Organizations face a growing danger from phishing and ransomware, which have been the most common forms of cybercrime in recent years. Most businesses have fallen victim to phishing or ransomware attacks at some point. Every business needs to act against the growing threat of phishing, the primary method through which ransomware and other malware are spread. On the bright side, organizations have a lot of flexibility in how they respond to these threats.
Ransomware - a persisting threat
ENISA defines ransomware as “a type of attack where threat actors take control of a target’s assets and demand a ransom in exchange for the return of the asset’s availability and confidentiality.”
Every ransomware assault consists of three main parts: holding assets hostage, carrying out malicious acts, and threatening victims. Assets are things that contribute to the success of a company or group. Most ransomware attacks target data files and directories. Locking, encrypting, erasing, and stealing are the four main actions of ransomware. Finally, ransomware attacks rely on blackmail to achieve their goals, with criminals using threats to compel the target(s) into giving them something in exchange for the availability of their assets.
Businesses of any size are susceptible to ransomware's devastating effects. Ransomware is capable of encrypting any valuable material or assets and holding them hostage, including personal and company files, financial and healthcare information, network share files (containing sensitive employee data, intellectual property, or consumer data), and other valuable content.
To understand the threat ransomware poses to businesses, it is useful to look at some statistics. The average ransom payment in Q3 2022 has increased to reach $258,143*, while the median ransom payment grew to $41,987. According to ENISA’s Threat Landscape 2022 report, ransomware attacks rank the highest during the surveyed period (July 2021 – July 2022).
A joint advisory by the cybersecurity agencies of in the United States, the UK, Australia, and Canada notes “an increase in sophisticated, high-impact ransomware incidents against critical infrastructure organizations globally.” The same report says that as ransomware tactics and techniques continue to evolve, this is a demonstration of “. . .ransomware threat actors’ growing technological sophistication and an increased ransomware threat to organizations globally.”
Email phishing is the most common ransomware delivery method
Many companies and government institutions that have been hit by ransomware have been reluctant to discuss what led to the infestations, but many admit that the successful attack was the result of employees falling for phishing emails.
The FBI, CISA, and NCSC all agree that phishing emails, compromised remote desktop connections, and exploiting software flaws are the most common ways that ransomware gets into a system. According to ENISA's findings, "phishing is the most used attack vector to gain an initial foothold in an organization."
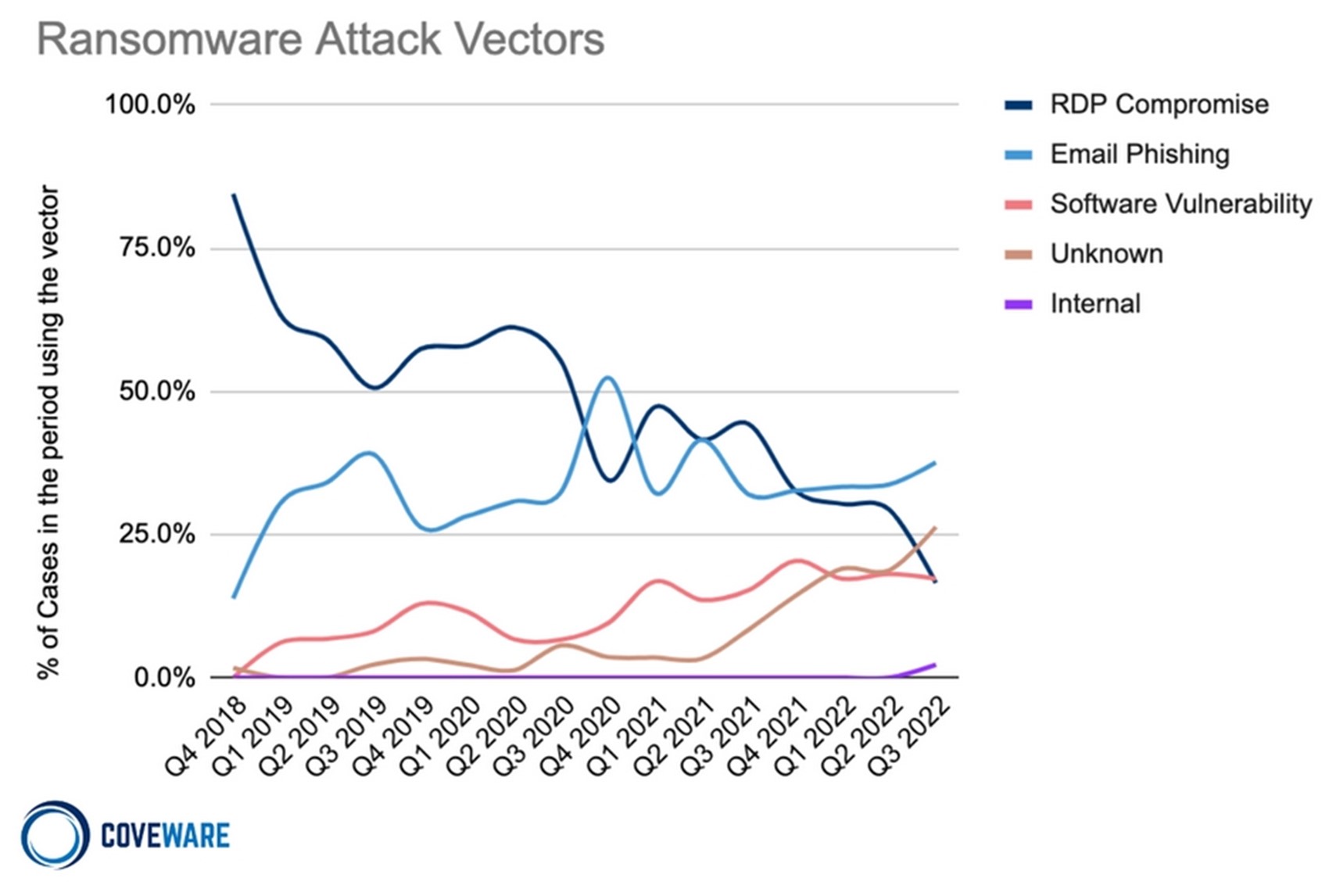
*Figure 1: Most common ransomware vectors. Source: Coveware
“Phishing attacks are carried out in high volume and target a broad audience, while other social engineering attacks make use of custom campaigns tailored to target specific employees. Using social engineering, threat actors leverage an employees' access inside an organization to gain a technical foothold in the network from which they carry out further attacks,” explains the ENISA report.
Why is email phishing so successful?
Employees today are suffering from "infobesity" as a result of their inboxes, making them less likely to be vigilant in detecting phishing efforts. A phishing email is easy to create, and cybercriminals are creative in their attempts to deceive people, coming up with new ways to disguise their content and avoid detection (via customization of content, copy of brand guidelines, etc.). In addition, cybercriminals exploit the personal information they glean from social media to send more convincing phishing emails.
Criminals use phishing emails to try to trick us into giving them personal information by appealing to our emotions. Each of us has both a fast and a slow mode of processing information, as demonstrated by the field of behavioral economics. When we take our time and consider the situation, we are more mature and sensible, deliberate, and logical. The goal of cybercriminals is to have us think otherwise. They want to force us to think quickly while we are still susceptible, emotional, and simple to control. Thus, fraudsters appeal to our emotions to trick us into opening suspicious links in email bodies, downloading malicious files, and disclosing confidential information.
Finally, employees may not receive appropriate training on how to recognize and avoid unexpected dangers, as well as how phishing can be used to spread ransomware. Hence, they are not sufficiently cautious when they receive requests to do things like send money, open attachments, or reveal private information. Unfortunately, some businesses aren't even thinking about making user education and awareness a part of their protection strategy.
How to shore up your defenses
Threat actors are reiterating their tactics, methods, and procedures (TTPs) on both payload and delivery campaigns due to the rapid awareness and reaction to phishing and ransomware. This perseverance shows that only concentrating on technology, with an emphasis on procuring, deploying, and optimizing security solutions, is insufficient.
Without a phishing defense strategy in place, businesses are vulnerable to not only the widespread phishing emails used to transmit ransomware but also the less noticeable emails used to deliver the same infection for years. Employees can be equipped to function as "human sensors" for detecting phishing attempts and as allies in preventing threat actors from obtaining a foothold in the organization if they are made aware of the potential for such assaults and given the tools to recognize them.
Therefore, businesses should consider the following mitigations:
- To assist employees to make safer choices regarding the emails they open, the links they click on social media, the websites they visit, and the methods they use to access the internet, businesses should create security awareness programs. If we want the "human firewall" to be an effective first line of protection against more complex phishing and ransomware, we must devote appropriate resources to their training.
- However, we all have times of vulnerability, and phishers bank on us being unprotected at inopportune times. In such a situation, you must use email security technology that can detect phishing attempts in email in ways that go beyond the typical red flags.
- Support your technology with actionable and real-time threat intelligence for additional protection against advanced phishing techniques and social engineering.
- Require all accounts with password logins to have strong, unique passwords (for instance use a password manager) and mandate the use of multi-factor authentication (MFA) whenever and wherever possible.
Download our latest whitepaper, “A Window on Email Security: Protecting Your Business from Hidden Email Threats” to learn more about the risks of unprotected email and more importantly, what you can do about it.