Awareness. Detection. Containment. Remediation. All necessary steps in the phishing incident response process for SOC analysts. Unfortunately, each of these steps takes time, and that time comes at a cost.
According to the Q3 2019 Email Fraud and Identity Deception Trends report from Agari, employees now report an average 33,108 phishing incidents to corporate SOC teams each year—an 18% increase over the last ninety days. This is on top of 25% increase over the previous quarter, when respondents to our survey estimated an average 23,063 reports annually.
What does this mean for SOC teams worldwide? More work, more time, and more resources. In addition to an increase in volume, the time it takes to triage, investigate, and remediate these reports continues to edge upward, to an average 7.31 hours for a true phish, and 6.13 hours for a false positive. 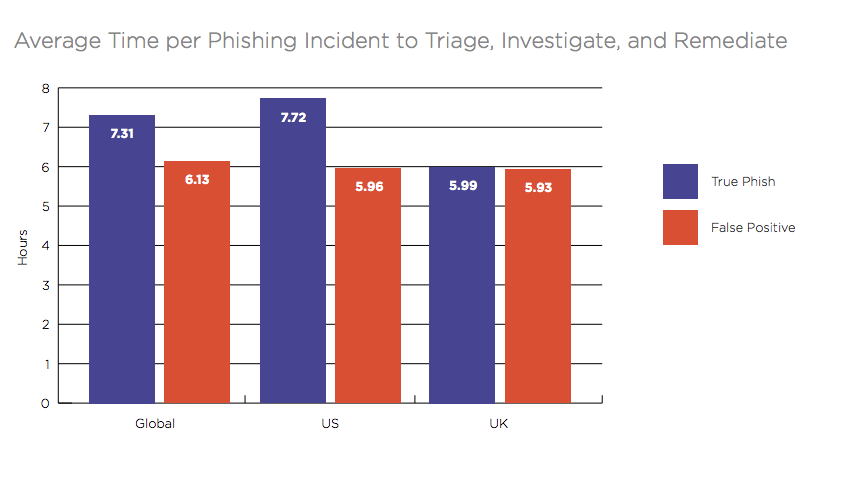 And it is not like organizations can simply drop this valuable function. After all, he cost of a successful phishing attack can lead to losses as much as $1.6 million per incident. If that attack results in a data breach, that cost can exceed $8 million according to new research from the Ponemon Institute.
And it is not like organizations can simply drop this valuable function. After all, he cost of a successful phishing attack can lead to losses as much as $1.6 million per incident. If that attack results in a data breach, that cost can exceed $8 million according to new research from the Ponemon Institute.
Unfortunately, it’s not just mega-corporations that are falling victim either... Ponemon estimates that 14% of all businesses will be hit by a data breach each year. Making matters worse? More than 90% of those start via email. After all, it only takes one click by an inexperienced user to start a process that can unravel an entire organization and leak the sensitive data of millions of people.
Email Security Can't Do It All
As an email security company, we’d know that legacy protections are unable to stop new and emerging threats. And while we’d like to believe that next-generation solutions can stop every threat out there, cybercriminals are always evolving their tactics as they look to stay one step ahead of security defenses. Even with a 99.99% catch rate for Agari customers, there is still that small chance that a malicious email will be delivered.
So how do organizations prevent users from clicking on malicious links or opening emails containing malware when it does reach the inbox? They train their employees on what to expect and then encourage them to report any messages they feel may be dangerous.
As part of our quarterly reports, ACID surveys SOC professionals at 280 large organizations to get a read on the state of incident response in a rapidly evolving email threat landscape. In addition to providing awareness training, this quarter’s survey finds that 98% of organizations give employees the ability to report suspected phishing emails. But all too often, employee-reported emails end up flooding SOC teams with more incidents to remediate than they can handle.
What’s more is that nearly 70% of those reported incidents are false positives—a 16% increase in ninety days. It is clear that the number of reported incidents will not decrease any time soon, which is good news for SOC analysts looking for employment and bad news for everyone else. While we did see a minor increase in the number of SOC analysts per organization, from 14.5 to 15.3, there is still a significant gap between the total number of analysts employed and the number of analysts needed to successfully remediate the sheer volume of reported incidents. 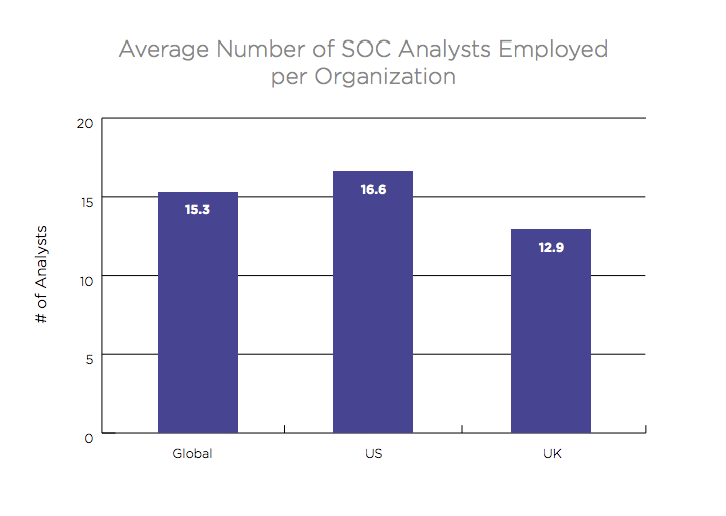
In fact, Agari research estimates that the average Security Operations Center needs 110 analysts working 40 hours a week to successfully remediate all incidents.
Moving Toward Automation
As part of our quarterly phishing incident response survey, we asked how much reducing the time required for phishing incident response would reduce breach risk. Respondents estimated an average 54% reduction, which would result in $654,545 saved annually.
To solve this exact problem, Suspicious Email Analysis provides a one-touch automation solution that has been shown to reduce the time need to respond to incidents by as much as 90% in real-world implementations. As a result, security teams can ignore false positives and focus on true phishing attempts—providing hours back in the day and increased safety for the organization.
Data breaches exposed more than 4 billion records in the first half of this year, and this number continues to grow by the minute. Especially for those industries typically targeted by attacks on their email and other sensitive systems, finding new ways to automate and accelerate phishing incident response time si more than ever. After all, your business—and your customers—depend on your security.
To learn more about trends in phishing incident response, download our datasheet.