Companies are flocking to Office 365 as the leading choice of cloud-based email. But while it’s a great productivity enhancer and provides simplicity and cost savings over on-premises solutions, it raises serious security challenges. Threat actors typically target email accounts with identity deception. And with Office 365 being ubiquitous and publicly-discoverable, the risks become even greater.
The Email Attack Vector
Email is the number one attack vector for cyber crime, comprising the entry-point for more than 95% of cyber attacks over the last 10 years. While in the past, many attacks tended to use malware, a new breed of threats are focused around identity deception and social engineering. Attacks are often customized and seeded with facts and context that the recipient might expect to see from a trusted sender.
Many of these attacks leverage identity deception at their core. While Office 365 includes layers for spam and malware, it doesn’t protect you against socially engineered attacks that are either phishing for credentials or motivating an employee to handle an urgent payment. Often these latter attacks show email history from superiors within the thread history. When an operational worker sees an email passed from her CEO to the CFO, with a cc: to her manager, there is immense pressure to perform the task. No one wants to be the bottleneck and this pressure undermines workers’ judgment; and criminals exploit this in their strategies.
Deception Detection
Agari took a unique approach to this problem a number of years ago by focusing on deception detection and filtering good behavior. Let’s break this down.
Agari looks at the identity of the sender to determine trust. The Agari Email Trust Platform is the only solution that verifies trusted email identities based on insight into 10 billion emails per day to stop advanced email threats that use identity deception.
But the next step is even more critical than the last. It consists of filtering out the more consistent good behavior to expose the bad. Note that this is in stark contrast to spam engines which try to filter out unwanted emails by focusing on the bad.
Good Versus Bad
One might think that creative innovators (the good guys) would be constantly evolving their business. While this is true, even the most revolutionary business approach tends to work within the constructs of known identities and established communication channels. 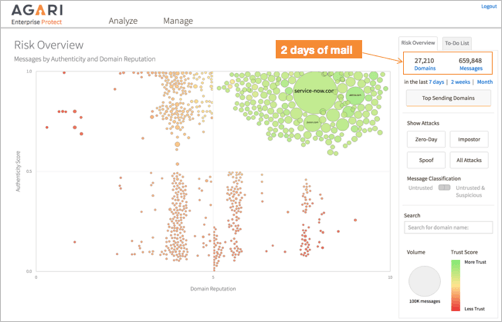
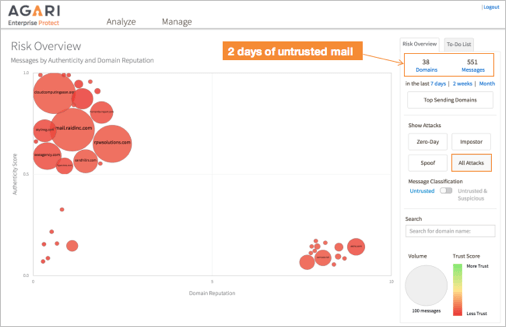
By modeling and subtracting out good behavior (left), the bad becomes visible (right).
On the other hand, a criminal trying to deceive will often use many different methods (and infrastructure) to do so. They might use one set of servers one time, and another a different day. They might impersonate one person for one operation and take over someone else’s email account for the next. They tend to be constantly looking for which door is open and this shows up behaviorally as inconsistent history in terms of relationships and internet infrastructure.
So by modeling the consistent good behavior, we can ultimately subtract this out to expose the less consistent, ever-changing bad behavior. With this method, even deceptive emails that have no malware or URLs can be stopped. And this is the missing link that can secure your Office 365 email channel from targeted phishing and BEC attacks, keeping your company productive and secure.
Learn more about securing Office 365 with Agari.