The secure email gateway (SEG) worked for decades, no doubt. It was truly the first line of defense against email-based threats that took advantage of people and technology to enable fraud. Those of us who have dedicated our lives to improving this industry are grateful for the work of companies like Symantec and Proofpoint, which have spent years protecting people and organizations from viruses and malware spread through malicious links and attachments.
Those solutions, though, no longer work against the new identity-based threats that dominate the email threat ecosystem today. Email and the threats against it are changing faster than ever before. To keep up, email security must do the same.
The Shift to Identity Impersonation
Legacy email security defenses worked for a number of years, but cybercriminals have since learned how to evade the systems that organizations put in place to protect against them. They have changed tactics, using new types of emails to con their victims out of millions. They no longer focus on spreading malware and viruses but instead use identity deception to trick their targets. In fact, the FBI estimates that 20,000 victims lost as much as $1.3 billion from business email compromise last year alone. And that’s just in the United States.
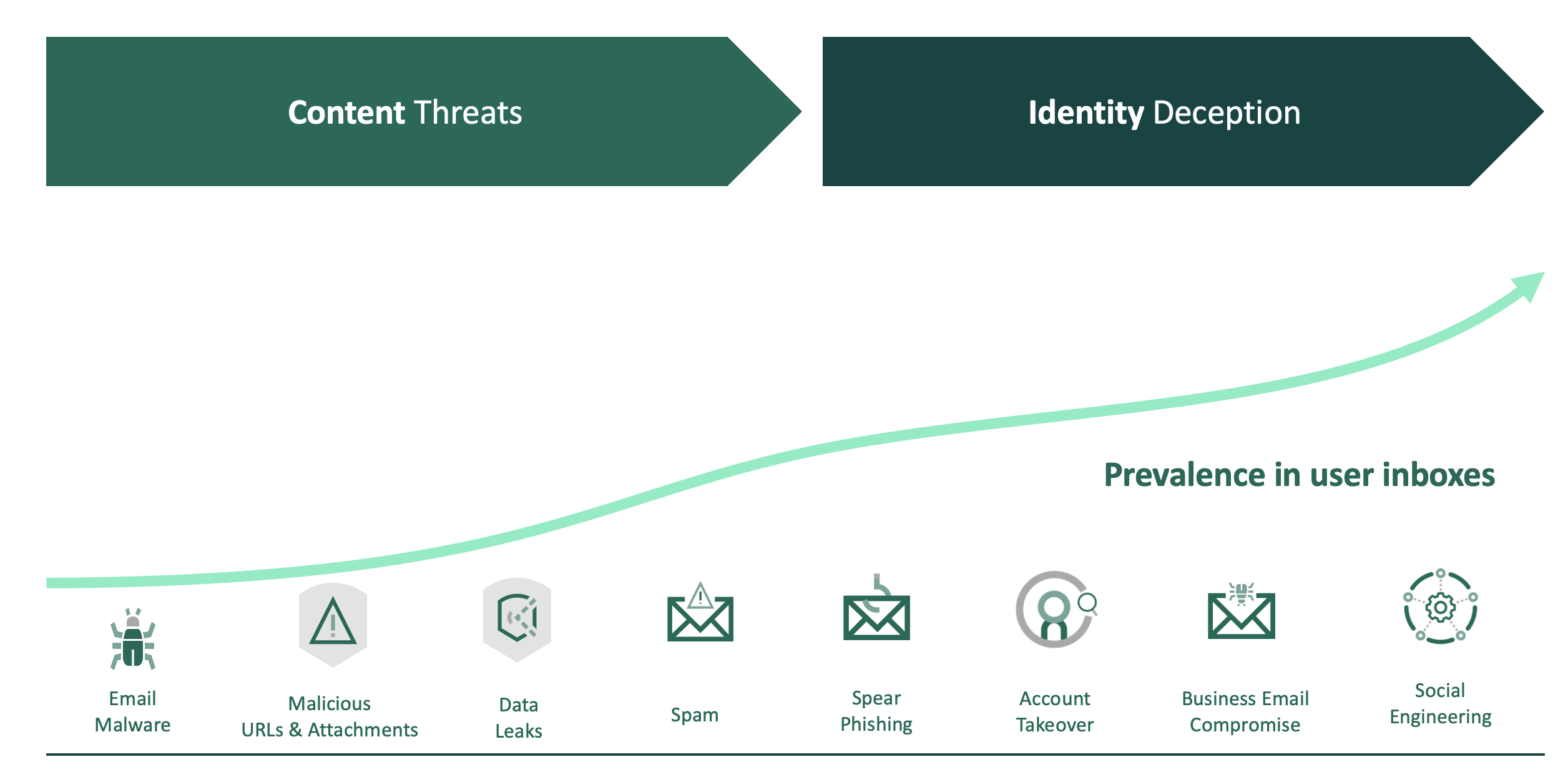
Attackers exploit security gaps in the underlying email protocols or the user interface constraints of email clients. As a result, they are able to send email messages that leverage the identity markers of trusted people and use deception techniques informed by social engineering to manipulate recipients into taking the desired action. These messages hide in plain sight, easily bypassing legacy security systems undetected, and use personal and professional context to defraud businesses and individuals.
Criminals scour websites like LinkedIn to determine relationships between people to make an email appear believable. The last barrier they encounter is figuring out ways to bypass the email security defenses, to score big. After all, once the email has been delivered, they can easily prey on human emotions to trick the recipient into wiring money or divulging sensitive information. As a result, email security protocols must be hardened to this type of attack.
The Shift to Cloud-Based Email Solutions
At the same time that cybercriminals are evolving their tactics, businesses are shedding on-premises infrastructure, moving en masse to cloud-based platforms such as Microsoft Office 365 or Google Workspace. These platforms provide native support for anti-spam, virus and malware blocking, email archiving, content filtering, and even sandboxing—a natural evolution as new technologies are developed in a better way than the preceding technologies. In the case of email, this means integrating services into the base platform that in the past were bolted on.
Designed to assess incoming emails by analyzing content and infrastructure reputation, these platform-native controls are proving essential to ferreting out spam, malicious URLs and malware, certain keywords, or a high volume of attacks from a single IP address. That said, they lack when it comes to protecting against the advanced email threats that use identity deception techniques. Clearly, a better solution—one designed for the cloud—is needed.
The Rise of Next-Generation Secure Email
This move to cloud-based email and the onslaught of zero-day attacks that successfully penetrate the inbox are shifting email security from signature-based inspection of email on receipt to continuous detection and response using machine learning to detect fraudulent emails and to hunt down latent threats that escaped initial detection or have activated post-delivery.
Enter the Data Science team from Fortra and their advanced techniques for detecting sophisticated attacks through a combination of machine learning, large language models (LLMs), and neural networks.
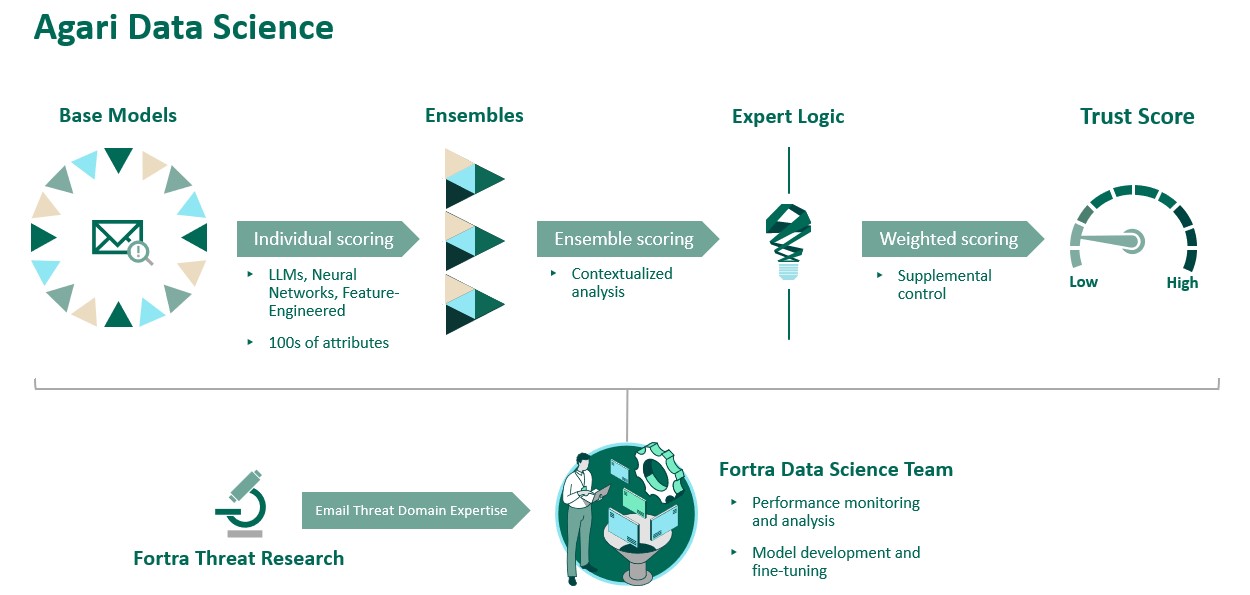
It is an approach that can’t readily be faked or spoofed because a fraudster typically doesn’t have a trusted pattern of communications with those they are intent on attacking. Even in scenarios where accounts have been compromised, behavioral anomalies can be detected. And once organizations adopt the Agari solution, there are simply easier targets in organizations that use less-effective alternatives. By using the to become a hardened target, attackers tend to turn their attention toward easier prey.
Learn more about the changing email security landscape and how Agari is prepared to protect against new threats in our exclusive white paper.