Email attacks using impersonation as their primary means of success are the top threats making it past Secure Email Gateways. These socially engineered messages have gradually increased in volume to overtake more malicious links or attachments typically used in payload campaigns targeting businesses.
In this series, we look at the top email impersonation threats based on the reported volume in user inboxes through Fortra’s PhishLabs’ SEA solution. Of the threat types, hybrid vishing has shown the greatest increase in volume, growing more than 266% from 2021 to 2022. Hybrid vishing is defined as a phish that uses both email and telephone communication to execute attacks.
How Do Email Impersonation Attacks Evade Security Controls?
Email impersonation attacks are communication-driven and range from a well-crafted message impersonating specific individuals to emails with little or no content at all. Common tactics include using lookalike domains, spoofed domains, and display name impersonation. They also rely heavily on stolen branding, such as logos or images.
Hybrid vishing may use any combination of these tactics in addition to incorporating a telephone number as the intended means of communication between the threat actor and the victim.
Below are examples of hybrid vishing emails in the two highest volume attack campaigns so far in 2023. These attacks bypassed each organization’s Secure Email Gateway (SEG) and were only detected through end user reports.
Example 1
The largest reported spike in hybrid vishing activity occurred February 8. The messages in the campaign were sent via a SendGrid account and largely targeted banking institutions. All reported emails bypassed the SEGs put into place by the targeted organizations.
In the campaign, the attacker used two different display names to deliver the messages:
Display Names:
Notification<[email protected]>
Karen smith<[email protected]>
Subject Line: Order 8NZGDM: OrderID#1248187 payment completed
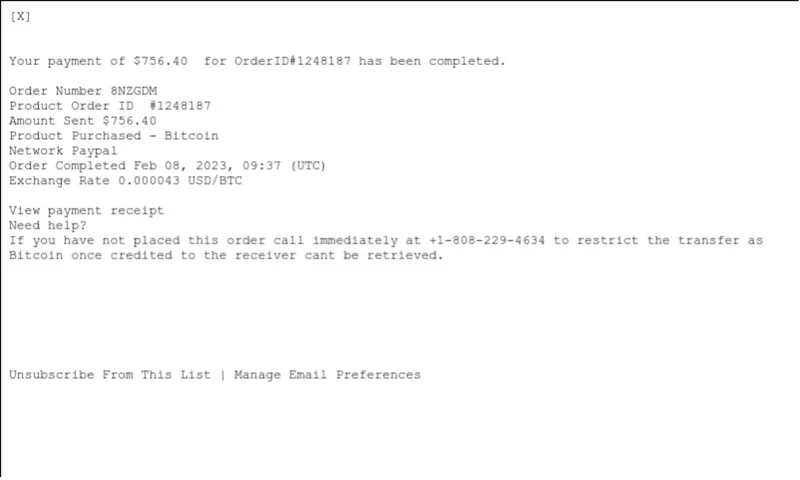
The threat actor formatted the message to look like a purchase receipt. In the message body they disclose details of the fake purchase and point to a phone number as the call to action.
If the victim calls the number provided in a hybrid vishing attack, they will either be connected with an automated system or fake representative playing to the theme of the email in an effort to gather sensitive information.
Example 2
The second largest spike in hybrid vishing activity occurred January 17, prior to the previous campaign. In the attack, the actor used a free Gmail account to send fake PayPal invoices. The messages in the campaign were given a Microsoft Spam Confidence Level (SCL) of 1, indicating the messages were safe and not spam.
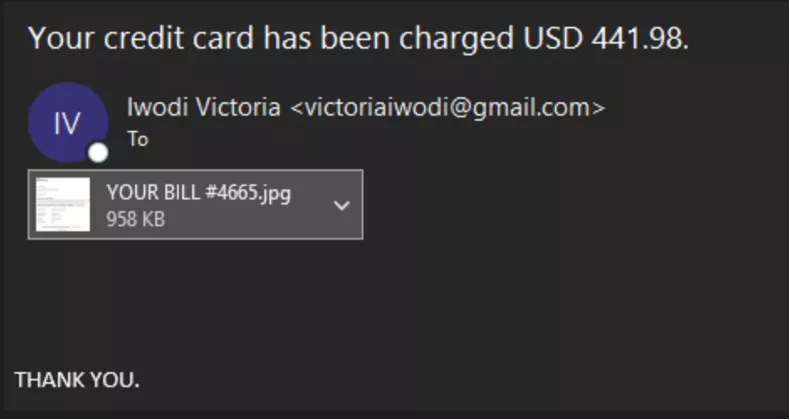
The only content within the body of the email are the words “THANK YOU”. A jpg is attached, labeled “YOUR BILL #4665”
Subject: Your credit card has been charged USD 441.98.
Sender Address: Iwodi Victoria <[email protected]>
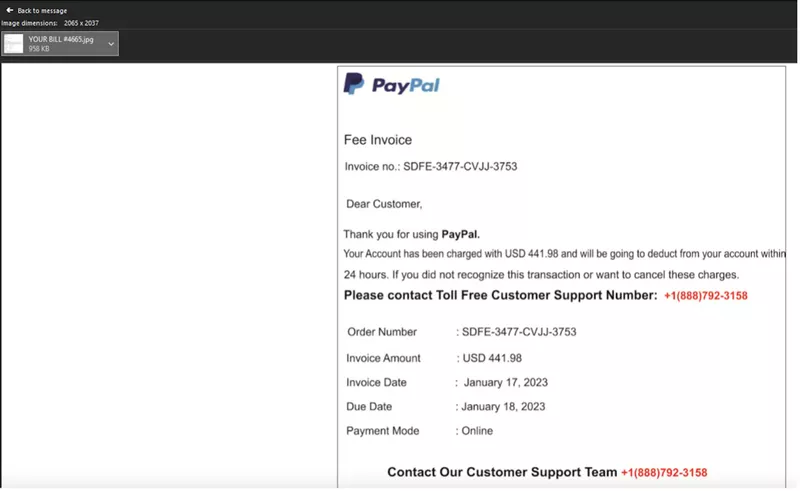
The fake PayPal invoice indicates a payment has been made and includes a number to call if the victim wishes to cancel the charges.
Combatting Email Impersonation Threats
Hybrid vishing threats are particularly difficult to detect, as they contain no apparent malicious indicators. Remediation of email impersonation threats such as these should take a three-pronged approach outside of reliance on traditional SEG protections, as these will fail to flag zero-day activity and attacks lacking known signatures. The following should be applied to all email impersonation threats.
Proactive, identity-based detection through AI-powered machine learning
Security teams should employ AI to stop response-based threats through traffic pattern analysis. This should be done through analyzing human relationships and their behaviors. This will allow security teams to identify known good email communications and trusted senders, as well as flag dangerous and often unassuming BEC, brand impersonation, and executive spoofing.
End User Reporting
Regardless of measures taken to defend your organization’s network perimeter, employees should be trained to identify and report suspicious messages that reach their inbox. In order to be effective, training programs should be engaging and customized to your business needs. The content should be delivered regularly, in an easily consumable format and should mirror real-world phishing scenarios that they could potentially encounter.
Post-Delivery Analysis
The analysis and documentation of response-based threat indicators is critical to enhancing security defenses. File hashes, email addresses, URLs, and any other intelligence that can be collected should be gathered and fed back into existing security architectures.
Email impersonation threats are the fastest growing sector of online attacks. They are generally easy to craft and use words and phrases to influence victims into performing desired actions. To stay ahead of email impersonation attacks, security teams should implement multiple layers of protection, including identity detection measures, reporting mechanisms, and robust analysis solutions.
Learn how PhishLabs’ SEA protects against email impersonation.
