Business email compromise (BEC) has grown into a billion dollar industry as cybercriminals use look-alike domains and display name deception to trick employees into revealing sensitive information, depositing money into criminally-owned bank accounts, and sending thousands of dollars in gift cards via email—all without ever touching a legitimate email account. When these criminals do gain access to an employee email account and use that access to spy on communications, gain knowledge of business operations, and send attacks on behalf of that employee, the damage can be much worse.
Unfortunately, this is not simply a hypothetical scenario... it’s a real problem affecting businesses worldwide. Here at Agari, we’ve coined it vendor email compromise, and it is being popularized by a cybercriminal group dubbed Silent Starling.
From Business Email Compromise to Cash-Out
Silent Starling, comprised of three main threat actors, has found success in compromising email accounts, gathering data from them, and then targeting appropriate contacts at the right time. The group consistently targets suppliers and vendors in their initial attacks, using phishing emails to encourage employees to divulge passwords, which can then be used to access the email account. Once this information is available, Silent Starling sets up a forwarding rule so the group receives copies of all emails into the account.
From there, Silent Starling diverges from a typical BEC group by showing extreme patience—oftentimes waiting months to gather information about employee behavior, standard invoice design, and other financial information that will be useful in an attack. When the time is right, the group will strike. At this point, they use either the original compromised account (or one very similar) to target the vendor’s customer, asking for payment on an invoice. And because the email looks exactly like one they are expecting, only with updated banking details, the customer is likely to fall for the scam. 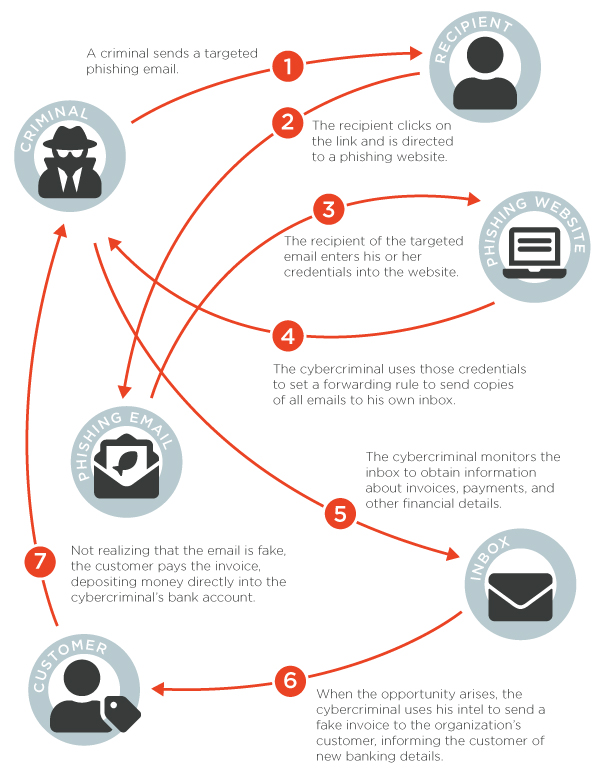
As you can see from the graphic above, the entity that is most impacted by a VEC attack is not the original victim of the initial attack where the account was compromised. Rather, is a completely separate organization—the compromised vendor’s customer. In a rather cruel twist, these customers have no control over the security of the system where the attack began and thus have no real way to defend against it.
Seeing Success with VEC
Since Silent Starling moved to vendor email compromise as a major attack type in 2018, the group has seen enormous success. In the course of our research, our team was able to document the successful infiltration of more than 700 employee email accounts spanning more than 500 companies. Combined, these accounts provided more than 20,000 sensitive emails, giving Silent Starling access to thousands of data points.
While a few of these compromised accounts were from users in Central America, East Asia, and Europe, nearly all of the victims were located in the United States, Canada, and the United Kingdom. 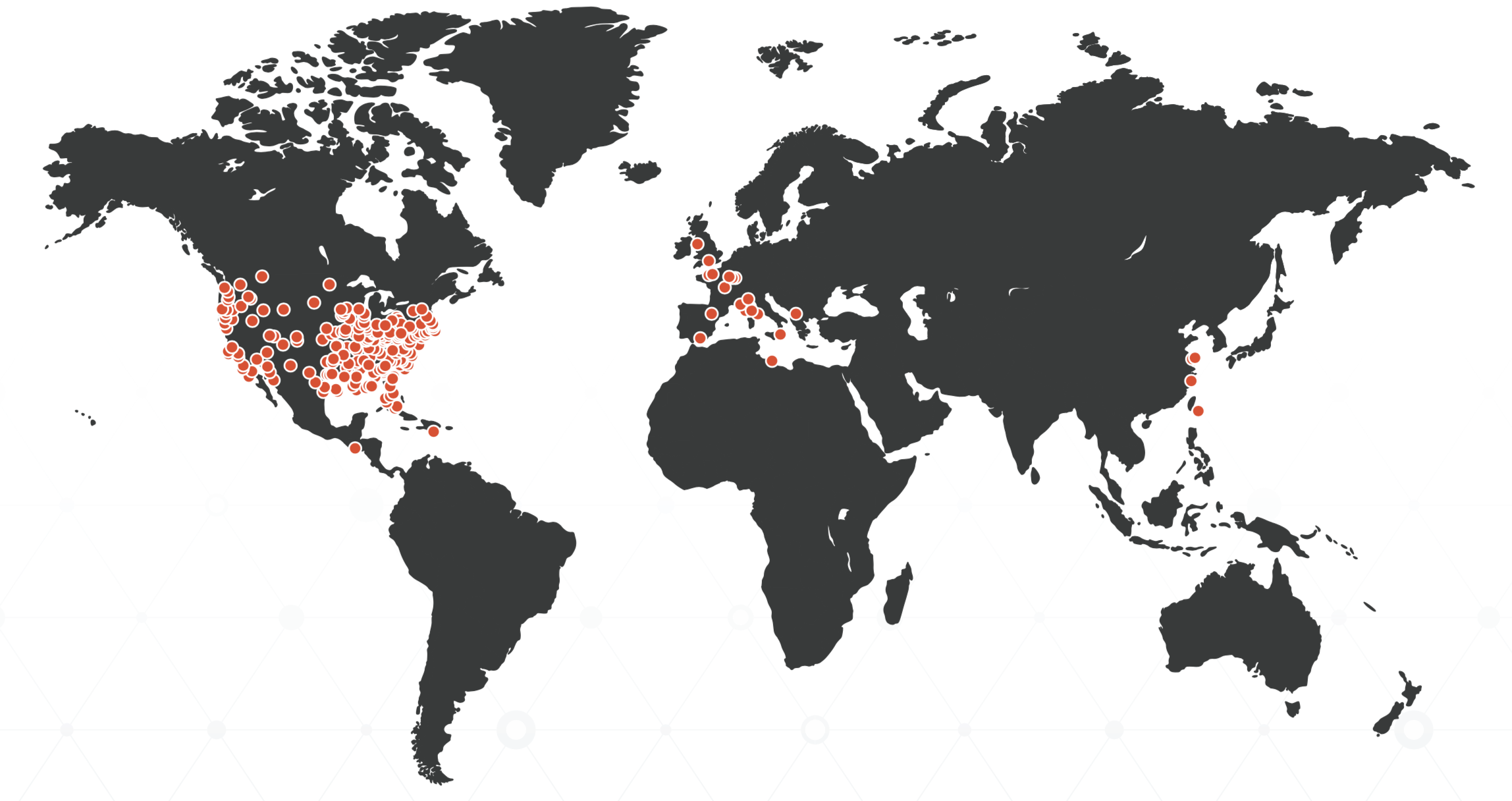
Further research into Silent Starling and others groups like it is needed to understand the full impact of this new type of crime, but we expect VEC to be the largest threat for organizations worldwide over the course of the next 12-18 months. As cybercriminals evolve this attack modality, these scams will proliferate,
Due to the nature of this scam, the red flags that people typically look for will are not there. Legacy email security providers do not have the ability to stop these attacks. And as a result, the financial impact will be harrowing, causing disruption throughout the global supply chain.
For more information on Silent Starling, download the full report or watch the webinar.