A breach itself is bad enough, but the time it takes an organization to discover and contain that breach is where the majority of costs are incurred.
Just ask Marriott. Or Equifax. Or Under Armour. When a phishing attack occurs, it takes an average of 197 days before it's discovered—and an additional 69 days to contain it. In many cases, such as the recently discovered breach at Marriott, it can take as long as four years.
And the costs associated with breaches are staggering. According to Statista, for US-based companies in 2023, the average cost of a data breach was $9.48 million, up from $9.44 million U.S. dollars the previous year.
The time it takes to identify a data breach and contain a breach is one of the single most important factors to total costs. But while organizations able to contain a breach save an average of $1 million compared to those that can't, the average time between breach and containment is rapidly growing due to the increasing severity of attacks.
As it stands, 98% of all breaches start with a malicious email, with new attacks increasing by the day. But the tools used by most organizations to remediate successful attacks and any subsequent breaches are woefully out of date, even when email operations have migrated to the cloud. Even leading Security Orchestration and Automated Response (SOAR) products lack out-of-the-box, email-specific workflows that are necessary for fast and effective email phishing incident triage and response.
Enter Suspicious Email Analysis, the first and only purpose-built phishing incident response solution for post-delivery remediation within Microsoft Office 365 environments. By integrating with the cybersecurity industry's leading third-party forensic tools and automating investigation and remediation workflows, Suspicious Email Analysis helps organizations slash phishing response times by up to 95%.
All of which can save thousands of hours of SOC analyst time, contain breaches before damage is done, and be incredibly helpful to staying financially strong and away from the bad press cycle—especially when you consider the new threats that 2019 will bring.
Trouble is Just a Click Away
According to industry estimates, 90% of organizations report being hit by targeted email attacks this year, with 23% suffering financial damage.
Depending on the size of the company, average losses from a successful email scheme can run $1.6 million and up, even before any breaches. And it's about to get a whole lot worse. Today, it takes just four minutes for email attacks to land their first victim. Even with phishing awareness training, up to 48% of users open a malicious email, and 4% go on to fall for it.
With recent reports that cybercriminal organizations are increasingly targeting cloud email, things could get especially dicey for organizations operating within environments like O365, as stolen credentials can sometimes be the same ones used to access multiple cloud-connected services. Think Azure, SharePoint, OneDrive, and more.
According to the FBI, business losses from business email compromise (BEC) scams alone have topped $12 billion just since 2013. But that's really just the tip of the iceberg. Targeted phishing attacks in all their forms are now believed to account for up to 48% of all Internet-related business losses from cybercrime.
It's no wonder security operations center analysts are finding themselves outgunned—and current remediation tools and processes aren't helping matters.
Unintended Consequences
In a recent survey of 300+ companies conducted by Agari, companies reported that 98% of employees are trained to report phishing attacks, and often even have a convenient button or abuse inbox to forwarded suspicious messages to the security team. It's one of the best sources of breach threat intelligence, and it helps prevent and contain countless breaches by leveraging humans as the last line of defense.
But it can also have unintended consequences. In the survey, our researchers found that the average company responds to 23,053 employee-reported phishing incident reports per year, with more than half of them being false positives.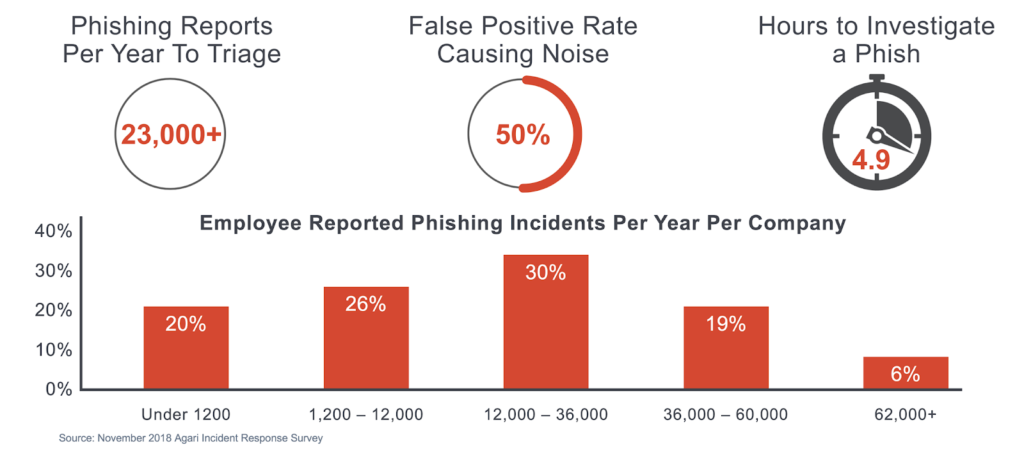
What's more, the manual process of investigating these incidents is frequently cited as the most time consuming a frustrating task facing the SOC team. Forensic analysis can entail a lot of cutting and pasting across multiple tools, and remediation often involves different groups within the same organization, many which lack effective data sharing capabilities.
As a result, responding to a legitimate phishing incident takes an average of nearly six hours. Even false positives are a time suck, taking an average of nearly five hours to resolve. It all adds up to as much as $253 spent responding to every phishing incident. That's nearly $4.3 million per year—and half of it wasted, even while successful breaches go undetected.
To put that into perspective, cybercriminals who are able to successfully breach a company can exfiltrate sensitive data within a handful of hours, while it'll likely be months before it's discovered. Considering that $7.9M average breach cost, every second counts—especially when you factor in regulatory fines and potential criminal prosecution.
In fact, cybercriminal organizations are increasingly stealing data and then turning around and extorting the company, threatening to reveal the breach. Many organizations are more than willing to pay the price in exchange for the breach never being reported.
That's where Agari comes in.
Automation is the Answer
Suspicious Email Analysis is a one-touch phishing incident response solution that seamlessly integrates with Microsoft Office 365 to dramatically accelerate triage, forensics, remediation, and breach containment.
When a phishing attack is reported, Suspicious Email Analysis automatically removes the reported email and discovers similar emails from the same campaign across all the inboxes in the organization. It also delivers a detailed impact analysis—including any phishing links, attachments, and sender forensics—enabling security teams to ignore false positives and focus their time and energy on the real deal. It even calculates the savings and efficiency of the phishing incident response process so that SOC teams can demonstrate the ROI of automating the process.
Now, breaches can be identified and contained in mere minutes instead of months, helping SOC analysts save time and helping their organizations avoid millions in potential losses.
By comparison, today's security orchestration, automation, and response (SOAR) tools can be expensive and complicated to implement, requiring custom code or additional headcount to integrate before they add any value. And even then, incident response times are only minimally improved relative to organizations without any SOAR tools at all.
Warning Signs Ahead
Over the last five years, at least 78,617 organizations have fallen prey to advanced email attacks that exploit the trusted identity of CFOs and other financial executives, according to Forbes.
But when you consider the 50,000 senior finance executives our researchers recently identified as targeted for forthcoming attacks, suddenly the threat landscape can look harrowing. Especially when you consider that those are targets for just one of the countless cyber criminal organizations with tens of thousands of their own targets in finance, HR, operations, and other corporate departments.
According to Dark Reading, a quarter of all IT and security leaders expect to experience a major breach in the next year, with 1 in 5 saying their organizations are more vulnerable to attack than they were in the past 12 months. Indeed, the targeted email attacks that can lead to such breaches are expected to be the #1 cybersecurity challenge organizations face in 2019.
All of which means finding new ways to accelerate phishing incident response times may prove critically important in the year ahead. An automated solution that is purpose-built for the cloud is the place to start.
To see how automating the process of phishing incident response can save your organization thousands of hours and millions of dollars per year, try the Suspicious Email Analysis ROI Calculator.