A newly-enhanced Agari App for Splunk integrates email threat data from both Cloud Email Protection and Agari DMARC Protection directly into Splunk SIEM, with support for Splunk Enterprise and Splunk Cloud. This comes at a pivotal time.
We’re over a year into the pandemic, with an estimated 57% of corporate employees still working remotely and the prospect of transitioning to new, hybrid office schedules on the horizon. As organizations look to support employees both in-office and remotely, the formidable challenge of protecting organizations from sophisticated cyberattacks will only grow more complex.
Phishing continues to be the primary attack vector into organizations. These savvy, socially-engineered email threats carry the risk of direct financial loss, but perhaps more importantly, they can also give threat actors the foothold they need to steal corporate data and IP, or pull off massive supply chain attacks.
On one end of the equation is domain spoofing, which enables fraudsters to impersonate an organization or its executives in phishing attacks targeting their customers, partners, and the general public. On the other end are malicious inbound emails designed to trick corporate employees into making costly wire transfers or revealing login credentials.
To address these and the full spectrum of other cyberthreats facing their organizations, a growing number of security operations centers (SOCs) are deploying Splunk's security information and event management (SIEM) solutions to support early attack detection, investigation, and response.
With our newly-enhanced app, Agari is expanding on our partnership with Gartner's Magic Quadrant leader for security information and event management, and we couldn’t be more thrilled. The Agari App for Splunk now integrates threat data on inbound phishing attacks, in addition to data on domain-spoofing threats available in earlier releases. Also new is support for both Splunk Enterprise and Splunk Cloud.
Boosting Visibility Into a Growing Threat
Splunk Enterprise and Splunk Cloud are SIEM solutions that ingest and analyze a high volume of data to quickly detect threats within an organization's IT environment—unifying security alerts within a common data store and user interface. With these solutions, security teams can identify, prioritize, and manage security events with event sequencing, alert management, risk scores, and customizable dashboards and visualizations.
For SOC teams suffering from alert fatigue, real-time visibility into verified phishing threats within their extended email ecosystem is paramount. Without it, the risk of compromise grows unchecked, limiting the ability to prioritize and manage potentially costly security events. To get the intel they need, analysts are often forced to switch from console to console to collect data, wasting time while potentially missing new threats that emerge between logins.
Agari Integrated Email Threat Data is the Answer
The Agari App for Splunk collects data from both the Agari DMARC Protection and Cloud Email Protection products and then allows analysts to view and query that data from within their Splunk instance.
Agari solutions have the proven ability to detect and block both inbound and outbound email attacks from reaching employees, partners, and customers while safeguarding brand reputation. Built with open APIs, our solutions deliver better security, reduce costs, and support a dynamic and agile environment. Combined with Splunk, the benefits only increase. Key highlights include:
- The Agari App for Splunk integrates with the Agari platform and ingests events from Agari DMARC Protection and with this new release, Cloud Email Protection.
- Analysts have the ability to configure supported APIs for ingest, and they can also view and query data from a number of preconfigured searches.
- The app includes more than 10 pre-configured dashboards that enable quick visual inspection and identity policy hits on top attack types, top users attacked, brand spoofing alerts, failure samples, and more.
A Single, Easily Integrated Solution—On-Premises or in the Cloud
One of the key enhancements in the Agari App for Splunk is support for Splunk Enterprise for on-premises environments and Splunk Cloud within a single application.
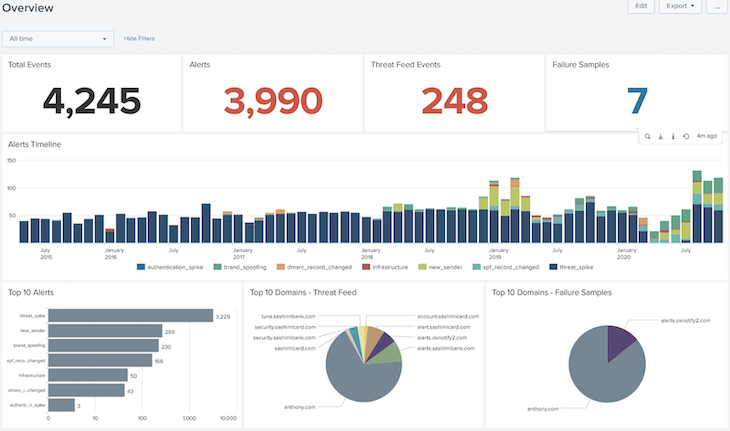 Preconfigured Agari DMARC Protection Dashboard for Splunk SIEM
Preconfigured Agari DMARC Protection Dashboard for Splunk SIEM
While a growing number of organizations enjoy the benefits that come with moving to the cloud, many are also discovering the added complexities involved with securing cloud-connected operations within and between companies. As a result, many have come to rely on Splunk Cloud for deep insight into their cloud and hybrid security ecosystems and applications.
This new release marks the first time Agari email threat data has been made available through an easily-integrated data connector for Splunk Cloud—enabling security teams to optimize the effectiveness of their Splunk SIEM before phishing attacks lead to a breach or scam.
According to industry reports, 80% of organizations saw a sharp rise in cyberattacks during 2020, the vast majority of them phishing and advanced email threats implicated in half of all business losses from cybercrime. But as the world transitions out of the pandemic, sophisticated new phishing strategies promise a whole new level of chaos in the months ahead.
By giving organizations a consolidated and granular view of the attacks against them, solutions like Splunk SIEM and Agari's integrated email threat data are key to protecting what is quickly becoming the first line of cyber-defense.
The Agari App for Splunk supports both Splunk Enterprise and Splunk Cloud, and is available today on Splunkbase. To learn more about integrating Agari email threat intelligence with Splunk, read our solution brief now.