey rated ATO as a key risk, but account takeovers contribute to 42% of all security risks in actuality.
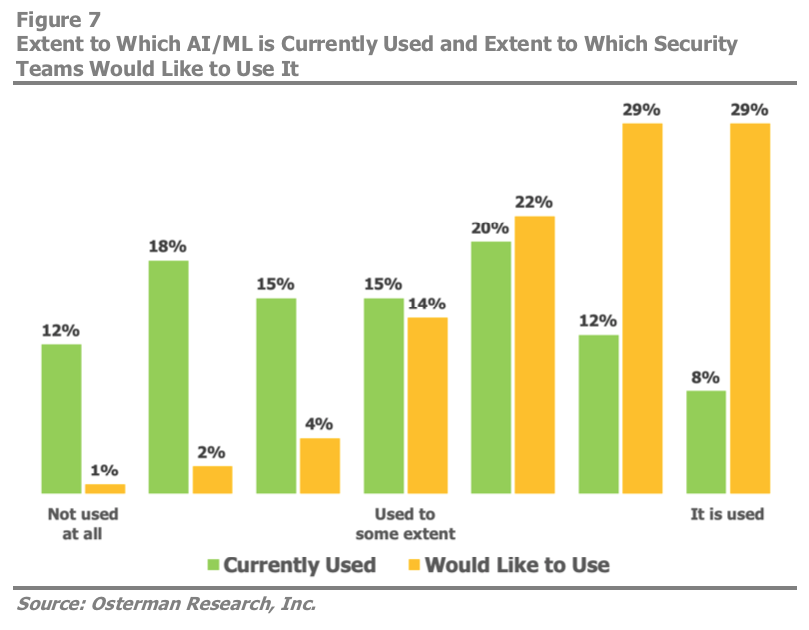
The threat is growing, too. Over the course of 2019, account takeover-based email attacks have ramped up by 35% to become the fastest-growing type of impersonation-based attack. To criminals, compromised accounts are ideal attack vectors, because their trusted identities get them past authentication and gateway security measures to their targets’ inboxes. The good news is that AI and machine learning offer ATO detection capabilities that legacy email security tools simply cannot.
Using AI to Detect and Halt ATO-Based Attacks
Legacy security systems are unprepared to stop attacks originating from compromised accounts since, by all appearances, they are coming from a trusted user. In contrast, Cloud Email Protection uses advanced machine learning to protect employee inboxes from these account takeover-based attacks, and other advanced threats.
The basis for Cloud Email Protection is the Agari Identity Graph, which analyzes over two trillion emails each year to map sender identities, analyze and evaluate perceived senders’ behavior, model trusted sender behavior, and score new messages according to those continuously evolving models. With the scores, Agari then detects malicious messages and provides indicators that help confirm when an employee’s email account is compromised—before the threat becomes a breach.
Email threats are constantly evolving. No single technology and no amount of end-user training can stop every single attack. But by improving security awareness training and adopting AI-based email security solutions, organizations can improve their odds against today’s most dangerous type of email threat.