Cybercriminals doubled down on popular threat types and preferred malicious software in Q2, with O365 phish and QBot malware dominating inboxes by significant margins. QBot operations eclipsed all other malware once again, reaching their highest volume of share just before a multinational takedown Tuesday removed malicious code from more than 700,000 computers.
Similarly, but lacking in disruption, the volume of email phish impersonating Microsoft O365 jumped, making up more than half of all reported credential theft attacks. O365 phish increased 11% of share over Q1, bringing the total volume of this threat type to the highest it has been since this time last year. O365 phish were the leading threat type in Q2, overcoming the second most reported 419 scams by more than 10%.
Every quarter, PhishLabs analyzes hundreds of thousands of phishing attacks targeting enterprises, brands, and employees. In this post we discuss the types of malicious emails making it into employee inboxes most, using intelligence collected through Fortra's Suspicious Email Analysis solution.
Employee Reported Emails
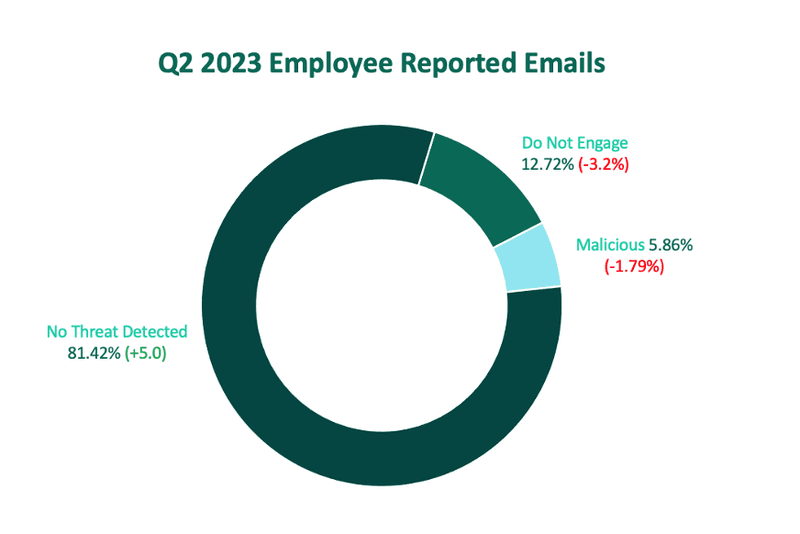
In Q2, employee-reported emails classified as malicious and as untrustworthy (Do Not Engage) both declined for the first time since 2021. This decline comes after a spike in Q1, where the combination of categories reached its highest volume since reporting on this dataset.
Emails considered untrustworthy saw the greatest decline in share, dropping more than 3%. Untrustworthy emails are defined as suspicious messages that require interaction with the sender to verify malicious intent.
The share of volume of malicious emails dropped 1.79%, totaling nearly 6% of overall reported email volume.
Emails that contained no threat increased for the first time in five quarters, making up more than 81% of reports.
Top Email Threat Categories
Credential Theft Attacks
Credential Theft Attacks led all malicious threat types in Q2, despite declining 1.7% of share from Q1. PhishLabs breaks Credential Theft into two categories:
- Phishing Attachments that redirect the victim to malicious websites
- Phishing Links that point victims to malicious websites
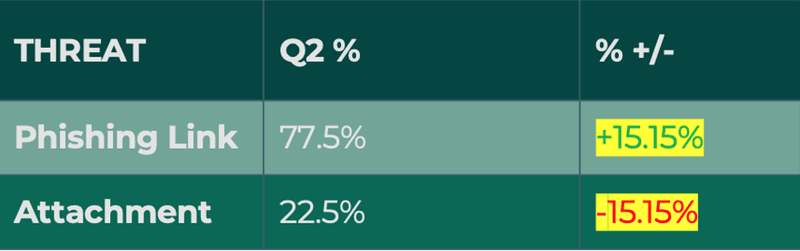
Emails containing attachments declined in Q2, dropping to 37.6% of Credential Theft volume.
The volume of emails containing phishing links jumped more than 15%, making up 77.5% of reports. More than half of these reports were composed of Office 365 phish. O365 attacks have seen an increase of more than 10% of share of volume for two consecutive quarters. Phishing emails impersonating productivity software such as Microsoft are particularly desirable to cybercriminals, as access to a set of these credentials can mean widespread compromise across a variety of accounts and tools.
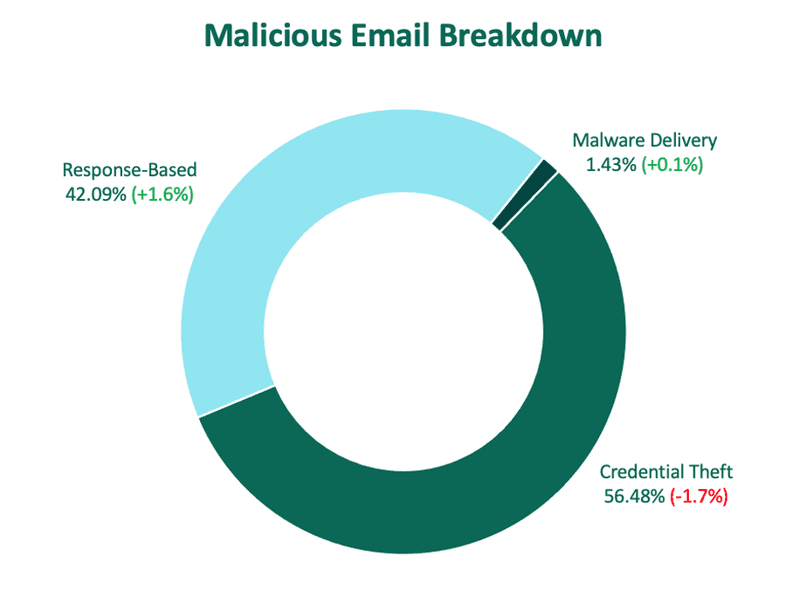
Response-Based Attacks
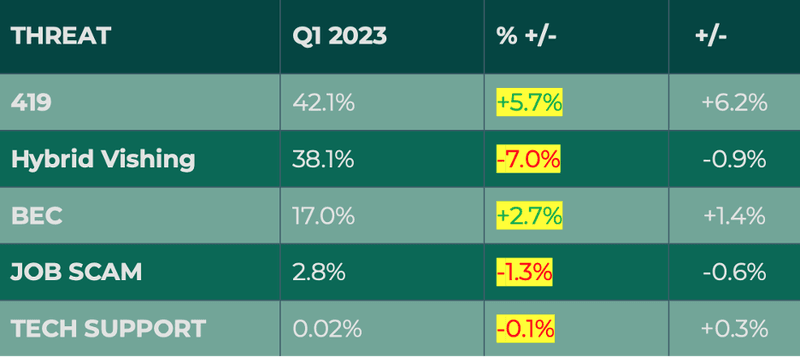
Email threats categorized as response-based increased slightly, making up just over 42% of reported malicious activity. Within the group, 419 (or Advance-Fee Fraud) were back on top as the most reported threat type, with 42.1% of volume. While 419 scams have been one of the longest running and most popular means of tricking victims via email, this threat type has recently waned in comparison to newcomer hybrid vishing.
Hybrid vishing broke its two-quarter streak as the most reported response-based threat after a 7% decline from Q1. Despite this, hybrid vishing still made up nearly 40% of malicious volume. Hybrid vishing breaks away from what is traditionally known as vishing or, phishing scams executed exclusively via phone. In a hybrid vishing attack, the cybercriminal initially makes contact with the intended victim through a phishing email. Within the body of that email there is a phone number listed for the receiver to call to contact the sender. Often, the call to action in these attacks is to speak with a phony representative to confirm or contend a “recent purchase”, or to speak with a support team regarding a technical issue or renewal.
Business Email Compromise (BEC) grew 2.7% in Q2, making up 17% of total response-based volume. This is the second consecutive quarter BEC has shown an increase.
Both job and tech support scams declined, making up 2.8% and .02%, respectively.
Malware Attacks
An international operation spearheaded by the FBI Tuesday has led to the disruption of the QBot network. As part of the takedown, QBot has been uninstalled from more than 700,000 infected computers. QBot has been the malware of choice for cybercriminals for multiple quarters, responsible for widespread infections and millions of dollars in damage.
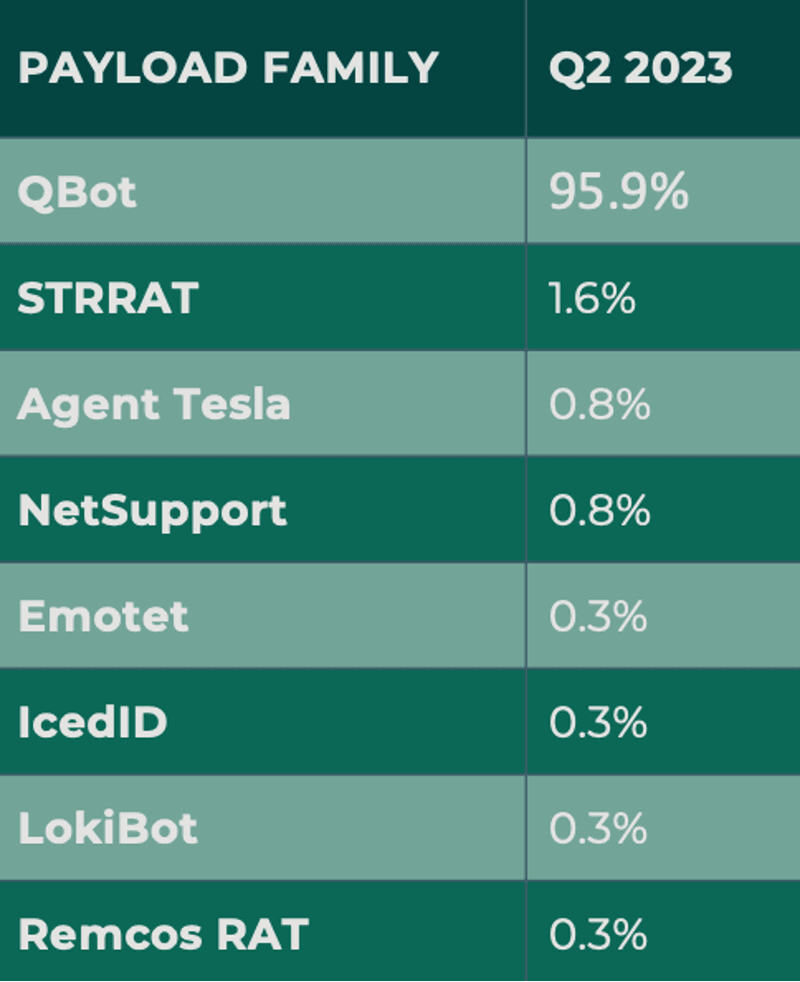
In Q2 specifically, QBot led all other malware varieties with nearly 96% of total attack volume. This represented a nearly 10% gain in share over the previous quarter. QBot has remained a highly resilient banking trojan-turned-backdoor delivered via a variety of file types. Similar to Emotet, the QBot C2 infrastructure was widespread, with compromised systems used to exfiltrate data, download additional malware, and provide access to other criminals.
Java-based STRRAT was the second most reported payload in Q2, representing 1.6% of total volume. First detected in 2020, STRRAT is capable of stealing credentials and controlling infected devices remotely.
As a whole, malware reported in inboxes increased by less than a percent, bringing its volume to 1.4% of overall malicious activity.
The methods cybercriminals choose to target victims is ever-changing and often challenging to predict. In Q2, cybercriminals abused the Microsoft brand more than in Q1 with greater than 50% of all emails containing phishing links impersonating O365. In the response-based group, 419 scams claimed the top spot once more, proving the timelessness of the tried and true Advance-Fee Fraud. And prior to Tuesday’s takedown, QBot continued its streak as the top malware by an overwhelming margin.
Learn how PhishLabs helps prevent email attacks.