QBot, the leading payload family in Q3, was disrupted as part of a coordinated, multinational operation led by the FBI on August 29, 2023. This resulted in the removal of 700,000 QBot payloads from infected devices across the globe, and interrupted the activity of one of the most active malware families since the former juggernaut Emotet, which was disrupted in 2021.
While QBot led all other payload volume in Q3 prior to takedown, there have been zero reports of QBot activity by end users since August 29. In its place, multiple payload families have stepped up, with Remcos RAT, AsyncRAT, and NetSupport each representing more than 10% of total payload volume. This is the first time any payloads other than QBot have displayed that great of volume since the beginning of 2023.
Email payloads remain the primary delivery method of ransomware targeting organizations. PhishLabs continuously monitors payload families reported in corporate inboxes to help mitigate attacks targeting their businesses. Below are the top payload threats to enterprises in Q3.
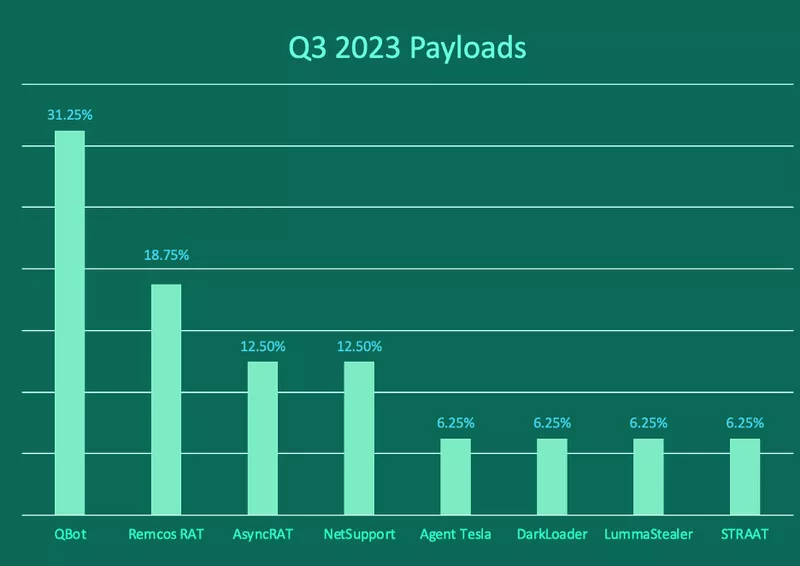
Q3 payload volume
QBot
Despite the QBot operational disruption on August 29, its volume in Q3 was great enough prior to takedown to lead all other payload families for the quarter, contributing to 31.25% of total reports. This was the fourth consecutive quarter where QBot volume topped all other families, even with zero reports in September.
QBot has been around since 2007, with bad actors consistently refining tactics to expand operational reach and enhance attack success. While the removal of Qbot payloads from 700,000 devices is considered a success, self-propagation capabilities of the payload, as well as its role as an initial access provider for other malicious software, means infections could still live in systems. At this time, the long-term impacts to QBot operations remain to be seen.
Below is a Qbot phish pre takedown. In the attack, the payload is delivered via malicious attachment. This example is targeting a financial institution.

QBot phish
Remcos RAT
Remcos RAT was the second most reported payload in Q3 with 18.75% of total volume. Remcos RAT (Remote Control and Surveillance RAT) is a legitimate remote access tool-turned-weapon that has been available online since 2016. Remcos is most frequently delivered in phishing emails and is capable of manipulating compromised systems to exfiltrate sensitive information.
Features of Remcos RAT include grabbing screenshots, keylogging, and recording audio. The payload is also capable of granting backdoor access to the infected network.
Below is a Remcos RAT phishing email delivering the payload via a link. The attack is targeting a global financial institution.
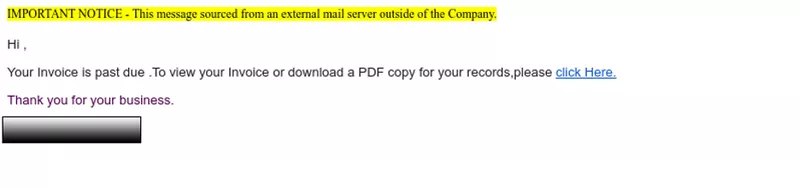
Remcos RAT phish
AsyncRAT and NetSupport
AsyncRAT and NetSupport both contributed to 12.5% of total payload volume in Q3. Like Remcos RAT, they are legitimate remote admin tools designed to provide device support but are commonly abused by bad actors.
AsyncRAT and NetSupport are delivered via phishing attacks containing malicious attachments and links. Once installed, actors are capable of monitoring and controlling infected devices remotely. Functions include keylogging, screen-grabbing, and various evasion techniques.
Both RATs have the ability to download and execute files, allowing actors to deliver additional payloads to the compromised device.
Below are examples of recent phishing attacks delivering AsyncRAT and NetSupport.
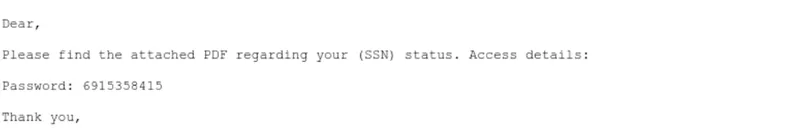
AsyncRAT phish delivered via attachment targeting a global financial institution

NetSupport phish containing link targeting a healthcare organization
The QBot disruption has put the rest of the malware landscape on display, as security teams wait to see which payload family will rise up to take its place. Similar to Emotet’s takedown, it remains to be seen whether QBot is gone for good or if actors will use this time to regroup and eventually reemerge. PhishLabs will continue to monitor the payload landscape to ensure that organizations have the most up-to-date information to better protect against malware attacks.
Learn how PhishLabs prevents and protects against damaging payload attacks.
