DMARC builds on two earlier email authentication standards: SPF (Sender Policy Framework) and DKIM (DomainKeys Identified Mail). DMARC was a critical development because both of these earlier standards, while effective, contain important gaps.
Why is DMARC Important?
Unless you’re one of the rare people on the planet that doesn’t use email for business and personal communications, you know that although email is both easy and convenient, it’s also increasingly fraught with risk. The very ubiquitous nature of email has made it a fertile target for hackers, spoofers and others with nefarious intent. Email’s fundamental flaw is that anyone can use someone else’s email address to send a message. In fact, it’s trivially easy, using just a little bit of computer code, to create messages that appear to come from any address you want.
To combat this risk, DMARC (Domain-based Message Authentication, Reporting and Conformance) was developed.
For instance, SPF only validates the email address shown in a message’s Return-Path field. Recipients of email messages don’t usually see that field, and consequently, phishers can easily use a legitimate, SPF-authenticated address in the Return-Path (for example, [email protected]) while putting an impersonated name in the From field displayed as a spoofed address (e.g. [email protected]) — and recipients will be none the wiser.
DKIM has a similar flaw: Phishers can sign a message with a valid DKIM signature that has no connection whatsoever to the address shown in the From field. DMARC fixes that problem by requiring alignment between the SPF address, the DKIM address, and the address that appears in the From field of a message.
Why DMARC is Effective?
Using DMARC is effective because it sets a policy that tells receiving email servers what to do with emails that don’t authenticate and provides a reporting mechanism so that receivers can tell domain owners about emails sent using their domain and whether they authenticated or not.
DMARC is designed to be deployed in stages. Companies generally start in “monitor mode” by setting up DMARC tags, which are the language of the DMARC standard. They tell the email receiver to check for DMARC and what to do with messages that fail DMARC authentication. The “rua” tag indicates where aggregate DMARC reports should be sent. Senders designate the destination address in the following format: [email protected]. Similarly, the “ruf” tag indicates where forensic DMARC reports should be sent.
Normally a “p=none” policy is the first stage, meaning no action is taken. Rather, the domain owner uses this information to make adjustments to their SPF and DKIM configurations until all of their legitimate mail sources are properly authenticating. At this point, the policy can be tightened to “p=quarantine.” The email will still be accepted by the receiver, but the receiver will decide how they want to implement the quarantine policy, usually by delivering the email to the recipient’s spam folder. The next step is to set the DMARC policy to reject (p=reject), which only allows authenticated and trusted emails to reach the recipient’s inbox. Setting a DMARC policy to reject ensures that bad email is blocked; the intended recipient of the malicious email will never be aware of the email in the first place.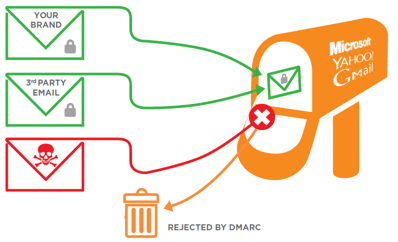
DMARC is designed to:
- Minimize false positives
- Provide robust authentication reporting
- Assert sender policy at receivers
- Reduce successful phishing delivery
- Work at Internet scale
- Minimize complexity
Once implemented, DMARC is very effective at blocking emails from nefarious and unwanted sources. However, because DMARC does not distinguish between inbound and outbound emails, the organization must conduct extensive analysis during the monitor and quarantine phases before moving to a policy of reject to ensure that legitimate business email communications to their consumers are not interrupted and the overall business is not impacted. This whole process of publishing a DMARC enforcement policy can take as long as 18 months, during which employees of the organization are constantly at risk of being attacked.
The Concept of Rapid DMARC
In response to this threat, Agari developed Rapid DMARC. Rapid DMARC takes the concept of a DMARC p=reject policy to prevent domain spoofing on workers and employs it immediately instead of having to wait for up to 18 months for a DMARC enforcement policy to be published.
Rapid DMARC is powered by the Agari Identity Graph™. The fundamental goal is to model the email-sending behavior of all legitimate senders across the Internet and to update these sending behavioral models in real-time. Using Internet-scale sources of email telemetry that include DMARC authentication data from over two trillion emails sent annually, patented scalable algorithms, and real-time advanced machine learning, accurate determinations of trusted and untrusted senders can be modeled.
When an organization leverages Rapid DMARC, the system inventories all the domains of that organization and analyzes the email senders that send email using these domains. Using historical knowledge from even before the organization implemented Rapid DMARC, including the sending behavior models for well-known senders that typically send email on behalf of organizations, such as MailChimp, Constant Contact, Salesforce, Marketo and SendGrid, the system maps these well-known senders to emails sent on behalf of the organization. Additionally, the system can map untrusted senders alerting the organization that someone is spoofing their domains and that they’re coming from a known malicious source. At this point the organization can enforce a policy to automatically quarantine or delete any message that is coming from an untrusted sender, keeping their employees safe.
All of this can be accomplished without having to complete the long process of publishing a DMARC record.
By analyzing an organization’s sender inventory and utilizing historical data, Rapid DMARC does an excellent job of protecting employees from receiving unwanted or malicious emails. However, to fully protect its customers, an organization will ultimately have to publish a DMARC policy. The good news is that since Rapid DMARC builds an organization’s sender inventory, a large part of the work to publish a DMARC record is already done, ultimately saving time and resources.
The significant advantage of deploying Rapid DMARC is that the sender inventory analysis occurs immediately when the system is deployed, providing instant protection from impersonation. Additionally, the extensive work that Agari has done over the past several years with well-known senders ensures a high level of efficacy and accuracy without an organization having to publish a DMARC record and manually monitor inbound senders, reducing the time to value from months to a matter of minutes.
Email will continue to be a ubiquitous form of business communication meaning that cybercriminals will continue to use email as a venue for phishing attacks and attempts to spoof your domains. However, the journey to protecting all your employees does not have to wait. Using Rapid DMARC, Agari can help you navigate this path quickly and efficiently.
To learn how to protect your customers, visit Agari DMARC Protection™.
To learn how to protect your employees, visit Cloud Email Protection.
