The scope of intelligence on underground marketplaces is vast and navigating the dark web in search of brand mentions and potential threats can be time-consuming and complex. In order to proactively defend against attacks and mitigate the threat of leaked information, organizations should consistently monitor marketplaces and forums for data pertaining to their brand. If questionable data is detected, understanding next steps is critical to minimizing risks to your brand, employees, and customers.
Below, we discuss the types of intelligence present on dark web spaces, and Fortra’s recommendations for data prioritization and subsequent application. With these recommendations, security teams will understand how to better identify and defend against attacks that originate in the dark web.
Types of Dark Web Intelligence
Full Credit Card Credential Intelligence
It is common to find leaked credit card information with full card numbers and associated data on the dark web. Compromised data of this nature can lead to swift monetary loss and long-term brand damage for organizations. Leaked credit card credentials should be a priority for security teams.
Credit card information available for capture may include:
- The expiration date on the card
- CVV number
- Other PII associated with the cardholder
Listings on the dark web that include full credit card numbers and other PII details should provide enough intelligence to determine who the affected customers are. Post-analysis, Fortra recommends security teams use this information to block affected consumer credit/debit cards and re-issue new cards to members.
Carding Marketplace Intelligence
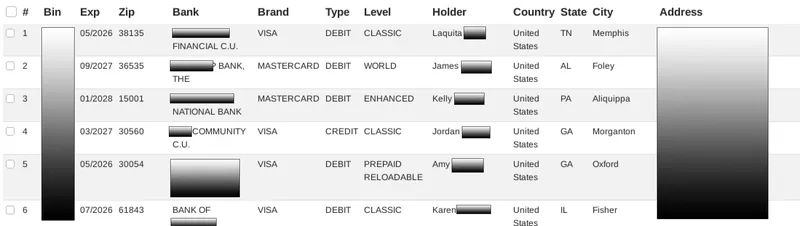
Carding Data on the Dark Web
Traditional Carding Marketplaces typically will not include full card numbers and have different data visualization when compared to full credit card intelligence. Instead, carding data is sold in two formats: credit card/PII data and dump data. Each type of carding data will offer distinct information that a security team or dark web service can scrape and ingest for further analysis.
Credit Card Data
The amount of PII that is visible on a credit card data marketplace will vary depending on the amount of PII the vendor is willing to display to potential buyers. Fortra recommends that security teams scrape any partial PII from the marketplace for review to determine if there is enough information to identify the customer.
Dump Data
Carding marketplaces selling dump data will typically have limited details available. For instance, customer PII data will not be visible. Security teams can best capture intelligence on these types of markets by tracking trending data including the BIN that is being targeted, the average cost of the data, and the amount of data for sale. Security teams can use dump data intelligence to determine if trends correspond to fraud levels they are currently experiencing. Similar to credit card marketplaces, security teams should scrape as much visible information on dump sites as possible and include that data within the created incident.
Account Marketplace Intelligence
Account-based marketplaces sell content that includes the visible PII of compromised individuals. The type of visible PII will vary based on the individual marketplace and the vendor selling the data. Common information security teams should capture, if available, includes:
- Account number
- Mobile phone identification number
- Last four digits on the credit card of the account
- Partial name/address
Oftentimes vendors on account-based marketplaces will show evidence of an account they have logged into through a screenshot. Vendors with minimal operational security acumen may leave customer PII visible on these print screen listings. Fortra recommends capturing and logging these with the corresponding account data for sale to identify the victim more easily.

Account Data on the Dark Web
Vendors on account marketplaces will also sell bank checks. These listings include screenshots of the check, which may expose customer PII.
Third-Party Leaks Intelligence
Email and password combinations resulting from database leaks, third-party breaches, or combo-lists are frequently found on dark web marketplaces and forums. Once sensitive information is detected and analyzed, Fortra recommends security teams notify their employees immediately. Password resets are highly encouraged, especially if the leaks are recent and could match current password management guidelines at the affected organization.
The nature of leaks persisting online for months and even years post-incident, combined with actor use of open bullet configuration tools designed to exploit username and password combinations, means affected individuals will remain at risk if they continue to use the same login.
Forum-Based Intelligence
Forums provide a space for threat actors to interact based on topics of interest, including hacking and fraud. Understanding which forums a threat actor operates within can provide a better understanding of the attack landscape and scope of compromised data a criminal is associated with. It is not uncommon for a threat actor to appear over multiple forums and post the same content.
Forum-based Intelligence on the Dark Web
A best practice for identifying information that pertains to your organization on dark web forums includes setting up keyword notifications. This will allow for the capture of content on posts when they relate to client-named assets. Gathering information based on keywords will allow for the investigation of data points such as:
- Threat actor name
- Threat actor contact information
- Links to other sites that the threat actor may operate
- Information from snippets of shared data the forum member may be previewing
Traditional Marketplace Intelligence
Traditional Markets are defined as dark web marketplaces that sell everything from drug paraphernalia to digital goods. These markets do not typically have visible PII present due to the nature of how they operate, meaning, threat actors will not divulge the details of the sensitive data or guides that they intend to make a profit off of. Security teams should focus on details around the threat actor, selling history, and where they advertise their goods/services. The following should be captured on traditional marketplaces, if possible:
- Threat actor name
- Information displayed on listing’s product description
- Shops they are associated with
- Vendor reviews
Any of this information may aid in determining the severity of the threat and how quickly an organization may want to act on it.
Traditional marketplaces are similar to forums in that it is common for the same threat actor to operate across multiple locations, often selling the same content. Understanding where the actor name operates, in addition to gathering any of the above information, will provide a better understanding of the threat landscape, the severity of the threat, and how quickly an organization may want to take action.
Infostealer Marketplace Intelligence
Infostealer marketplaces typically display intelligence that includes the domains that were compromised with each individual infostealer. Infostealers can cause significant damage to an organization, with a single infection capable of affecting a broad range of applications and systems. Infostealer marketplaces should be prioritized and scraped for relevant information pertaining to your organization.
Fortra recommends security teams examine the URL tied to your assets and those associated with the Infostealer for sale. This information can be used as contextual intelligence to identify whether an individual within the organization was compromised. It is important to identify whether URLs associated with your organization in the Infostealer are internal or external. Threat actor control of an internal URL can be particularly damaging, resulting in access to everything within that environment like project management tools and collaboration products.
Criminal activity on the dark web often goes unnoticed by security teams and can lead to damaging, yet preventable attacks. Visibility into dark web spaces and understanding what data pertains to your brand can help organizations stop the exploitation of compromised information in addition to removing the risk of future threats.
Learn how Fortra helps organizations gain visibility into threats on the dark web.
