Recent research conducted by Agari showed that Business Email Compromise (BEC) attacks are running rampant with 96% of organizations experiencing an attack during the second half of 2017. To compile the report, Agari analyzed over 1 billion emails that were considered safe by conventional security technologies. Our analysis showed that BEC was one of the predominant methods used by cyber criminals. BEC attacks are particularly effective because they have no payload, such as a malicious attachment or URL, so they are able to slip past most of the conventional security technology that organizations use to protect themselves.
BEC is Big Business
BEC attacks leverage social engineering, impersonating trusted individuals, such as bosses and third-party vendors, to request wire payments or sensitive data such as W-2 tax forms. Social networks and free cloud email services make it simple for cyber criminals to identify their targets, create an email account that impersonates a trusted entity (the CEO, the brand, or a partner) and then create a believable con with personalized details to make a fraudulent request. It continues to be a big, and costly, problem. According to the FBI, BEC attacks were responsible for more than $5.3 billion in losses between 2013 and 2016.
Not one size fits all
BEC attacks inherently rely on identity deception to slip through defenses. The three most common types are: display name deception, domain spoofing, and look-alike domains.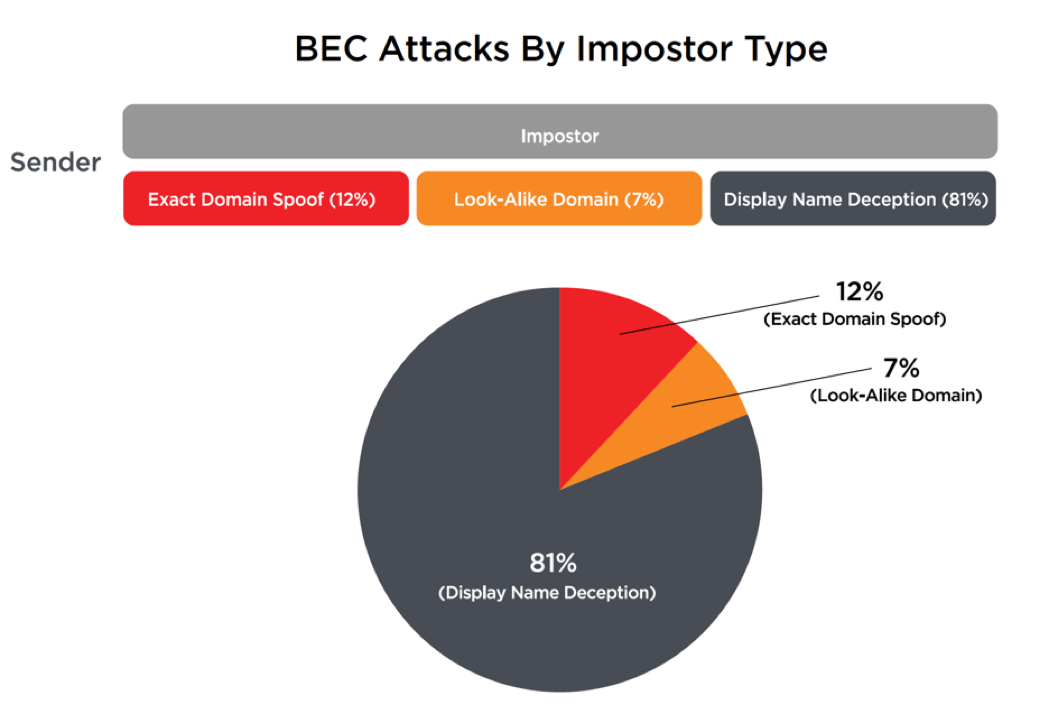
In a display name deception attack, the criminal uses a display name that is the same or very similar to that of the impersonated party. Since most people determine the identity of the sender simply by looking at the display name, this attack is very successful. The most common type of display name attack uses free webmail accounts, but some criminals go further and register their own domains.
Domain spoofing attacks attempt to forge a legitimate sending domain, along with their delivery paths. Finally, look-alike domain attacks based use deceptive-looking domains under the control of an attacker. There are two principal types of look-alike domains. The “traditional” type looks like the domain of the impersonated organization—for example, “agarii.com” (with two i’s) might be used to impersonate a user with the domain “agari.com” (with only one ‘i’). The second, and increasingly more common, type are generic domain names that appear authentic, such as “homerefi-source.online” or “adjust-refinance.online”. The criminal will then create multiple email accounts and associated display names to target specific individuals. These generic domains are less likely to be automatically identified as deceptive than look-alike domains and can be reused for attacks on many different organizations.
How did Traditional Email Gateway Fare--Not Too Well
At the root of the problem is that conventional email security solutions, such as Secure Email Gateways (SEG), Advanced Threat Protection (ATP) and Targeted Attack Protection (TAP) were designed to detect attacks by monitoring for malicious payloads, attachments, URLs and other forms of known bad behavior. BEC attacks evade these protections by impersonating trusted individuals, partners or brands, while avoiding the use of malicious payloads. In other words, they’re not trying to get you to click on something malicious; they’re trying to get you to act on a request because you trust the sender.
Agari Phishing Defense™ -- Enhancements for BEC
As BEC attacks remain unchecked by conventional email security, Agari today announced some groundbreaking enhancements to Agari Phishing Defense™:
- Agari Advanced Display Name Protection – Integrates a new machine learning model that integrates organizational data from Office 365 and Azure Active Directory to automatically block display name deception.
- Rapid DMARC – Automatically authenticates inbound email claiming to be from an organization’s internal domains to block spoofing attempts—regardless of whether the organization has published a DMARC policy.
- Search and Destroy - Microsoft Office 365 and Google G Suite administrators can rapidly search and delete emails that have already been delivered to user inboxes for breach prevention or copy emails for forensic analysis.
Agari Phishing Defense takes a revolutionary approach to identifying targeted email attacks using multiple patented machine learning models that integrate identity mapping, trust models and behavioral analytics linking the Internet’s infrastructure, DMARC authentication, organizational and individual data to detect and prevent identity deception. It’s the industry’s first email security solution that stops sophisticated targeted email attacks that are currently evading today’s security tools.