Free domain registrations used to stage phishing sites have experienced a significant drop in activity, contributing to just under 2% of phishing abuse in Q1. Free domain registrations and other no-cost means of staging phishing infrastructures are historically a favorite of threat actors. While no-cost methods as a whole did make up the majority of abuse in Q1, the decline in free domains can be tied directly to the halting of free domains from provider Freenom, and could indicate a shift in criminal activity to other means of building malicious infrastructures.
Every quarter, Fortra’s PhishLabs examines hundreds of thousands of phishing attacks targeting enterprises and their brands. In this post, we break down the latest phishing activity, staging methods, and top-level domain abuse.
Top Targeted Industries
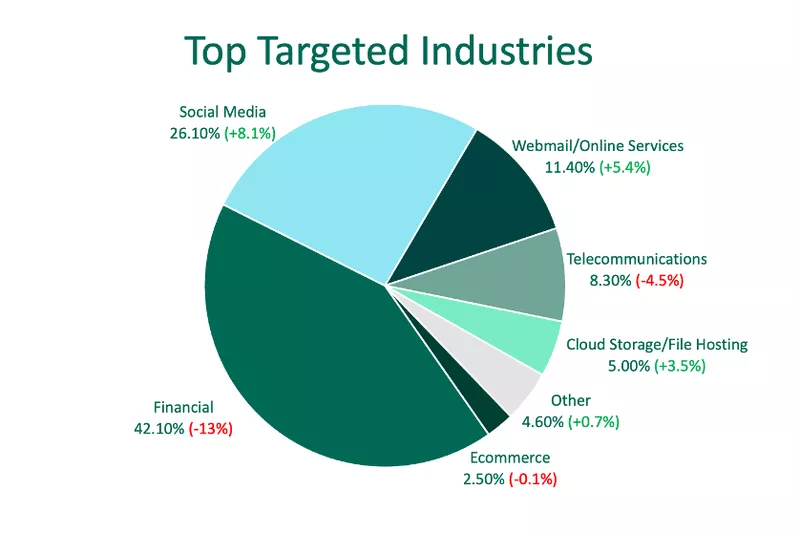
In Q1, phishing sites impersonating Financial Institutions experienced the largest decline in activity since 2020. Financials were targeted 13% less than Q4 2022, after seeing an increase in malicious activity for the previous two quarters. Despite this, Financial Institutions were still impersonated more than any other industry in Q1, representing more than 42% of total phishing site volume.
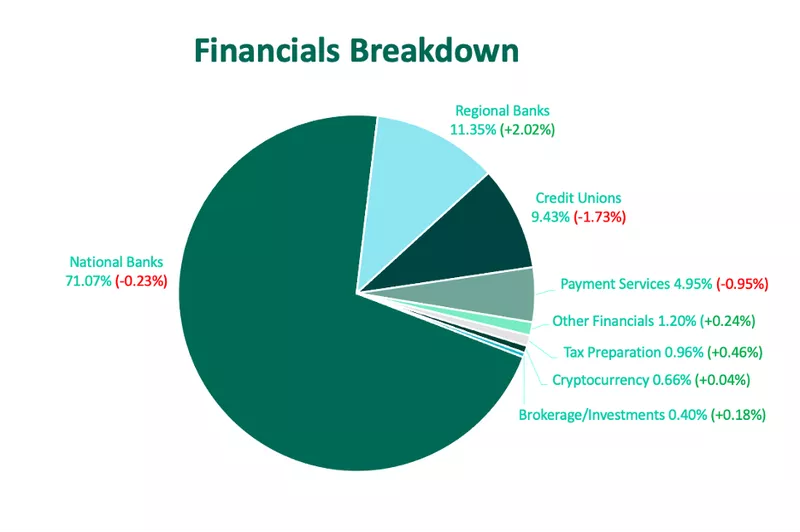
National Banks were the top targeted subset within the group, making up 71% of total volume in spite of experiencing a less than 1% decrease in activity. The share of volume of phishing sites impersonating Regional Banks climbed, making it the second most impersonated financial institution. In Q1, Regional Banks represented 11.4% of share of activity. The increase in phishing sites targeting the customers of Regional Banks may be attributed to money movement away from larger institutions in light of the Silicon Valley Bank seizure.
Also within the Financial category, Credit Unions and Payment Services were both impersonated less, after phishing site activity targeting these financial subsets declined. Credit Unions represented 9.4% of activity and Payment Services made up 5%.
The second most impersonated industry in Q1 was Social Media. Phishing sites targeting Social Media customers jumped 8.1% over Q4, representing more than a quarter of total abuse. This was the largest increase in activity among all industries.
Phishing activity targeting Webmail Providers experienced the second largest increase in activity in Q1, moving it up from the fourth spot in Q4. Webmail was impersonated 11.4%.
Additional industries targeted:
- Telecommunications 8.27% (-4.5%)
- Cloud Storage/File Hosting 5% (+3.5%)
- Other (including Healthcare and Insurance) 4.5% (+0.7%)
- Ecommerce 2.5% (0.1%)
Credential Theft Staging Methods
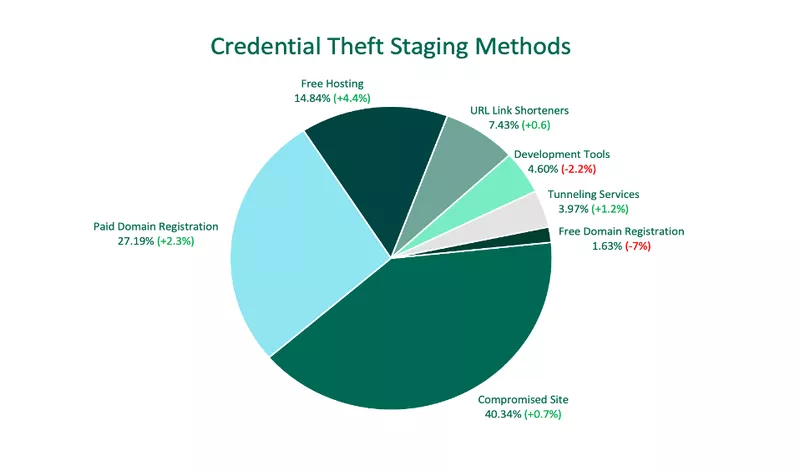
In Q1, nearly 73% of criminals used no-cost approaches, such as compromising an existing website or abusing a free service, to stage phishing sites. While this represents nearly three-quarters of all staging methods, no-cost solutions as a whole declined from Q4, after a significant decrease in Free Domain Registrations.
Compromising a website was the top staging method, making up more than 40% of all activity after a 0.7% increase. Paid Domain Registrations grew for the fifth consecutive quarter, contributing to 27.2% of staging methods. This is the highest share of volume of Paid Domain Registration abuse since 2020.
Free Hosting was the third most abused staging method, increasing 4.4% over Q4. Free Domain Registrations experienced a 7% drop in abuse, moving from the fourth spot to the seventh. URL Link Shorteners took its place at fourth, with 7.4% of staging volume.
Development Tools and Tunneling Services represented 4.6% and 3.9% of volume, respectively.
Top Level Domain Abuse
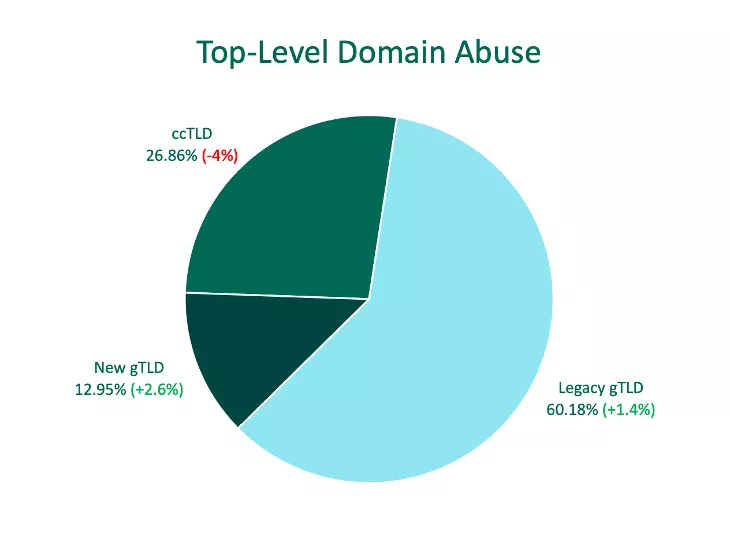
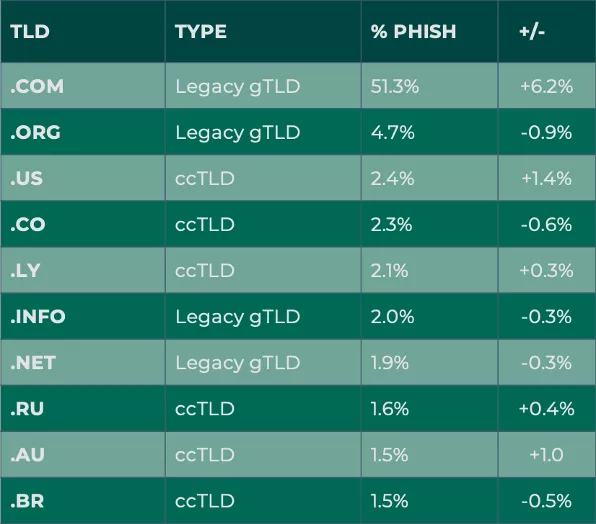
In Q1, criminals used Legacy Generic Top-Level Domains (gTLDs) 60.2% of the time to stage phishing sites. Legacy gTLDs abuse as a whole increased for the second consecutive quarter, growing 1.4% over Q4.
Legacy gTLD .com was the most abused TLD, contributing to 51.3% of total TLD volume. While .com is historically associated with the majority of phishing activity, the gap between it and the second most abused TLD was widened after a 6.2% increase in share over Q1.
Legacy gTLD .org was the second most abused TLD, representing 4.7% of share of attacks. Legacy gTLDs .info and .net made up the sixth and seventh spots, contributing to 2% and 1.9% of volume, respectively.
Country-Code TLDs (ccTLDs) declined more than 4% in Q1, with Freenom ccTLD .ml dropping completely from the top ten. Five free ccTLDs registered through Freenom have been a large contributor to past abuse. In March, Freenom halted the registration of all free domains and abuse associated with .ml has since plummeted.
Despite the decline, ccTLDs represented six of the top ten TLDs. Within the group, .us and .au abuse grew the most quarter over quarter, with .us jumping 1.4% over Q4 and .au demonstrating a 1% increase in activity.
There were no New gTLDs represented in the top ten.
The threat landscape continues to be volatile as criminals pivot to ensure the creation and success of phishing campaigns. Identifying the tools and methods most likely to be applied to create these campaigns is critical, so that actions can be taken to reduce or stop abuse. To achieve this, security teams should be knowledgeable of how and where their brand is being abused and how these infrastructures are created. Relationships with relevant service providers are key, and should be nurtured to enhance the detection of threats and speed of mitigation.
Learn how PhishLabs can help your organization protect against credential theft phishing and malicious domains.
