Phishing sites impersonating reputable organizations continue to represent the top online threat to businesses and their brands. In Q4, Financial Institutions were targeted most by credential theft phish, experiencing the largest share of malicious sites recorded since 2021, according to Fortra’s PhishLabs. Within the group, criminals capitalized on the broad customer bases and recognizable names associated with National Banks, attacking those businesses nearly three-quarters of the time.
Every quarter, PhishLabs examines hundreds of thousands of phishing and social media attacks targeting enterprises, their brands, and their employees. In this post, we break down the latest phishing activity and staging methods observed through our Suspicious Email Analysis solution.
Top Targeted Industries
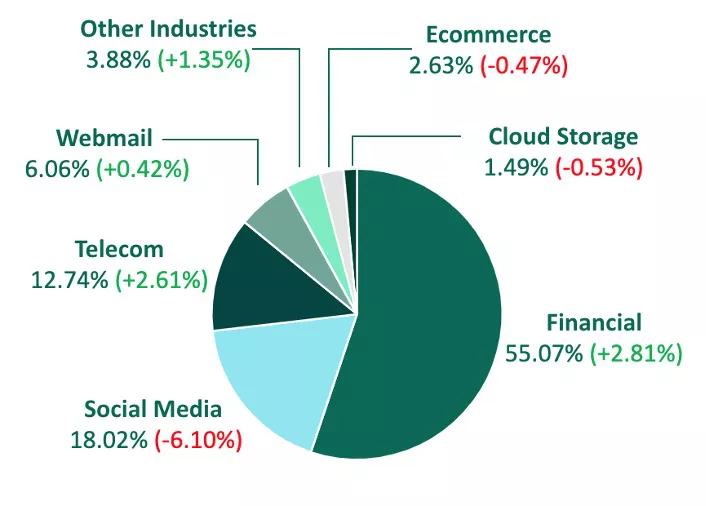
More than half of all phishing sites impersonated Financial Institutions in Q4, with actors using false branding to trick victims into disclosing login credentials and other sensitive information. Finance also experienced the largest increase among all industries, growing nearly 3% in share over Q3. Within the group, National Banks grew more than 15% of share, representing 71.30% of total phishing sites. National Banks are historically the top impersonated target among Financials.
Also falling under the Financial umbrella, attacks on Credit Unions grew, as bad actors continue to prey on smaller institutions that may be underprepared for advanced cyberattacks. Credit Unions experienced 11.16% of share of total Financial attack volume, making it the second most targeted subgroup. Regional Banks were targeted 9.33% of the time in Q4, after a drop in share of nearly 12%.
Social Media was the second most targeted industry by phish in Q4, making up 18.02% of total attack volume. This is despite experiencing the largest decrease among all other industries, dropping more than 6% in share from Q3.
Telecommunications remained in the third spot for the second consecutive quarter, despite increasing 2.61% of share over Q3. Telecoms contributed to 12.74% of total volume.
Other industries targeted include:
- Webmail 6.06%
- Other Industries (Including Gaming and Healthcare) 3.88%
- Ecommerce 2.63%
- Cloud Storage 1.49%
Credential Theft Staging Methods
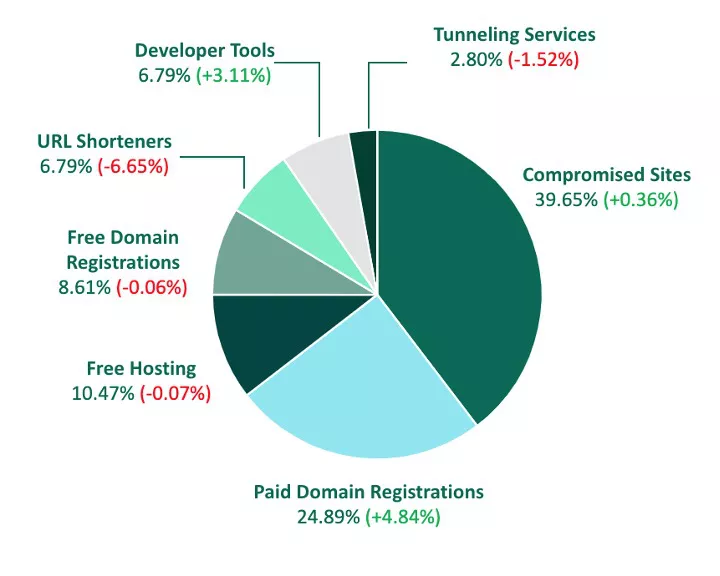
In Q4, three-quarters of phishing sites were staged through no-cost methods such as compromising an existing website or abusing a free tool or service. Compromising a legitimate site was the favorite among bad actors, increasing slightly from Q3 to represent just under 40% of total malicious activity.
Paid Domain Registrations experienced the largest increase in share among all methods, increasing nearly 5% in Q4. The share of bad actors using Paid Domain Registrations to stand up phishing sites has grown quarter over quarter this year and in Q4 accounted for its highest share since 2020.
Free tools and services were used to stand up phishing sites 35.46% of the time in Q4, with Free Hosting contributing to 10.47% of total staging volume. This is despite a slight decrease in share from Q3. Free Domain Registrations also experienced a decline in activity, accounting for 8.61% of share.
URL Shorteners and Developer Tools were both used by bad actors 6.79% of the time, despite each experiencing a decrease of 6.65% and increase of 3.11%, respectively.
Top Level Domain Abuse
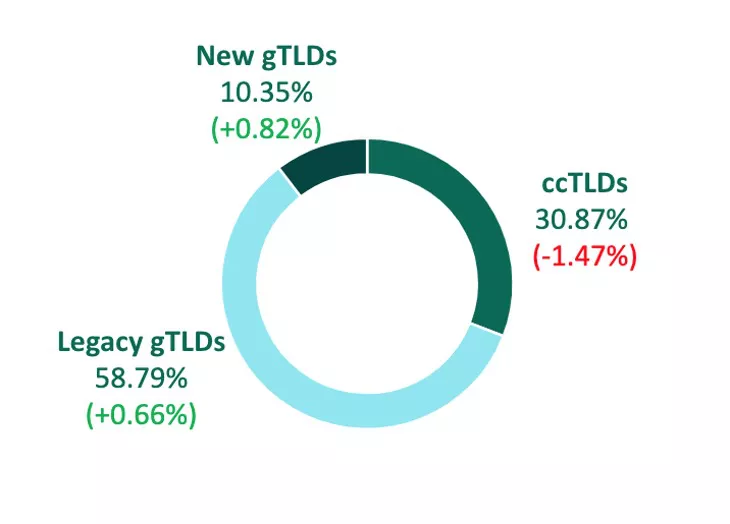
In Q4, threat actors increased their abuse of Legacy gTLDs to stage phishing sites, totaling nearly 60% of volume. Legacy gTLDs are historically the go-to top-level domain for criminals because they add legitimacy to attacks, in addition to making malicious activity harder to spot.
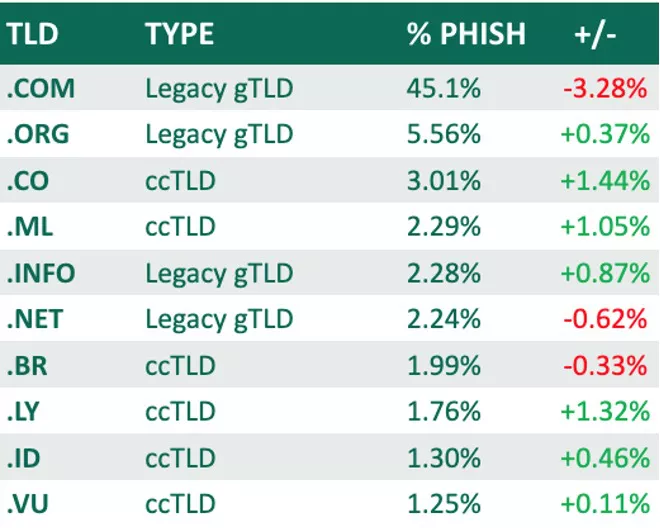
Legacy gTLD .com led the group, contributing to 45.10% of total abuse. This is a 3.28% decrease in share over Q3. Legacy gTLD .org was significantly lesser in count, but represented the second spot with 5.56% of abuse.
Country Code TLDs (ccTLDs) were used less as a whole in Q4, declining 1.47% in share from Q3 to represent just 30.87% of total share. Within the group, .co was abused most, making up just over 3% of incidents.
New gTLDs grew in count and share, contributing to 10.35% of total volume. This is an increase of .82% over Q3. Despite the growth, no New gTLDs were among the top ten for the second quarter in a row.
Phishing continues to represent the top online threat to organizations with criminals employing a variety of malicious tools to attack vulnerable or underprepared brands. In order to proactively stop attacks on your business, security teams must be knowledgeable of the services used to build sites impersonating your brand and monitor for suspicious activity that could lead to the creation of malicious infrastructures.
Learn how PhishLabs detects and disrupts phishing attacks here.
